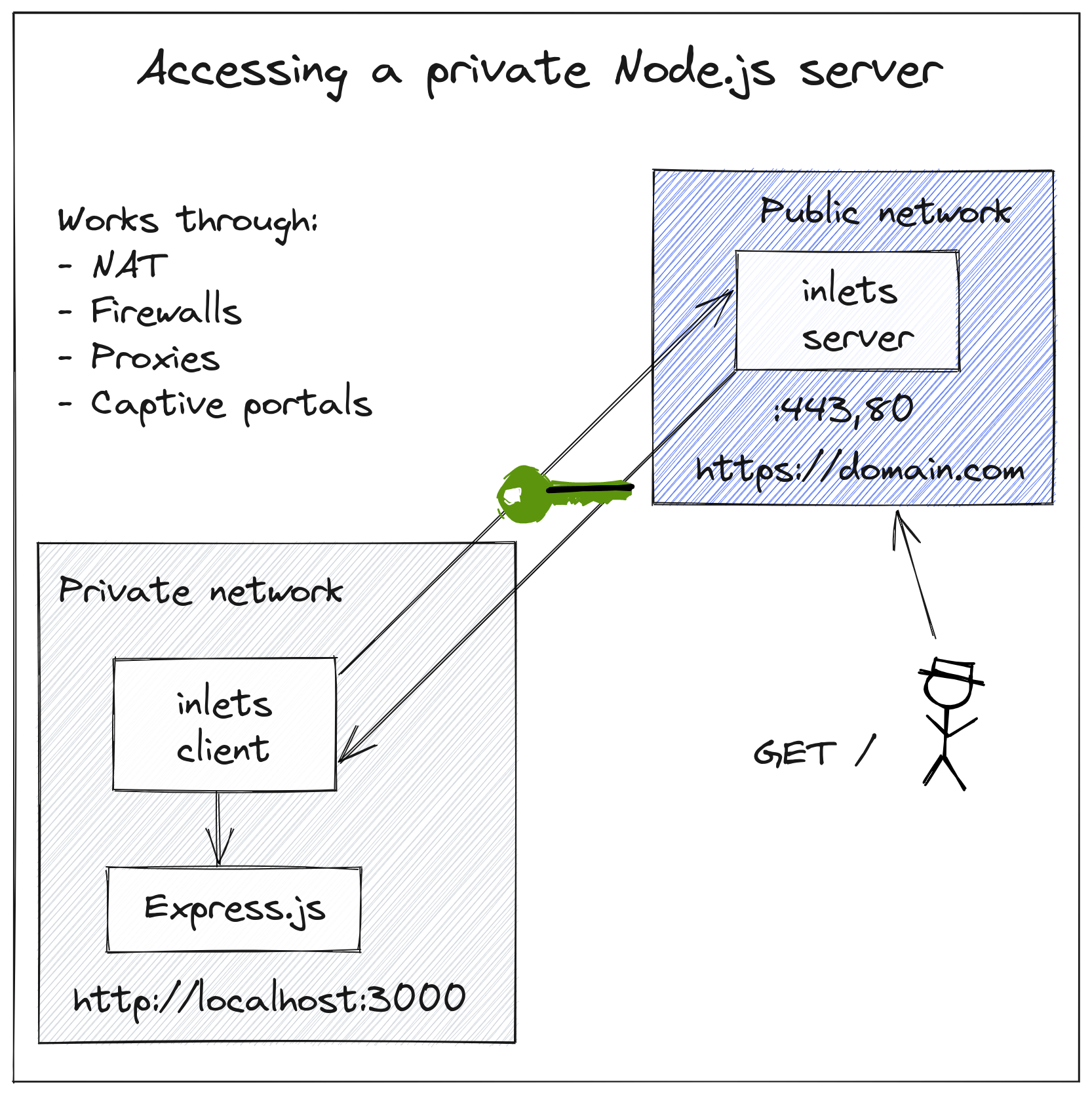
Serve traffic through a private tunnel
Once the tunnel server has been created, you will receive:
Private Tunnel Review 2023
Private Tunnel is the VPN service from the folks behind the OpenVPN protocol itself. But does that necessarily make it better than the competition? After all, almost every other VPN provider out there also supports the OpenVPN protocol.
I was very curious at the start of this review because OpenVPN is the most widely used VPN protocol today. So the team behind Private Tunnel already has that rather huge trophy. And that heightened my expectations.
This Private Tunnel VPN review answers the following questions:
- How fast is Private Tunnel?
- Is it secure and private?
- Does Private Tunnel work with streaming sites like Netflix, BBC iPlayer, and Amazon Prime Video?
- Does Private Tunnel work in China?
- Does Private Tunnel offer anything that its competitors do not?
Below is a summary of what I think of Private Tunnel. For full analysis, do read the full review.
TRY OUR #1 RATED VPN RISK-FREE FOR 30 DAYS
If you are looking for the best VPN, NordVPN is our highest-rated and is offering a risk-free 30-day trial if you sign up at this page.
There are no hidden terms—just contact support within 30 days if you decide NordVPN isn’t right for you and you’ll get a full refund. Start your NordVPN trial here.
Private Tunnel Summary
I had high hopes for Private Tunnel, but I was, unfortunately, let down. The speeds aren’t that great. The server list is small. And the feature list is even smaller. I wasn’t able to access many streaming sites and the service doesn’t work in China, either. On the plus side, Private Tunnel offers 24/7 support to its users, provides a malware blocker, and I’m pretty sure their OpenVPN servers are well-configured – which is the only VPN protocol it supports.
Private Tunnel Key data
* Average speed over multiple global locations based across multiple speed tests per day.
How does Private Tunnel compare to other VPN providers?
Here’s how Private Tunnel compares to two of the most widely-used and trusted VPN providers, NordVPN and Private Internet Access:
Private Tunnel pros and cons
Pros:
- Malware blocker
- Built by the people behind the OpenVPN protocol itself
- 7-day free trial (requires a credit card)
- Good and consistent speed even on faraway servers
- Good yearly price
Cons:
- Does not work with streaming sites
- Does not work in China
- No kill switch
- Vulnerable to WebRTC leaks
- Does not support torrenting
- Basic plan only allows for three simultaneous connections
- Logs some data
- Few servers on offer
- Only supports OpenVPN
- No dedicated privacy policy
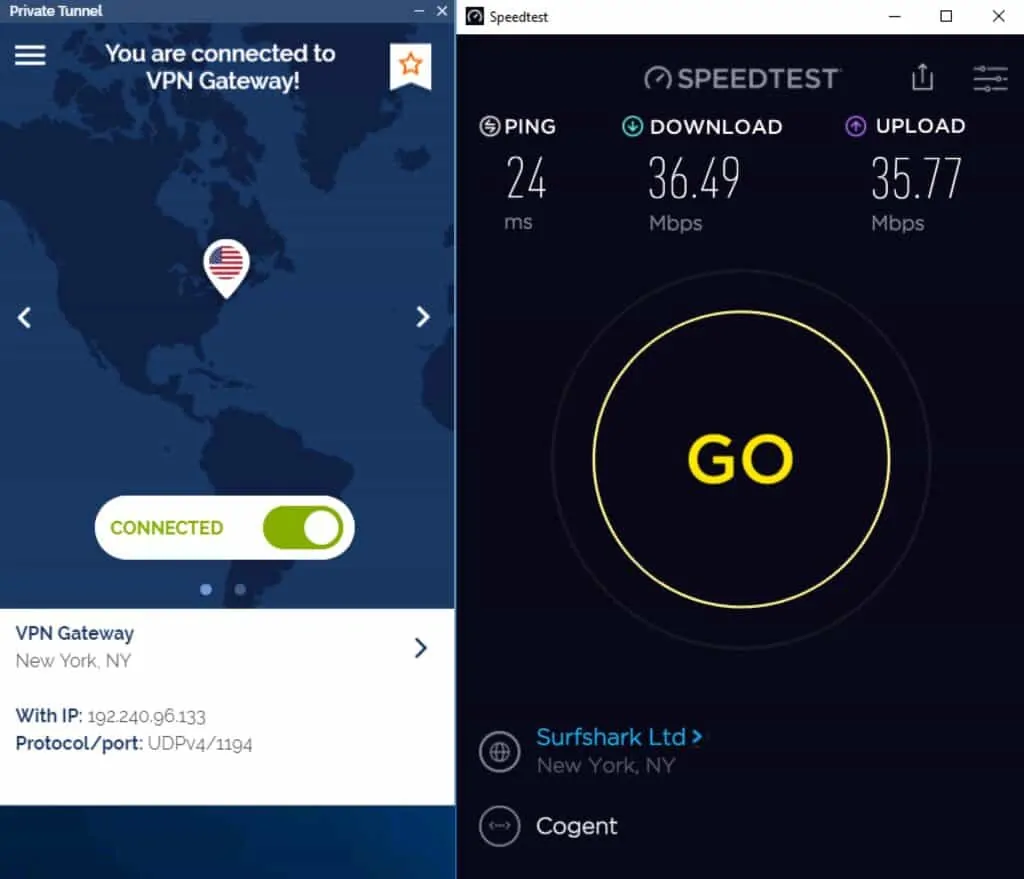
Is Private Tunnel fast?
Speed is always going to be important for any VPN provider. You don’t want your VPN bogging down your high-speed connection.
Private Tunnel’s speeds were pretty good. Not amazing, but adequate, consistent, and better than others. I was surprised to see that Private Tunnel’s speeds didn’t change when connecting to faraway servers. That’s a definite plus.
I tested Private Tunnel’s speed over three regions. Here are the average speeds per region:
The global average comes to: 42.6 Mbps
All the speed tests were conducted using the OpenVPN protocol (the only protocol supported by Private Tunnel).
In terms of gaming online, Private Tunnel performed well. I had no lag or hiccups on any of the three games I tried. In-game voice chat was also smooth. No audio stuttering or lag. I tried different servers and even when connected to a faraway server, my connection was fast and gaming was smooth.
Supported devices
Private Tunnel provides native apps for the following platforms:
That’s not bad but I’ve seen better. And I would have liked to see router support.
You can connect up to three devices on the base plan. If you want more, you can but at an extra cost. Raising the limit to five connections, for example, will run you $8.00 (GBP £6.05) a month, rather than $6.00 (£4.54). Most VPN providers allow you to connect five or more. So there’s room for improvement on this front.
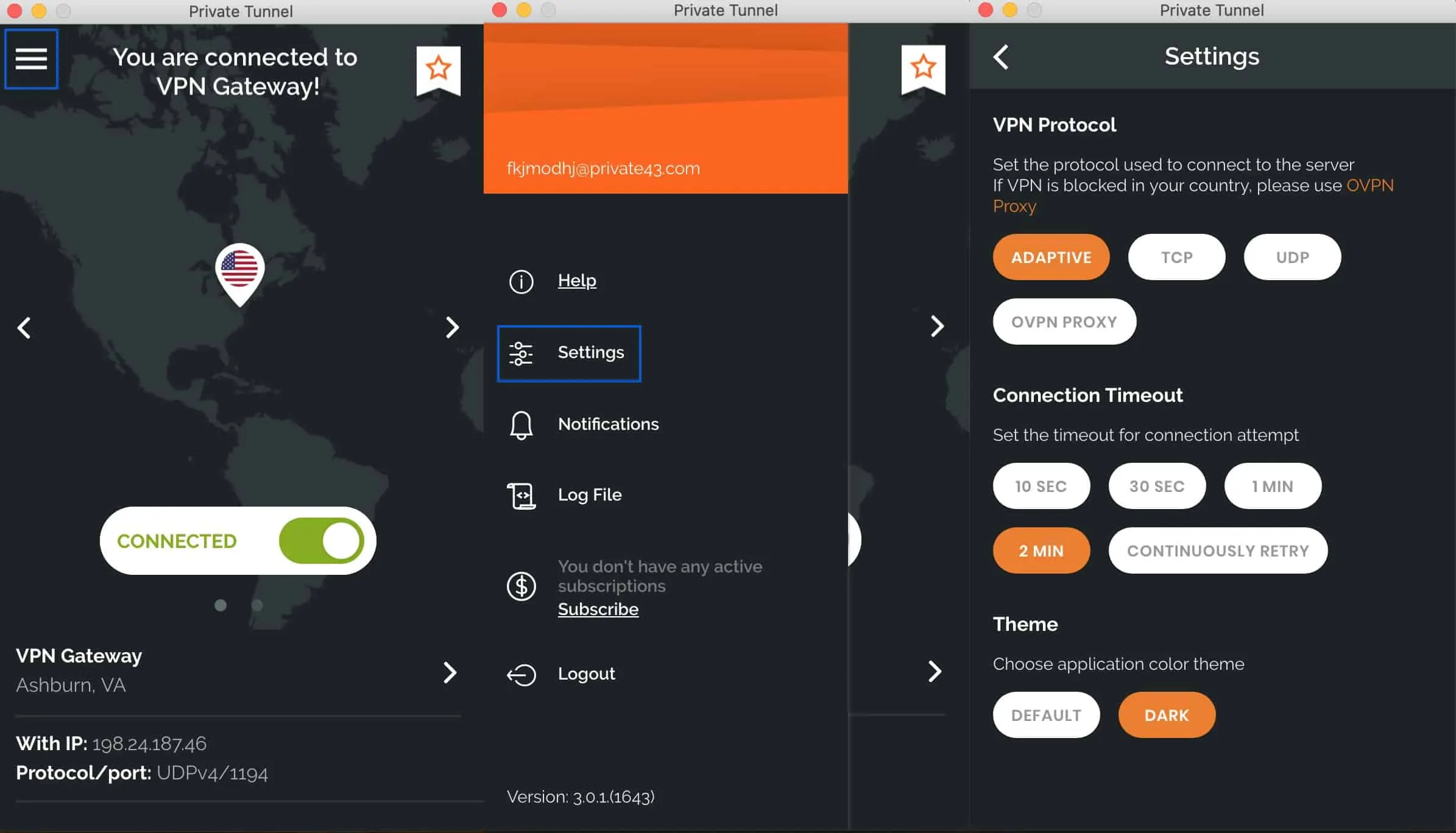
The app is simple enough to navigate and understand. I don’t think even new users would have trouble with it. If you’ve ever used the OpenVPN Connect app for iOS or Android, you’ll feel right at home. The apps definitely share some design cues, which makes sense as the people behind OpenVPN are the people behind Private Tunnel.
The macOS client is shown below.
Private Tunnel does not support routers nor does it provide browser extensions at this time.
I mentioned earlier that Private Tunnel does not provide a dedicated privacy policy – and that’s true. However, when you log in to the app for the first time, a privacy policy is displayed in the app and you need to accept the terms.
I will comment on this in the Security, privacy, and logging section.
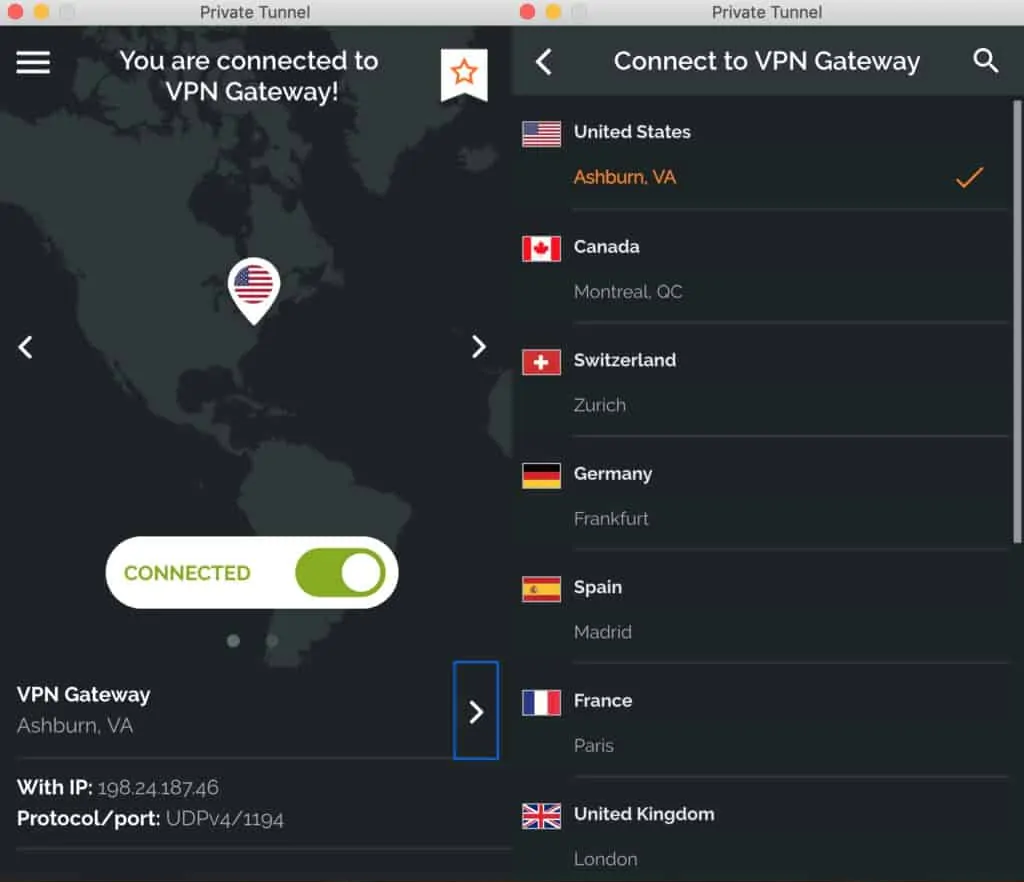
Private Tunnel servers
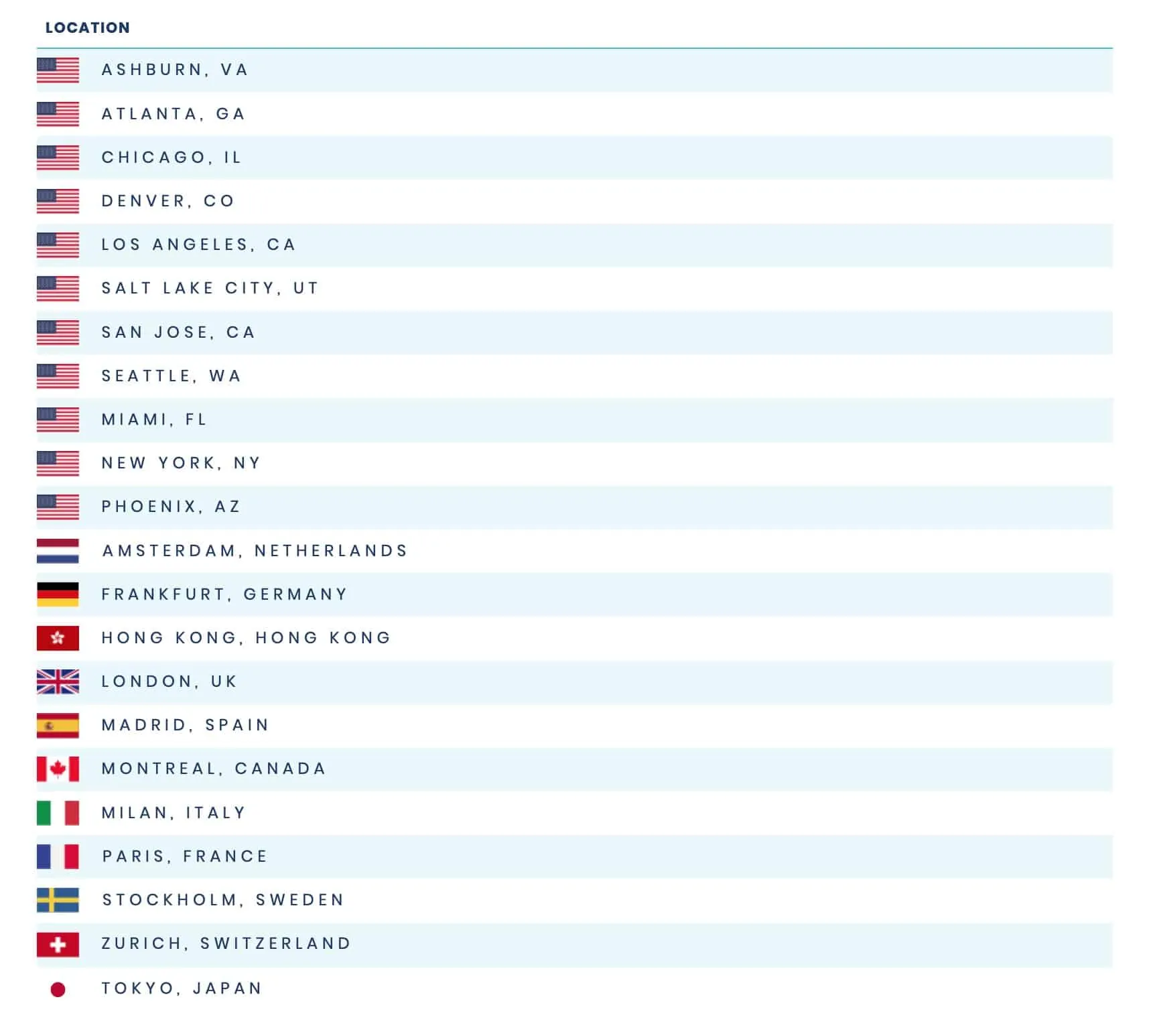
Private Tunnel provides access to fewer VPN servers than most of its competitors. This isn’t usually something I complain about much. However, in Private Tunnel’s case, the list is really very small.
Private Tunnel provides access to just 22 servers in only 12 countries. That’s really small. If you’re looking for a VPN provider that provides worldwide coverage, you’ll need to look elsewhere.
Streaming
What’s the streaming situation with Private Tunnel? It isn’t great.
Looking through its support section, I found a support document that answered the question: Do you guarantee that certain services are available while connected to PrivateTunnel? Private Tunnel’s answer is:
