What are the Five Eyes, Nine Eyes and Fourteen Eyes Intelligences
FIORC was created in the spirit of the existing Five Eyes partnership, the intelligence alliance comprising Australia, Canada, New Zealand, the United Kingdom, and the United States.
Five Eyes, Nine Eyes, 14 Eyes (What to Avoid in 2023)

As awareness of global surveillance grows, more people are looking for information about the Five Eyes, Nine Eyes, and 14 Eyes surveillance alliances. This guide is regularly updated with new information and gives you everything you need to know right now. We also list recommended privacy services (Email, VPN, and Private Search Engines) that are outside of the Five Eyes.
The terms “Five Eyes” (a.k.a. FVEY), “Nine Eyes”, and “14 Eyes” often appear in the privacy community, especially when discussing VPNs and other privacy tools. So what are these organizations?
In short, these are international surveillance alliances representing various countries around the world. These alliances work together to collect and share mass surveillance data with each other. Beginning with the UKUSA agreement and Five Eyes intelligence sharing, these networks have been spying on people for decades, with established policies going back to World War II, as we’ll discuss below.
The government agencies behind these efforts often work with internet service providers and other large tech companies to tap key infrastructure for the collection of private data (data surveillance). This turns your internet service provider, for example, into a local adversary that is spying on you for state agencies. And no, this is not a theory.
Your internet service provider is logging everything!
In 2021, the US Federal Trade Commission published a 74 page report documenting how internet service providers are collecting vast amounts of private data from their customers and then selling the data to third parties. We examined this report, the implications, and some solutions in our article on internet service providers logging browsing activity.
These practices are well-documented in the PRISM surveillance documents and also the infamous Room 641a example with AT&T and the NSA. Fortunately, there are some simple solutions to keep your data safe that we’ll cover below.
In this guide, we’ll explain all the different “X” eyes surveillance alliances and why this topic is important when choosing privacy tools. Here’s what we’ll cover:
- Five Eyes
- Six Eyes?
- Nine Eyes
- 14 Eyes
- NSA and GCHQ cooperation within 5 Eyes
- ECHELON surveillance system
- The importance of avoiding 5 Eyes
- Recommended privacy services that are outside of the 5 Eyes, including
- Secure email services
- VPNs
- Private search engines
So let’s get started!
Five Eyes
The Five Eyes (FVEY) surveillance alliance includes the following countries:
- Australia
- Canada
- New Zealand
- United Kingdom
- United States
The history of this alliance goes back to WWII and the UKUSA Agreement, which was officially enacted after the war in 1946. This agreement formalized a partnership between the United Kingdom and the United States for gathering and sharing intelligence data.
The partnership continued throughout the Cold War and has only strengthened since the “Global War on Terror” kicked off in the early 2000s. Edward Snowden brought renewed focus to the Five Eyes surveillance alliance in 2013 when he exposed the surveillance activities of the US government and its allies.
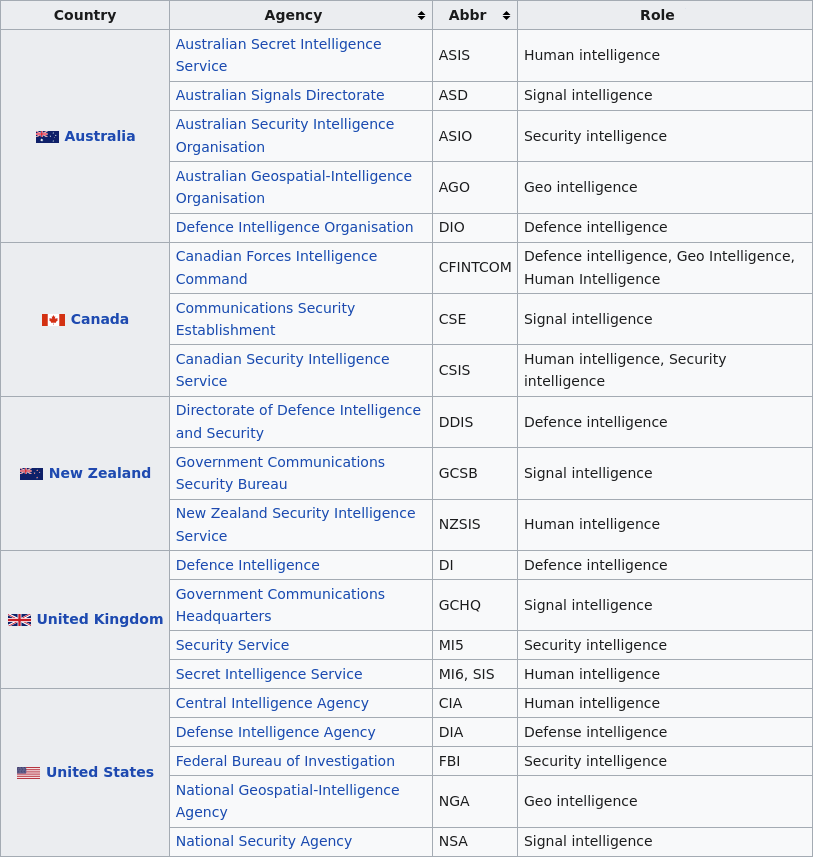
Below are the different “5 Eyes” surveillance agencies working together to collect and record your activities:
In addition to these national organizations, there exists the Five Eyes Intelligence Oversight and Review Council (FIORC). According to the FIORC web page on the US Director of National Intelligence website,
FIORC was created in the spirit of the existing Five Eyes partnership, the intelligence alliance comprising Australia, Canada, New Zealand, the United Kingdom, and the United States.
It further states that,
The Council members exchange views on subjects of mutual interest and concern; compare best practices in review and oversight methodology; explore areas where cooperation on reviews and the sharing of results is permitted where appropriate; encourage transparency to the largest extent possible to enhance public trust; and maintain contact with political offices, oversight and review committees, and non-Five Eyes countries as appropriate.
The following non-political intelligence oversight, review, and security entities of the Five Eyes countries are part of FIORC:
- The Office of the Inspector-General of Intelligence and Security of Australia
- The National Security and Intelligence Review Agency of Canada
- The Office of the Intelligence Commissioner of Canada
- The Commissioner of Intelligence Warrants and the Office of the Inspector-General of Intelligence and Security of New Zealand
- The Investigatory Powers Commissioner’s Office of the United Kingdom
- The Office of the Inspector General of the Intelligence Community of the United States
You can get more information about FIORC, including a copy of the organization’s charter, here.
It is no surprise that some of the Five Eyes countries listed above are also the worst abusers of online privacy:
- United Kingdom – Since the passage of the Investigatory Powers Act in 2016, internet service providers and telecoms have been recording browsing history, connection times, and text messages. The data is stored for two years and is available to UK government agencies and their partners without any warrant.
- United States – The US government has been implementing Orwellian mass surveillance collection methods with the help of large telecoms and internet service providers (see the PRISM program). In March 2017, internet service providers were given the legal authority to record user activity and sell this to third parties. Of course, internet providers have been collecting data on their customers for many years, long before this law passed in 2017.
- Australia – Australia has also implemented sweeping data retention laws similar to the United Kingdom.
Broad authority among 5 Eyes countries
Whether it is the NSA in the United States or the GCHQ in the United Kingdom, the “5 Eyes” is home to the most powerful surveillance agencies in the world. A privacy company sharing a jurisdiction with entities like these is just asking for trouble.
In particular, the intelligence agencies in the Five Eyes countries have tremendous authority to force companies to record and hand over data. In the United States, the Patriot Act ushered in a new level of power for federal data collection, especially through the use of National Security Letters. We see these same trends unfolding in the UK, Australia, and other locations as well.
Six Eyes?
In an August 2020 Nikkei interview, Japanese Defense Minister Taro Kono discussed tighter cooperation with Five Eyes, telling an interviewer that,
These countries share the same values. Japan can get closer [to the alliance] even to the extent of it being called the ‘Six Eyes‘.
Reportedly both the United States and United Kingdom have shown some interest in this, perhaps in response to the growing risks of armed conflict with China. While this appears to be just talk right now, we’ll keep an eye on the situation and update our articles as necessary.
