Can I use a VPN with Tor
Источником запросов может служить вредоносное ПО, подключаемые модули браузера или скрипт, настроенный на автоматических рассылку запросов. Если вы используете общий доступ в Интернет, проблема может быть с компьютером с таким же IP-адресом, как у вас. Обратитесь к своему системному администратору. Подробнее.
Should you use a vpn with tor
Об этой странице
Мы зарегистрировали подозрительный трафик, исходящий из вашей сети. С помощью этой страницы мы сможем определить, что запросы отправляете именно вы, а не робот. Почему это могло произойти?
Эта страница отображается в тех случаях, когда автоматическими системами Google регистрируются исходящие из вашей сети запросы, которые нарушают Условия использования. Страница перестанет отображаться после того, как эти запросы прекратятся. До этого момента для использования служб Google необходимо проходить проверку по слову.
Источником запросов может служить вредоносное ПО, подключаемые модули браузера или скрипт, настроенный на автоматических рассылку запросов. Если вы используете общий доступ в Интернет, проблема может быть с компьютером с таким же IP-адресом, как у вас. Обратитесь к своему системному администратору. Подробнее.
Проверка по слову может также появляться, если вы вводите сложные запросы, обычно распространяемые автоматизированными системами, или же вводите запросы очень часто.
Can I use a VPN with Tor?
Generally speaking, we don’t recommend using a VPN with Tor unless you’re an advanced user who knows how to configure both in a way that doesn’t compromise your privacy.
You can find more detailed information about Tor + VPN at our wiki.
- Contributors to this page: cypherpunk
- Edit this page – Suggest Feedback – Permalink
Download Tor Browser
Download Tor Browser to experience real private browsing without tracking, surveillance, or censorship.
Our mission:
To advance human rights and freedoms by creating and deploying free and open source anonymity and privacy technologies, supporting their unrestricted availability and use, and furthering their scientific and popular understanding.
Donate Now
Subscribe to our Newsletter
Get monthly updates and opportunities from the Tor Project:
Using Tor over a VPN: What, why and how?
We live in a world where the FBI can now look at your browsing history without a warrant – and that’s just the US. Developments like these are making a lot of people more cautious about their online privacy. Some turn to virtual private networks (VPN) to secure their everyday browsing. Others turn to Tor solutions to hide their trails. But what about combining these approaches? Is it possible and what would the benefits and the downsides be? Let’s find out.
Premium protection
Crush viruses, data leaks, and online threats
Secure your device with antivirus protection
Get email, credit card, & ID breach alerts
Change your IP address & stay safe online
Using Tor over a VPN: in short
Tor refers to both the software for making your internet traffic untraceable and the volunteer network of servers that makes it possible. It’s secure but too slow for everyday use, and the security can be compromised by malicious agents setting up their own servers.
Meanwhile a VPN is a simpler and faster approach to securing your connection by encrypting your data and routing it via a VPN server. It’s great for everyday use. However, by combining them together, you can protect yourself from people trying to spy on you via compromised Tor routers. We explain it in more detail further on.
Table of contents
What is Tor?
Tor is the name of the software for anonymous communication and the network it uses to carry this out. It’s usually accessed via the Tor Browser maintained by the Tor Project, though there also exists an operating system called Tails that routes all of your internet traffic via the network.
The title itself comes from The Onion Router. No, it doesn’t have anything to do with the satire website of said name. However, it does deal with layers.
How does Tor work?
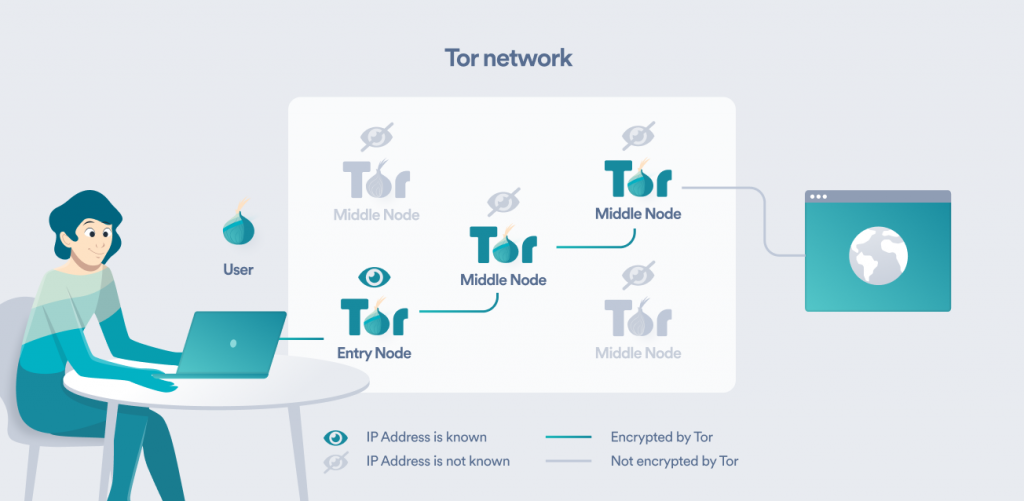
To keep your identity anonymous, Tor software bundles your data into three layers of encryption. Tor routes your data via three nodes (the servers established by volunteers) before it reaches online.