“PrivateTunnel does not block objectionable content while you are connected to our services, with the exception of destinations that have been reported to be spreading malicious malware or associated with viruses and network worms. As much as we try to ensure content availability for all of our users, we cannot provide any assurance that geo-restricted services can be accessed over our services. This includes streaming services such as Netflix, BBC iPlayer, Hulu, and other services that prohibit access from anonymizers and public VPN services”.
So that didn’t exactly fill me with optimism.
In my tests, I was unable to access Netflix, BBC iPlayer, or Hulu – as stated by Private Tunnel. But I also tried Amazon Prime Vide, 4All, and ITV Hub with the same result: no access.
Streaming is definitely not one of Private Tunnel’s strong points. If streaming over VPN is important to you, you should look for a different provider, such as NordVPN or ExpressVPN.
Check out our recommended VPNs for streaming.
Does Private Tunnel allow torrenting?
The short answer is no, it does not. P2P traffic is blocked on most of Private Tunnel’s servers. Apparently, there are a few over which it will work but Private Tunnel doesn’t recommend it. They claim you may encounter issues and that your experience may be degraded.
So if you’re a big torrenter, Private Tunnel may not be the best choice for you.
Have a look at our recommended VPNs for torrenting.
Does Private Tunnel support split tunneling?
Split tunneling enables you to perform what is called selective routing. This means that you can route certain applications through the VPN while letting other traffic flow through your ISP connection. So, for example, you could route your Netflix traffic through your ISP connection and send all other traffic through the VPN. It’s extremely flexible and can be set up as you like.
Just remember to deactivate split tunneling when you’re done, so that you don’t inadvertently use your ISP connection while thinking you were going over the VPN tunnel.