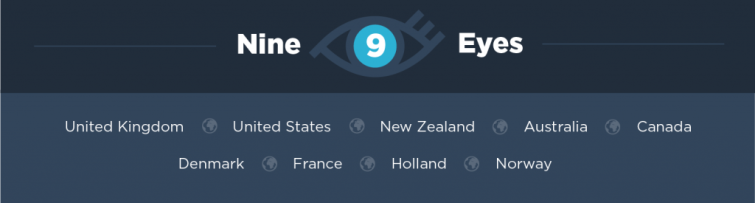
Nine Eyes
The Nine Eyes countries include:
- 5 Eyes countries +
- Denmark
- France
- Netherlands
- Norway
The existence of the Nine Eyes alliance is referenced in various sources online and became well-known following the Snowden revelations in 2013. It is just an extension of the Five Eyes alliance with similar cooperation to collect and share mass surveillance data.
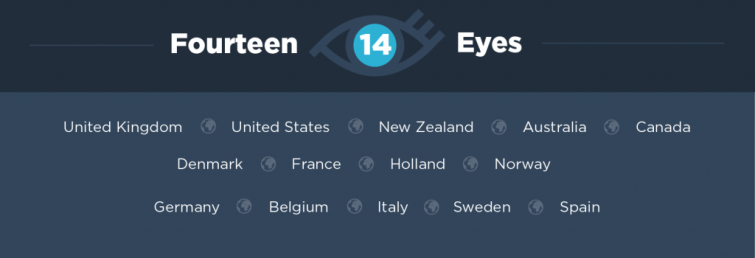
14 Eyes
The 14 Eyes surveillance countries include:
- 9 Eyes countries +
- Germany
- Belgium
- Italy
- Sweden
- Spain
As before, the original surveillance agreement was extended to these other countries. The official name of this group of countries is referred to as SIGINT Seniors Europe (SSEUR).
NSA and GCHQ cooperation within 5 Eyes
Various government document releases, which have come out through official FOIA channels, reveal the close relationship between the NSA and GCHQ. Being the two most powerful surveillance entities in the world, with historical ties, it is no surprise that they work closely together.
A top-secret NSA document from 1985, which was released in 2018 via a FOIA request, reveals that this close cooperation continues today, based on the broadly-written UKUSA Agreement:
The UKUSA Agreement, dated 5 March 1946, has twelve short paragraphs and was so generally written that, with the exception of a few proper nouns, no changes to it have been made. It was signed by a UK representative of the London Signals Intelligence Board and the U.S. Senior Member of the State-Army-Navy Communications Intelligence Board (a predecessor organization which evolved to be the present National foreign Intelligence Board). The principles remain intact, allowing for a full and interdependent partnership. In effect, the basic agreement allows for the exchange of all COMINT results including end product and pertinent collateral data from each pattern for targets worldwide, unless specifically excluded from the agreement at the request of either party.
Another top-secret NSA document from 1997 (officially released in 2018) further elaborates on the close cooperation between the NSA and GCHQ:
Some GCHQ [redacted] exist solely to satisfy NSA tasking. NSA and GCHQ jointly address collection plans to reduce duplication and maximize coverage through joint sites and cross-tasking, despite site closures.
With the reference to “joint sites” above, it’s important to discuss ECHELON.
ECHELON surveillance system
ECHELON is a network of spy stations utilized by Five Eyes countries for large-scale espionage and data collection.
The Guardian described ECHELON as a a global network of electronic spy stations that can eavesdrop on telephones, faxes and computers. It can even track bank accounts. This information is stored in Echelon computers, which can keep millions of records on individuals.
Officially, however, Echelon doesn’t exist. Although evidence of Echelon has been growing since the mid-1990s, America flatly denies that it exists, while the UK government’s responses to questions about the system remain evasive.
Despite these denials, there have been whistleblowers who have confirmed what’s going on behind the scenes. Both Perry Fellwock and Margaret Newsham came forward to document various aspects of ECHELON to the public.
Avoid the 5 Eyes
While there are privacy concerns with the other countries in the greater 14 Eyes alliances, the big one to avoid is the Five Eyes. Therefore, when data security is critical, simply avoid the Five Eyes: US, UK, Canada, Australia, and New Zealand
Some people say concerns about these surveillance jurisdictions are overblown or misguided, and that it really doesn’t matter. You often hear this argument from VPN companies (and their marketers) that are based in the US or Canada, for example. This line of thinking is misinformed and ignores reality.
There are many examples that prove the real-world risks associated with privacy-focused companies operating in Five Eyes jurisdictions. Here are just a few that we’ve discussed before on RestorePrivacy over the years:
- Riseup, a Seattle-based VPN and email service, was forced to collect user data for government agents and was also hit with a “gag order” to prevent any disclosure to their users. (They also could not update their warrant canary.)