Each node removes a layer (with the previous address on it) to reveal the address of the next node. In essence, only the first node – called “the entry node” – knows who is sending data but not what that data is, while the third node is the only one to know what data is sent – but not where it comes from.
But how is it different from a VPN?
What is a VPN?
VPN stands for “virtual private network.” It recreates the security of two computers communicating without intervening links but by using the internet. It’s like laying down a direct wire to the other device without leaving your home.
How does a VPN work?
VPNs accomplish that task via tunneling . Your data is split into packages and sent via a virtual tunnel between your device and the destination. Those packages are encrypted so that nobody would know what you’re sending.
Finally, that data is routed via a VPN server , which allows VPN to do things like hide your IP and make you appear as if connecting from another place (city or country).
Why use Tor over a VPN?
Using Tor with a VPN is a good way to add another layer of security. This is because a VPN protects you in case the Tor network is compromised, and it hides Tor use.
Both of the technologies are good at what they do, but they have their own downsides:
VPN downsides
Tor downsides
May keep data log logs on the server side (look for VPN providers with no-log policies)
Nodes may be compromised and expose your data. This way, your browsing history could be reconstructed.
Your ISP or government might get suspicious if you’re using Tor.
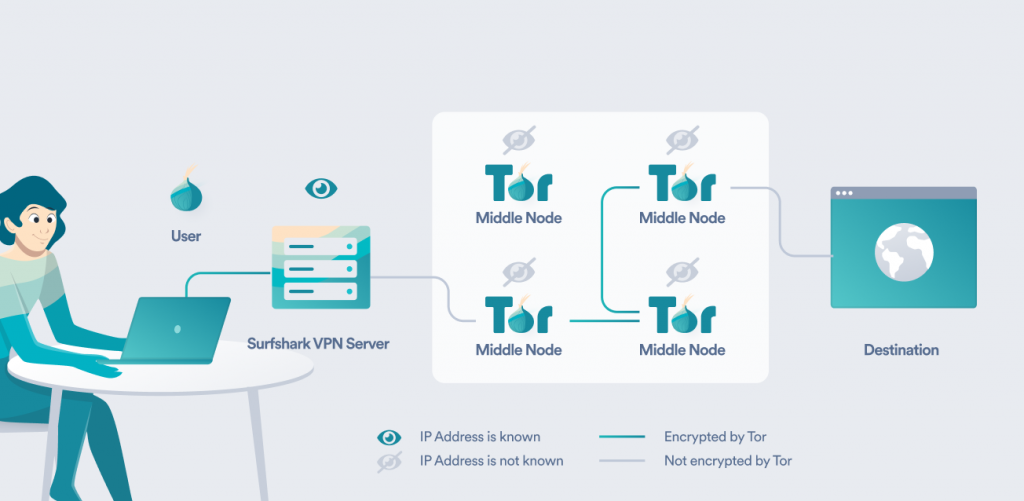
To avoid these, you can use Tor over a VPN. The VPN will shield your data on its way to the entry node. Your ISP won’t be able to see that you’re using Tor – only that you’re using a VPN (and good VPNs can obfuscate even that). And when your data reaches the entry node, it will show the IP of the VPN server, not your device – meaning that IP is hidden and it can’t be traced back to you.
At the same time, Tor encrypts data by itself. So when it goes over the VPN server, the server can’t register what you’re actually doing – it can only see that you’re using Tor.
But how do you combine Tor and a VPN? Turns out, it’s quite easy to do. Read on and follow our quick, simple guide.
How to use Tor over a VPN
It’s not that hard to use Tor with a VPN – you just need a trustworthy and secure VPN provider (and the Tor Browser, obviously). Here’s a short guide using Surfshark VPN as an example.
- Sign up for Surfshark .
- Download and install the client .
- Sign into the client.
- Click “Connect” to connect to the fastest server.
- Download and install the Tor Browser .
- Launch the Tor Browser and connect to the Tor network.
- That’s it!
Now, Tor is already slow due to all the nodes, so you may experience a slight additional speed drop due to adding the VPN server to the chain.
But what if you wanted to try a VPN over Tor?
What about a VPN over Tor?
It is possible to set up a VPN to work over Tor. Or rather, to put a VPN after the Tor node network. This is useful if you want to access websites that don’t allow Tor connections. Here’s the Tor Project’s list of websites that either block Tor connections or ask for additional verification when you use Tor.
Is it safe, easy to use, or at all recommended? No, it’s not . It forgoes the most important reason for using Tor over a VPN – namely, keeping your identity secret from the person who hosts the entry node. Neither does it mask Tor use from scrutiny by your ISP.
So unless you really, really need to use a website that doesn’t accept connections from the Tor network, stick to Tor over a VPN.
So, what’s the difference between Tor over a VPN and a VPN over Tor?
In short, the difference between using Tor over a VPN vs. a VPN over Tor are: