Simple Explanation: What is AES-256 Bit Encryption
Convene uses AES-256 Bit Encryption, which is the best security available on the market, but you may not know what this means exactly. We’ve written a very simplified, helpful guide to explain what it is and why you should value it.
Data Encryption
Cybercriminals are always on the prowl, looking for weak links to break and crack. How can users, especially in this increasingly connected world, have complete assurance that their data is safe, wherever it may be located?
Encryption is one of the most common ways to protect sensitive data. Encryption works by taking plain text and converting it into cipher text, which is made up of seemingly random characters. Only those who have the special key can decrypt it. AES uses symmetric key encryption, which involves the use of only one secret key to cipher and decipher information.
The Advanced Encryption Standard (AES) is the first and only publicly accessible cipher approved by the US National Security Agency (NSA) for protecting top secret information. AES was first called Rijndael after its two developers, Belgian cryptographers Vincent Rijmen and Joan Daemen.
The following illustration shows how symmetric key encryption works:
Figure 1. Symmetric key encryption
AES-256, which has a key length of 256 bits, supports the largest bit size and is practically unbreakable by brute force based on current computing power, making it the strongest encryption standard. The following table shows that possible key combinations exponentially increase with the key size.
Key Size
Possible Combinations
Table 1. Key sizes and corresponding possible combinations to crack by brute force attack.
SecurEncrypt: Rock-Solid AES-256 Encryption on ATP Flash Storage Devices
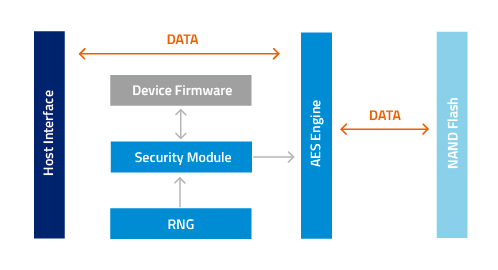
SecurStor-enabled ATP flash storage devices feature SecurEncrypt with AES-256 encryption to safeguard data against unauthorized access.
They make use of a hardware-based set of security modules and an AES engine. When the host writes data to the flash storage device, a Random Number Generator (RNG) generates the 256-bit symmetric cipher key, which is passed to the AES engine. The AES engine encrypts the plain text (source data) into cipher text (encrypted data) and sends it to the NAND flash for storage.
Inversely, if the host wants to retrieve data from the storage device, the AES engine decrypts the cipher text in the NAND flash, and then transmits data to the host as plain text. The encryption/decryption process is done at the flash level and does not require host intervention, so there is no performance degradation and data transfer does not slow down.
Figure 2. AES-256 encryption mechanism in ATP SecurEncrypt
ATP SecurStor: Protection Beyond Encryption
SecurEncrypt using AES-256 encryption is one component of ATP SecurStor, a multi-level security suite that protects data with a variety of options beyond data-at-rest encryption. Customers can choose from features that can be customized according to their application-specific requirements to guard against unauthorized access, illegal copying and other security threats to ensure data, OS and firmware integrity at all times.
For more information about SecurStor-enabled ATP flash products, visit the ATP website or contact an ATP Representative.
Simple Explanation: What is AES-256 Bit Encryption?
Convene uses AES-256 Bit Encryption, which is the best security available on the market, but you may not know what this means exactly. We’ve written a very simplified, helpful guide to explain what it is and why you should value it.
What Is Encryption?
Encryption is the process of encoding information by turning plaintext (what you write) into ciphertext (a coded version of the plaintext). At a glance, ciphertext appears to be random data, but to the trained eye it is clearly ciphertext. However, encryption means there are endless possibilities of what the plaintext version of the ciphertext might mean. How to decode the ciphertext depends on the type of code, or encryption, used to create the ciphertext.
What Is AES Encryption?
AES stands for Advanced Encryption Standard, which is a computer security standard designed to cryptographically store sensitive and top-secret information. AES encryption is a method of encryption which works through an approved 128-bit, 192-bit, or 256-bit symmetric encryption algorithm based off of the AES.
How Does AES Encryption Work?
- Key Expansion – at this stage, round keys are created to be used in the next stages of encryption. This uses Rijndael’s key schedule.
- Round Key Addition – A round key is the result of performing an operation on the previous round key and the data you want to encrypt. In this step, the initial round key is added to the divided data.
- Byte Substitution – this switches around the bytes based on the Rijndael S-Box substitution method.
- Row Shifting – the data divided into each row is moved to the left (one space for the second row, two for the third row, three for the fourth row).
- Column Mixing – Using a predetermined matrix, the data columns are multiplied and a new block of code is created.
- Round Key Addition – Another round key is applied to the columns.
This process is then repeated 13 times for the 256-bit Encryption, 11 times for 192-bit and 9 times for 128-bit.
Why Is AES 256-bit Encryption The Best On The Market?
The “bit” refers to the length of the key required to cipher and decipher the ciphertext. This means AES 256-bit is more encrypted than its 128-bit counterpart. The 128-bit encryption alone would take billions of years for a supercomputer to crack , so the AES 256-bit is practically impenetrable.
This is why it is trusted by government agencies across the world. It is a legal requirement for a company’s cybersecurity to be encrypted with AES 256-bit to work with NASA!
Why Convene Uses AES 256-bit Encryption?
Convene uses AES 256-bit encryption because your data is important to us. We want you to feel as secure and comfortable as possible uploading your sensitive data into our Document Library.
Our security measures go beyond encryption, as we are also CMMI-Level 5 certified, meaning we are approved to work with any US Government Agency. If you would like to learn more about our advanced security features, please visit our FAQs page here .
Convene is an award-winning Board Portal designed to digitise and streamline your meeting processes from start-to-finish. Our comprehensive features include:
- A Document Library with role-based access to ensure your sensitive documents are protected.
- A built-in Audit Trail , so you can be sure you are compliant with all regulations.
- Integrated Video Conferencing , so you can make the switch from remote to hybrid working seamlessly, whilst still viewing your Board Pack all on one screen.
- Surveys , with the option for anonymity, so you can be sure you are aware of your employees’ opinions.
- Accessibility Features , including text-to-voice, which makes us the leading accessible Board Portal.
Convene is more than just its features, our customers also trust us to keep their data safe. Our certified security will ensure your confidential data is protected at every stage of project delivery. This includes, but is not limited to:
- AES 256-bit encryption and secure storage
- Granular access controls and role-based permissions
- Document security and digital rights management
- Device security
- Secure user authentication
- Security governance
- 24/7 intrusion detection and prevention
Our software also now comes as an integration with Microsoft Teams , which provides the benefits of both Teams collaboration and a Board Portal.
If you’d like to learn more about how Convene can help your organisation achieve better governance , please do not hesitate to book a free demo today!
Everything You Need to Know About AES-256 Encryption
When national security is involved, strong encryption measures are taken to protect data. The Advanced Encryption Standard (AES), originally adopted by the U.S. federal government, has evolved to become an industry standard for securing data and needs to be part of every organization’s integrated risk management strategy. AES comes in 128-bit, 192-bit, and 256-bit implementations, with the 256-bit implementation being the most secure. This article explains what AES-256 encryption entails, how it works, and how secure it is. It also discusses how double encryption bolsters security and protects private content from malicious cyberattacks.
What Is AES-256 Encryption?
The Advanced Encryption Standard (AES) is a symmetric block cipher that the U.S. government selects to protect classified data. AES-256 encryption uses the 256-bit key length to encrypt as well as decrypt a block of messages. There are 14 rounds of 256-bit keys, with each round consisting of processing steps that entail substitution, transposition, and mixing plaintext to transform it into ciphertext.
How Does AES-256 Encrypt Your Data?
Since AES is a symmetric key cipher, it uses the same secret key for both encryption and decryption. This means that both the sender and receiver of the data in question need a copy of the secret key. Symmetric keys are better suited for internal transfers, unlike asymmetric keys, which are best for external transfers. Symmetric key ciphers, such as AES, are faster and more efficient to run since they require less computational power than asymmetric key algorithms.
Additionally, AES uses block ciphers, where the plaintext is divided into sections called blocks. AES uses a 128-bit block size, whereby data is divided into 4-by-4 arrays that contain 16 bytes. Each byte contains 8 bits, with the total bits in every block being 128. In AES, the size of encrypted data remains the same. This means that 128 bits of plaintext yield 128 bits of ciphertext.
In all encryption, each unit of data is replaced by a different unit according to the security key used. AES is a substitution-permutation network that uses a key expansion process where the initial key is used to come up with new keys called round keys. The round keys are generated over multiple rounds of modification. Each round makes it harder to break the encryption. The AES-256 encryption uses 14 such rounds.