- Lavabit, another US-based email service, was forced to provide encryption keys and full access to user emails. Rather than comply, the owner decided to shut down Lavabit email.
- IPVanish, a US-based VPN service, was forced to collect user data for an FBI criminal investigation. This all transpired while IPVanish was claiming to be a “no logs VPN” — and they could not alert their users to what was happening. (See the IPVanish logs case.)
- HideMyAss, a UK VPN service was also ordered by a court to collect user data and hand this over to authorities for a criminal investigation. News about this came out after-the-fact.
VPNs operating in the US, and by extension all of their users, can also be the targets of lawsuits involving copyright infringement. A recent court case involved TorGuard VPN, which was forced to block torrenting on all US servers as part of the settlement agreement. This is why we recommend avoiding US-based VPNs when using a VPN for torrenting.
These are just a few cases that have publicly come to light, but you can be sure there are other examples we don’t know even about.
Secret demands for user data + gag orders = privacy nightmare
As we can see from these examples, when authorities compel businesses to collect and hand over data, they usually serve them with a gag order as well. This is done through National Security Letters and it prevents the business from disclosing any information to their customers.
These laws basically give the government the authority to compel a legitimate privacy-focused company to become a data collection tool for state agencies, without any warning or notification. Even warrant canaries are ineffective in places like the United States.
Ignoring the jurisdiction of a privacy-focused business is foolish and ignores these well-documented risks.
Recommended privacy services (in good jurisdictions)
One of the main purposes of RestorePrivacy is to test, research, and recommend privacy and security tools that meet specific criteria. Given our emphasis on data security and trust, jurisdiction is a key factor we consider.
In terms of jurisdiction, our main concern is avoiding Five Eyes countries. After all, some of the 9 and 14 Eyes countries do indeed have strong privacy laws, especially in comparison to the US and UK.
Secure email outside Five Eyes
Using a secure and private email service in a safe jurisdiction is a no-brainer. Consider this:
- Yahoo was found to be scanning emails in real-time for US surveillance agencies.
- Gmail was found to be giving third parties full access to user emails and also tracking all purchases via receipts in your inbox.
- Advertisers were allowed to scanYahoo and AOL accounts to “identify and segment potential customers by picking up on contextual buying signals, and past purchases.”
Alternatives – Here are some of our favorite secure email services that we tested:
- Mailfence review (Belgium)
- Tutanota review (Germany)
- ProtonMail review (Switzerland)
- Mailbox.org review (Germany)
- Posteo review (Germany)
- Runbox review (Norway)
- Countermail website (Sweden)
- KolabNow website (Switzerland)
- Startmail website (The Netherlands)
Best VPNs outside the Five Eyes
As mentioned above, internet service providers are actively collecting data for government agencies around the world. They do this by either actively snooping on connections or simply recording all your DNS requests. Additionally, advertisers and other third-parties will track and record your online activity that is tied to your unique IP address.
A good VPN service is absolutely essential for basic online privacy, especially when ISPs are logging everything. A VPN encrypts all your traffic between your computer/device and the VPN server you are connected to. Not only does this make your traffic and online activities completely unreadable to your ISP and other third parties, it also hides your IP address and location.
Here are the best VPN services that are located outside of the Five Eyes countries:
- NordVPN (Panama) – see our NordVPN review
> Grab the 68% Off NordVPN Coupon - Surfshark (The Netherlands) – see our Surfshark VPN review
- ExpressVPN (British Virgin Islands) – see our ExpressVPN review
- VPN.ac (Romania) – see our VPN.ac review
- VyprVPN (Switzerland) – see our VyprVPN review
- Perfect Privacy (Switzerland) – see our Perfect Privacy review
- OVPN (Sweden) – see our OVPN review
- TrustZone VPN (Seychelles) – see our TrustZone VPN review
- ProtonVPN (Switzerland) – see our ProtonVPN review
We do our best to keep the VPN reviews updated to reflect the latest test results, company changes, and new features.
Note: Some people are worried about logs and data collection with VPNs. Fortunately, there are a few verified no logs VPNs that have undergone independent audits to confirm their no-logs policies:
- NordVPN was audited to PwC AG in Zurich, Switzerland to confirm essential privacy-protection measures and the no-logs policy. NordVPN has committed to annual third-party audits, while also undergoing independent security audits and penetration testing carried out by Versprite.
- ExpressVPN has been audited twice by PwC to verify its no-logs policy. Additionally, ExpressVPN has passed security audits conducted by Cure53.
- VyprVPN underwent a no-logs audit carried out by Leviathan Security a few years ago.
Private search engines outside Five Eyes
Most of the big search engines, such as Google, record all your search queries and then link this to your identity and data profile, so you can be hit with targeted ads. Unless you want to give Google and its partners all your search activities, consider using alternatives.
Here are some private search engines you may want to consider:
There are a few search engines based in Five Eyes countries that we still recommend. These include:
- DuckDuckGo (United States)
- Mojeek (United Kingdom)
- Brave Search (United States)
For additional tools and tips, see the main privacy tools page.
Trust and jurisdiction
In the end, jurisdiction is just one of many factors to consider when selecting reliable privacy tools for your unique needs. How much it matters depends on your own circumstances, particularly your threat model and the types of adversaries you are looking to protect yourself against.
For those seeking higher levels of privacy and security, jurisdiction is indeed important, especially when you consider the growing power of governments to force companies to hand over data and log users.
Trust is also a major factor you should consider. After all, a VPN can operate in a “good” overseas jurisdiction, yet still lie to customers and provide data to government agencies. Take for example PureVPN, a “no logs” service based in Hong Kong that gave US authorities connection logs for a criminal case.
This is where trust is key. Fortunately, to strengthen trust, more privacy-focused businesses are undergoing independent audits and third-party verifications. In addition to the VPN audits we mentioned above, we also see this trend with password managers and occasionally with secure email services.
Are these the only international intelligence alliances?
Most definitely not. In addition to the Five Eyes (FVEY), Nine Eyes, and 14 Eyes (SIGINT Seniors Europe), there are other organizations we know of. Examples include the SIGINT Seniors Pacific, the Quadrilateral Security Dialog (the Quad), and the Club de Berne. There may also be other such organizations that we still don’t know about.
Will Japan become a “Sixth Eye”?
Japan has publicly suggested that they would like to work more closely with the Five Eyes, and perhaps some day become a Sixth Eye. As of now it appears to be only talk, but growing tension between Japan and China seems to be moving Japan toward ever stronger connections with the Five Eyes countries. Only time will tell if we’ll be talking about Six Eyes instead of Five Eyes soon.
Conclusion: Use services operating in safe jurisdictions for 2023
The Five Eyes is the most powerful surveillance alliance in the world. While it arguably works well to protect its member countries (USA, UK, Canada, Australia, and New Zealand), it makes those countries less than ideal jurisdictions for pro-privacy companies and products.
Ultimately, we also need to acknowledge that everyone has different needs, use cases, and threat models. This means that selecting products and services is a very subjective matter, and only you can find the best fit for your needs.
Good luck and stay safe!
This guide on the 5 Eyes, 9 Eyes, and 14 Eyes was revised and updated on January 3, 2023.
About Sven Taylor
Sven Taylor is the lead editor and founder of Restore Privacy, a digital privacy advocacy group. With a passion for digital privacy and accessible information, he created RestorePrivacy to provide you with honest, useful, and up-to-date information about online privacy, security, and related topics.
Reader Interactions
Comments
- kcs August 22, 2023
Duck Duck GO isnt safe or secure. there are back end ties that are very shady , how can you have them in this list?
- IT September 16, 2023
please define “very shady back end ties”
John August 10, 2023
What are the Chinese, Russian, or Iranian alternatives? Clearly the only countries that might be trusted.
- IT September 16, 2023
No, it’s not clear at all: There is nothing obvious or logical about your conclusion. How many countries exist, in your estimation? And what are you going to do when 90 percent of the world’s internet traffic is sold?
https://www.vice.com/en/article/y3pnkw/us-military-bought-mass-monitoring-augury-team-cymru-browsing-email-dataWatchingtheweasels August 3, 2023
Are NordVPN (with its own page on the World Economic Forum’s homepage) and ExpressVPN (with its purchase by Kape seen here: https://www.timesofisrael.com/israeli-cybersecurity-firm-buys-expressvpn-for-close-to-1b/) still reliable guards of our privacy? Yes they are large, have a lot of servers, and have polished user interfaces but these aren’t comforting ties for companies you do business with to protect cyberprivacy.