AES works by having the initial key added to a block using an exclusive or (XOR) cipher. This is an operation that is built into processor hardware. In the block, each byte of data is substituted with another, following a predetermined table. The rows of the 4-by-4 array are shifted, with the bytes in the second row being moved one space to the left. Bytes in the third row are moved two spaces, and the ones in the fourth row moved three spaces. The columns are then mixed, combining the four bytes in each column, and the round key is added to the block. The process is repeated for each round, yielding a ciphertext that is completely different from the plaintext.
This encryption algorithm features the following advantages:
- Using a different key for every round yields a much more complex result
- Byte substitution modifies the data in a nonlinear way, thus hiding the relationship between plaintext and ciphertext.
- Shifting rows and mixing columns diffuses data, thus transposing bytes. This further complicates the encryption.
The result of these processes is secure data exchange. The same process is repeated in reverse for the decryption process.
AES-256 Decryption Process
AES ciphertexts can be restored to the initial state by the help of inverse encryption. As we have seen above, the AES uses symmetric encryption, meaning that the secret key used for encryption is the same one used for decryption.
In the case of AES-256 decryption, the process begins with the inverse round key. The algorithm then reverses every action, namely: shifting rows, byte substitution, and column mixing, until it deciphers the original message.
Is AES-256 Encryption Crackable?
AES-256 encryption is virtually uncrackable using any brute-force method. It would take millions of years to break it using the current computing technology and capabilities.
However, no encryption standard or system is completely secure. In 2009, a cryptanalysis discovered a possible related-key attack. In such an attack, attackers try to crack a cipher by observing how it operates by using different keys. Luckily, experts have since concluded that such a threat can only happen in AES systems that are not configured correctly.
Since it is almost impossible to crack the AES cipher using a brute-force method, the main risk to this standard is side-channel attacks. In these attacks, attackers try to pick up information leaking from a system to discover how the encryption algorithms work. However, this can only happen in non-secure systems. A sound AES-256 implementation safeguards a system from side-channel attacks.
Much as the AES-256 standard is very secure, a vulnerable system can lead to an attacker gaining the secret key itself. A zero-trust security approach ensures that organizations trust and verify digital communications that exchange data. Further, organizations must take a defense-in-depth approach to security that employs multi-factor authentication, hardened infrastructure, and proactive and integrated incident response. Incoming sensitive content communications must be verified using data loss prevention, antivirus, and anti-malware capabilities, while outbound sensitive content communications should also leverage data loss prevention. These capabilities should be involved in any cyber risk management approach.
The open nature of the AES-256 standard makes it one of the most secure encryption standards. Cybersecurity experts are on the constant lookout for potential vulnerabilities, and when a vulnerability is discovered, users are notified and action is taken to address the issue.
Examples of Where AES-256 Encryption Is Currently Being Used
Following are some of the use cases for AES-256 encryption:
- U.S. government entities such as the NSA, the military, and many other entities use AES encryption for secure communication and storage of data.
- Many devices, applications, and networks today use AES-256 encryption to protect data at rest and in transit. Many SSDs employ AES encryption algorithms.
- All data stored in the Google Cloud is encrypted using the AES-256 standard by default.
- AWS, Oracle, and IBM also use the AES-256 encryption standard.
- WhatsApp messages are encrypted using the AES-256 encryption standard.
AES-256 for Sensitive Content Communications
Organizations must protect and keep data private when it is at rest and in motion. Encryption must be employed in both instances. For data at rest, AES-256 encryption is often the best option, whereas transport layer security (TLS) encryption creates secure sockets layer (SSL) tunnels to protect private content. Private data that requires encryption includes personally identifiable information (PII), protected health information (PHI), financial records, and corporate strategic product, marketing, and sales plans.
Kiteworks encrypts each piece of content with a unique, strong key at the file level and with a different strong key at the disk-level volume. This ensures that each file is double encrypted. Further, file keys, volume keys, and other intermediate keys are encrypted when stored.
Kiteworks uses a passphrase entered by an administrator to generate a super key it uses in the encryption of all stored keys. Thus, when an administrator rotates the passphrase on a regular basis, as recommended, the process is quick and efficient because only the keys need to be re-encrypted and not all content.
Those wanting more detail about Kiteworks’ key encryption approach across different sensitive content communication channels—email, file sharing, managed file transfer, web forms, and application programming interfaces (APIs)—can schedule a custom demo tailored to their environment.
SUBSCRIBE
Get email updates with our latest blogs news