B July 27, 2023
I’m looking to start using a Gmail and G-suite alternative. My question is the following: If I start using ProtonMail does it make sense to also buy a subscription to SurfShark, or should I just use ProtonVPN?
- Sven Taylor July 27, 2023
What are the Five Eyes, Nine Eyes and Fourteen Eyes Intelligences?
You’ll often hear of “five eyes countries” (and “nine eyes” and “14 eyes” countries) in the context of online privacy.
This guide lays out what these terms mean. Furthermore, which countries are part of them, and everything else you need to know.
So, let’s begin with the basics:
Who are the Five Eyes countries?
The Five Eyes countries are:
- United States
- United Kingdom
- Australia
- New Zealand
- Canada
Five Eyes (sometimes referred to as FVEY) is an intelligence alliance that dates back to the early 1940s.
Who are the Nine Eyes countries?
The Nine Eyes countries are:
- The 5 Eyes Countries
- Denmark
- France
- Netherlands
- Norway
As you might suspect, Nine Eyes is an extension of the core Five Eyes alliance.
Who are the 14 Eyes countries?
The 14 Eyes countries are:
- The 9 Eyes Countries
- Germany
- Italy
- Belgium
- Sweden
- Spain
This alliance is also known as SIGINT Seniors Europe (SSEUR). According to Wikipedia, it’s there to coordinate “the exchange of military signals intelligence among its members”.
History of the Five Eyes Alliance
Five Eyes originally came about as a way for the core countries to share intelligence. It was founded as the informal UKUSA agreement in 1941. Official formalization between the UK and USA was in 1946, in the wake of the second world war. However, since then it also encompasses other core countries.
Beyond the core Five Eyes countries come the other nations that form the Nine and 14 Eyes groups. These nations joined the scheme as “3rd party countries”. Furthermore, it’s widely believed that other countries in the schemes beyond the core countries listed. The suspected countries include “Pacific allies” such as South Korea and Singapore.
Five Eyes and similar arrangements are (by their nature) always secret. Wikipedia suggests that it was nearly 30 years after the original formation of the agreement before the Australian Prime Minister even became aware of it. Furthermore, Five Eyes only came to public attention in 2005. Since 2010 it’s been possible to read some of the details of it online on the UK’s National Archives website.
Recent Years Controversy
The Five Eyes agreement gained modern mainstream relevance when links to the NSA were proven. These were made public as part of the infamous Edward Snowden leaks. His revelations showed and confirmed that agreements made during the Cold War are being extensively used in the pursuit of widespread digital surveillance.
It became clear that these countries are using intelligence sharing agreements for purposes that go beyond signals intelligence. Therefore, they effectively allow the intelligence services in multiple countries to liaise with each other. Thereby sharing information relating to anything from human and defense intelligence to matters of national security.
An example of how this can work in practice came out with Snowden’s revelations in 2013. It emerged that the American NSA effectively outsources work to the UK’s GCHQ.
Most controversially for advocates of privacy, the Snowden revelations showed that governments make use of the Five Eyes framework to get around laws about monitoring their own citizens. As an example, the UK’s MI5 can ask the US NSA to tap UK phones, thus “allegedly circumventing laws.”
“Britain’s GCHQ intelligence agency can spy on anyone but British nationals, the NSA can conduct surveillance on anyone but Americans, and Germany’s BND foreign intelligence agency can spy on anyone but Germans. That’s how a matrix is created of boundless surveillance.”
What do the 5 / 9 / 14 Eyes alliances do?
If you’re a privacy conscious individual, this is a very valid question. Furthermore, it’s more than reasonable to argue that what the agencies within these alliances do goes far beyond what they need to do to ensure they keep the world “safe.”
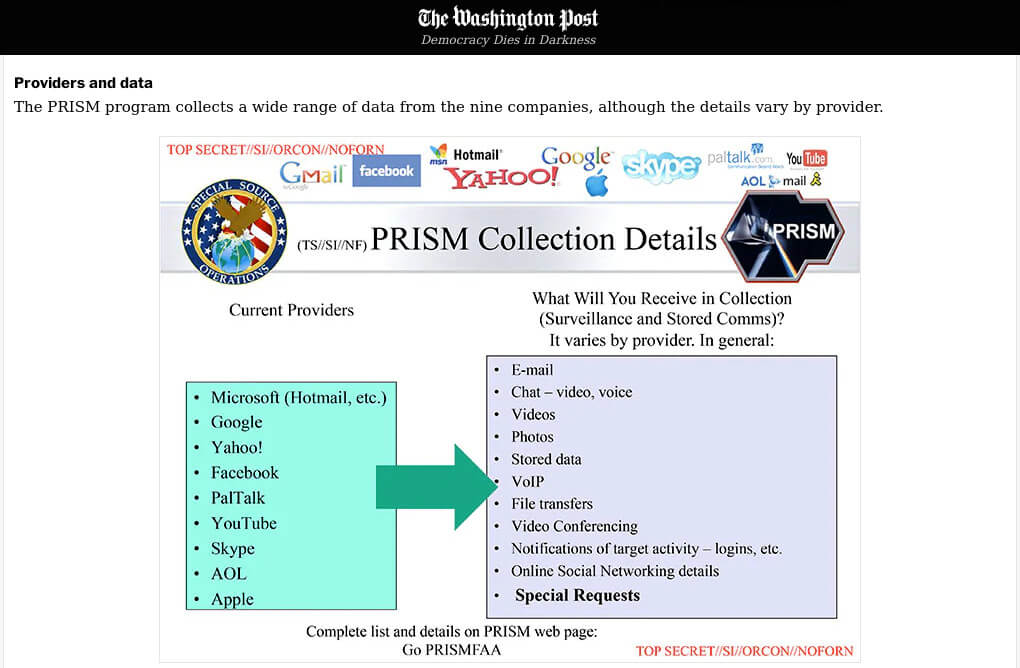
One of Edward Snowden’s most headline-grabbing revelations related to the NSA’s PRISM program, a mass data collection initiative whose participants include all the big players in the Internet world, including Microsoft, Google, and Facebook. PRISM has made it incredibly easy for the NSA (even its “low-level agents”) to access information on commonly-used platforms. Therefore, due to the alliances, other countries easily tapped into this ability as well. Unfortunately, even those who believe they have “nothing to hide and nothing to fear” would be spooked by the ease with which the NSA – and therefore their alliance partners – can tap into anything from Skype conversations to email messages.
Then we can add to that the fact that these security agencies have been shown to engage in practices that are at best – underhand. These include cracking encryption algorithms and bribing companies to weaken their own IT security systems
We’re not suggesting that the 5 / 9 / 14 Eyes alliances’ sole purposes are to snoop on citizen’s day-to-day lives. Unfortunately, the by-product of much of the related agencies’ work allows them to do just that.
The Alliances and VPN Use
For many, the whole point of using a VPN (Virtual Private Network) service is to avoid government surveillance. Thereby being able to browse the Internet with a reasonable level of privacy.
As you can see from the information above, you can easily defeat that object by choosing a VPN provider based in one of the countries. Particularly the Five Eyes countries, or one that locates its servers in one of those countries. Thereby, authorities could compel a provider to hand over details of your online activities. Furthermore, thanks to the information sharing, it could be ANY of the countries on the list!
Using a VPN server in a 5 Eyes Country
A commonly asked question is what the position is if someone uses a VPN provider in a country outside of the 5 / 9 / 14 Eyes jurisdiction. Then uses it to connect to a server in a country that IS within that jurisdiction, such as in the US or UK.
Without going into too much technical detail, there is some risk here. The FVEY country could subpoena the server provider for connection logs (or even perform its own monitoring of connections into and out of the server). However, if the VPN provider is taking the right security precautions on their infrastructure, the risk should be relatively small.
That said, people keen to minimize their exposure to the broad jurisdiction of these intelligence alliances should take the lowest-risk approach. That would be using a provider outside the 5 / 9 / 14 Eyes jurisdiction AND only connecting to servers outside of the jurisdiction.
So which VPN should I choose?
A good starting point is to look at our Best VPN no logs guide.
These VPN services don’t keep any record of your browsing activity. Therefore, if they were ever required to hand over details of usage, they wouldn’t have any of that information to share.
Therefore, choose a VPN that’s outside the far-reaching jurisdiction of 5 / 9 / 14 eyes, AND one that doesn’t keep activity logs. Thereby you are doing all you can to minimize the chance of your online activity being subject to a questionable level of surveillance. This is why we do not recommend using a free VPN as they can be dangerous and they often sell your data.