Private Tunnel does not support split tunneling at this time.
Have a look at our recommended VPNs for split tunneling.
Security, privacy, and logging
Private Tunnel is based in the US, which isn’t the most privacy-friendly jurisdiction out there. Still, I’ve always felt that if a VPN provider commits to a strong no-logging policy and sets up its infrastructure not to log, then jurisdiction becomes less critical.
So what’s Private Tunnel’s privacy policy like? Well, at the bottom of its webpage, we can click on Private Tunnel’s ‘Policy’. Clicking that takes you to a privacy policy—but only relative to Private Tunnel’s website, not its VPN service. No luck there.
As far as logging goes, we find this:
And lower down, Private Tunnel states:
“Log files stored on our servers are only used for monitoring server performance, identifying software bugs, identifying any potential security breaches, and for the purpose of identifying abusive users. The log files are not used for monitoring or censoring your internet activities. We respect your privacy. We are not interested in what you do on the internet”.
So clearly there’s some logging going on and, so far, Private Tunnel is rather vague on what is actually collected.
As I mentioned above, when you first log into the Private Tunnel client, its privacy policy (or at least a summary of its data collection practices) is displayed. You need to scroll through it to read the whole thing—which isn’t ideal. This should be on its website. Really.
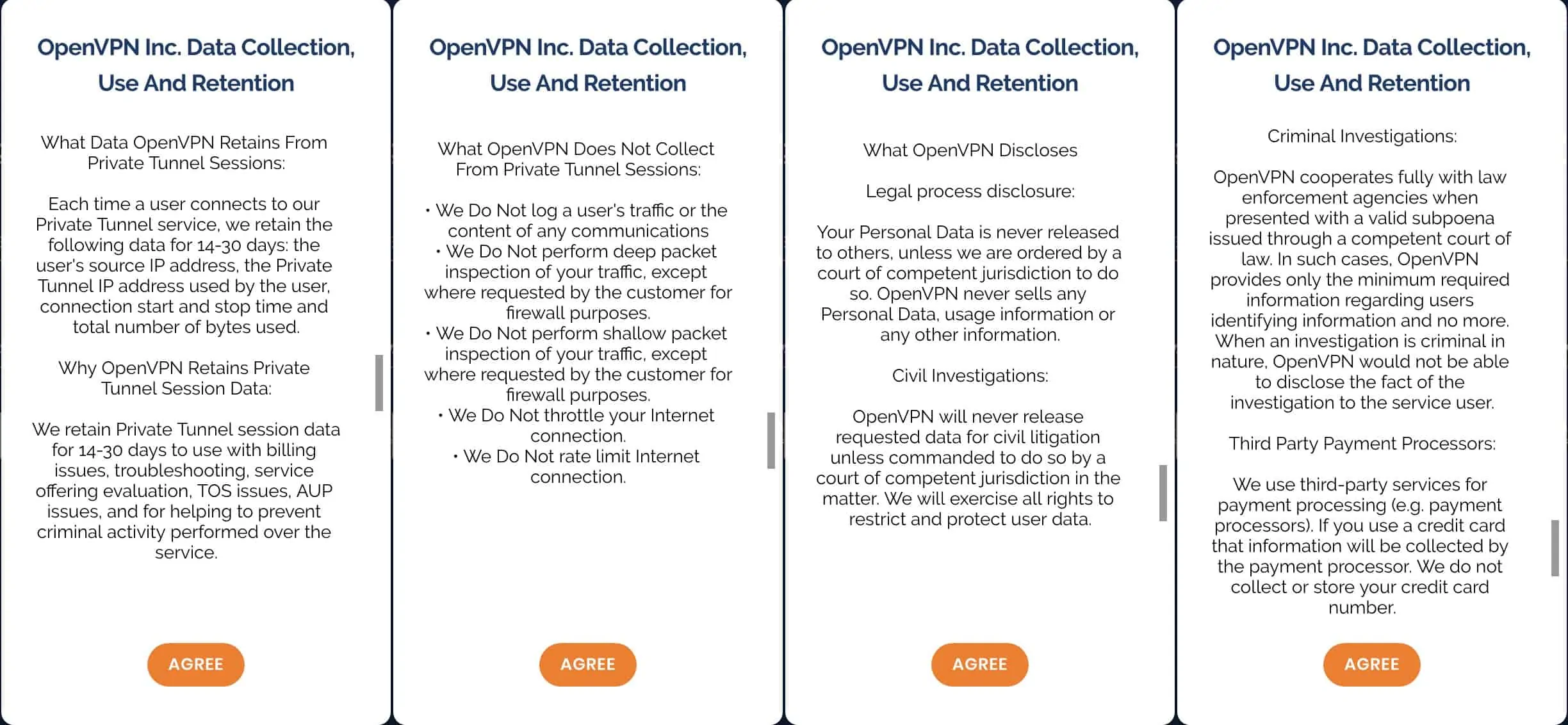
So what does Private Tunnel collect?
- Source Ip address
- VPN server IP address
- Connection timestamps
- Bandwidth usage
That’s quite a lot. This data is kept for 14 to 30 days. These are not the best collection practices we’ve seen.
Moving on to protocols and encryption, Private Tunnel only supports OpenVPN. Now I know Private Tunnel is built and operated by the people behind the OpenVPN protocol itself, but that’s no reason to limit your service offering to a single protocol. Other secure VPN protocols are supported by most commercial VPN providers today, like IKEv2 and WireGuard.
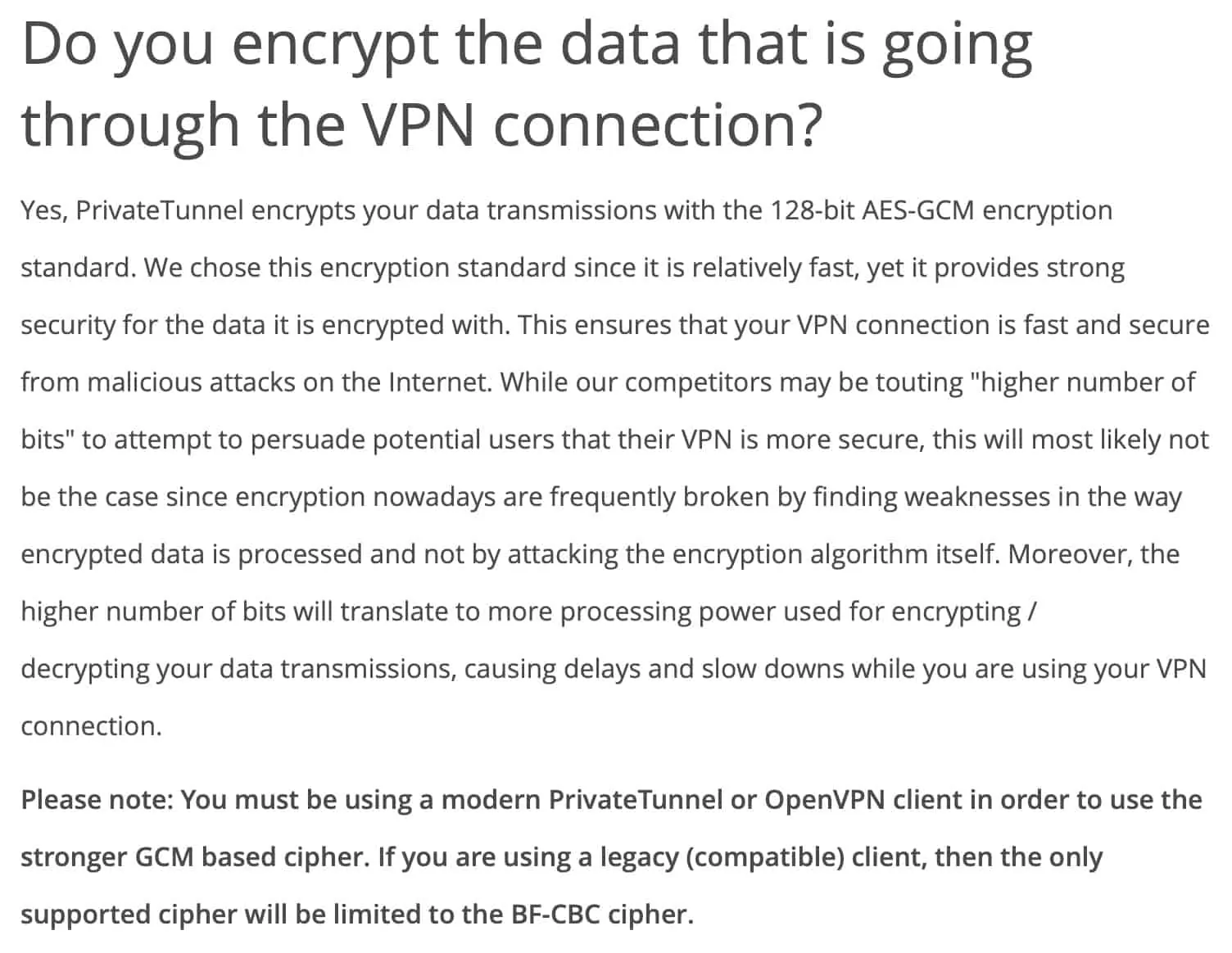
As far as encryption goes, Private Tunnel only supports 128-bit AES-GCM, for modern OpenVPN implementations and 128-bit AES-CBC, for legacy implementations. To be clear, 128-bit encryption is wholly secure. It’s just that 256-bit encryption is the de facto industry standard in the commercial VPN market. It is, however, possible that it’s the 128-bit encryption that gives Private Tunnel its edge in speed.
I’m afraid that’s the extent of the encryption information on Private Tunnel’s website. It’s not the most informative website I’ve seen.
Private Tunnel also provides a malware blocker. It even has a page dedicated to the feature on its website. Unfortunately, it isn’t very informative either. Aside from claiming Private Tunnel “blocks online threats, shields your devices, blocks hackers, and protects your private information”, there isn’t a word on how this is achieved.
The malware blocker is also not a feature you enable within the app, as I found no references to a malware blocker in the app. And again, I was unable to find any details on how this malware blocker works.
While more information is certainly needed, let’s be grateful for small favors. A malware blocker is a good thing and this is a plus. Let’s just hope its malware lists are updated more often than its website.
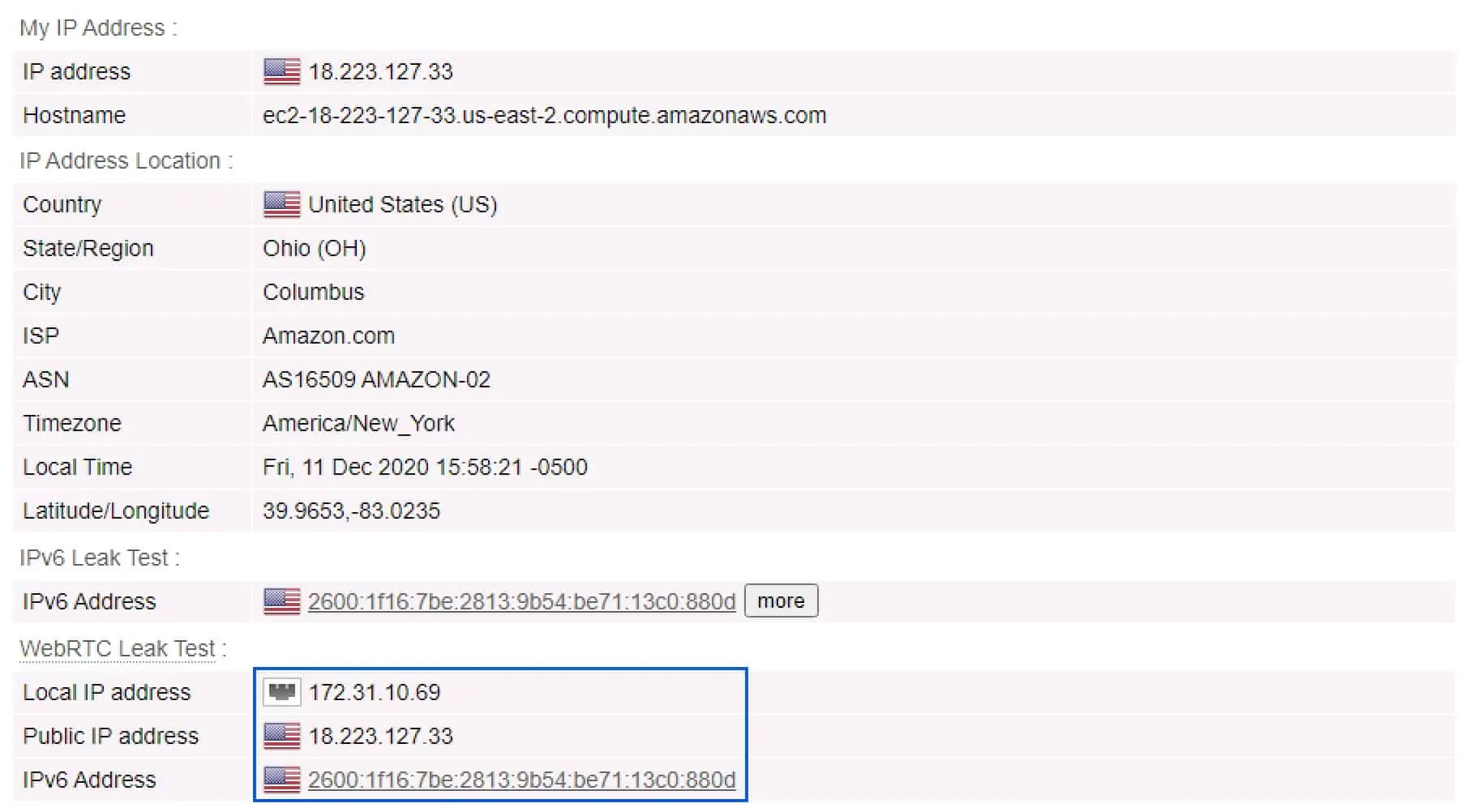
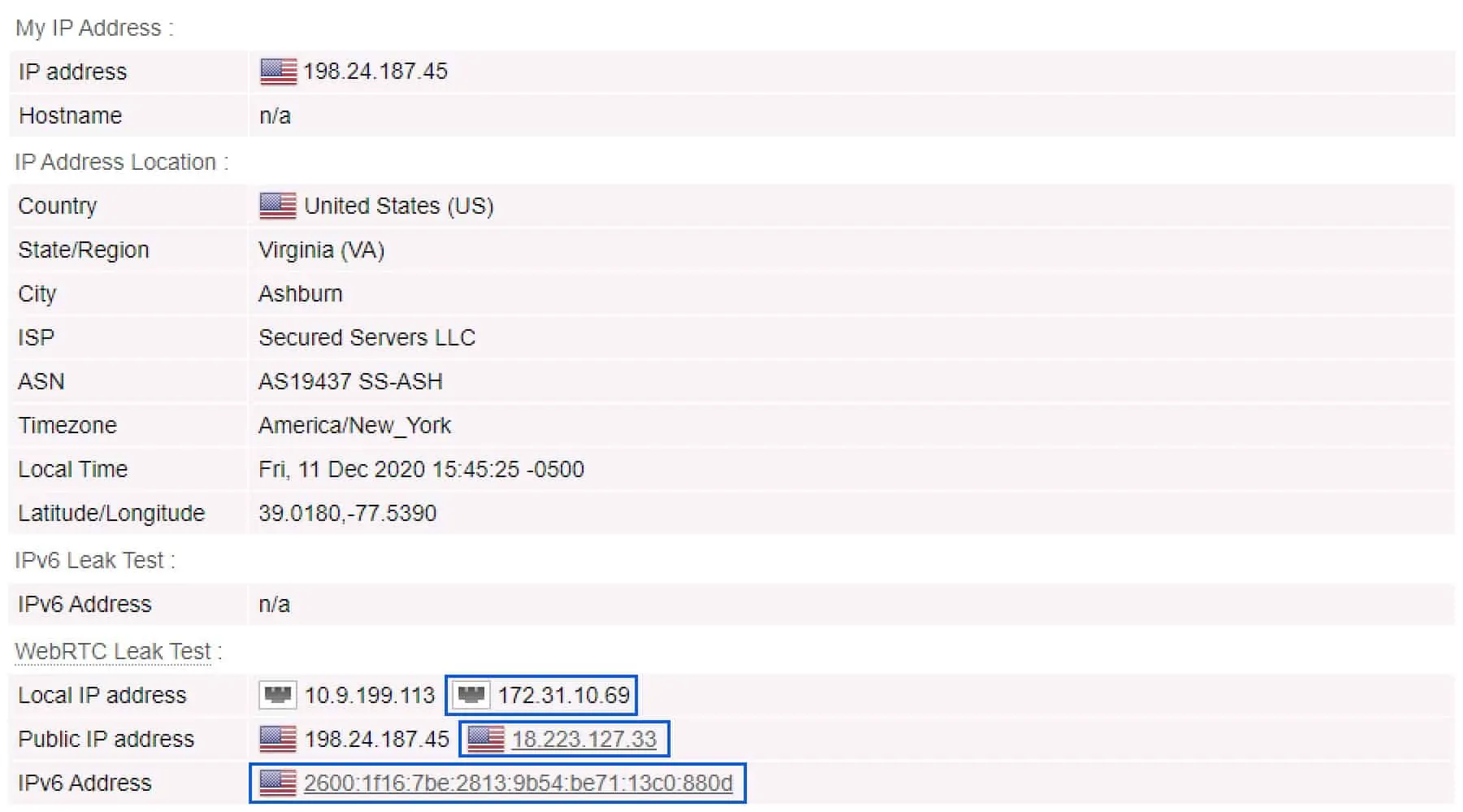
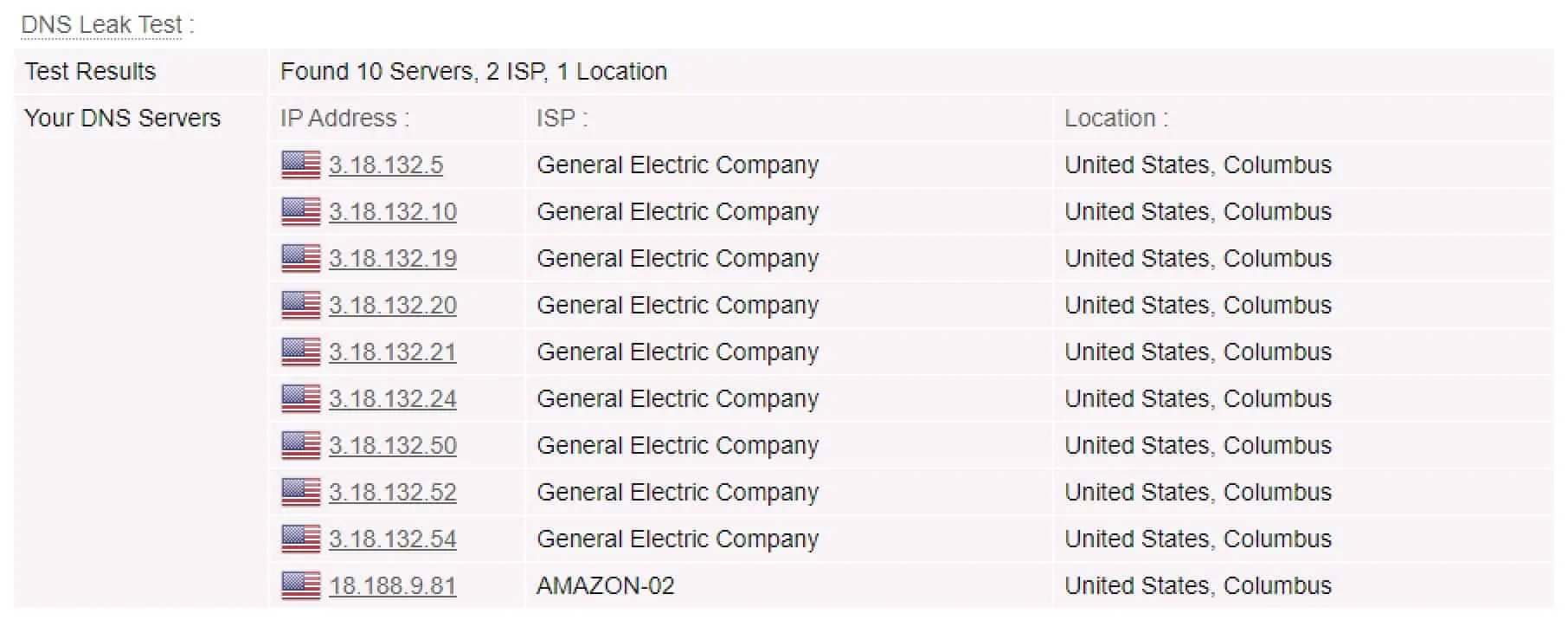
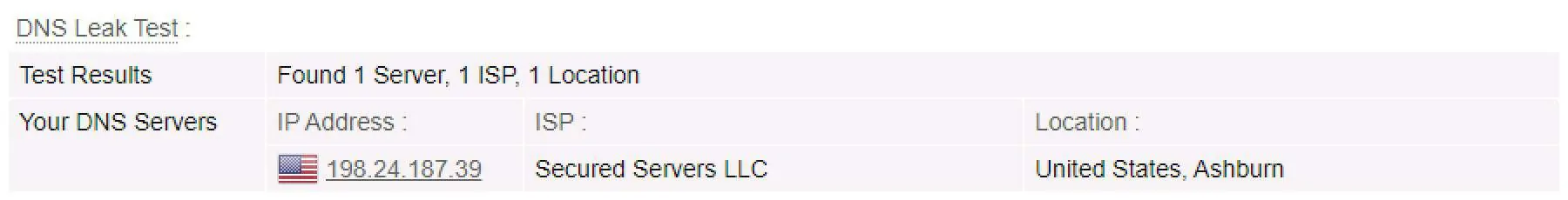
In testing Private Tunnel for leaks, I didn’t run into any DNS leaks. But I did find a WebRTC leak, that was exposing my real public IP address as well as my local IPv4 and IPv6 IP addresses.
Notice that in the screenshot taken with the VPN enabled, my real public, private and IPv6 IP addresses are listed in the WebRTC Leak Test section. That’s pretty bad.
WebRTC stands for Web Real-Time Communication. It is an open-source protocol that provides web browsers and mobile applications with real-time, direct peer-to-peer audio and video communication. WebRTC leaks can expose both your real public IP address (from your ISP) and your real local IP address (assigned by your router).
There are ways to stop WebRTC leaks. We have a detailed guide on stopping WebRTC leaks. I strongly recommend following the advice in his article regardless which VPN provider you use, or even if you don’t use a VPN.
IP test without Private Tunnel
IP test with Private Tunnel
DNS test without Private Tunnel
DNS test with Private Tunnel
In line with the industry’s best practices, Private Tunnel provides its users with a shared IP address. Shared IPs are more private, as they make it more difficult to trace traffic to specific users.
Does Private Tunnel work in China?
Not being in China, this is usually a tough one to answer. I normally have to troll through support forums to deduce whether or not it actually works. But not this time. Private Tunnel has a handy support document that lists all of the possible reasons why its service might not work. At the bottom of that list, we find the following:
“Country based censorship – Some countries impose access restrictions to VPN services due to the censorship rules in place in the region. If you are traveling to these countries, our service is not likely to work until you return to your home country”.
The list of countries is:
- China
- Saudi Arabia
- United Arab Emirates (UAE)
- Oman
- Iran
- Turkmenistan
While the service not working in China might be a bummer, at least we have a clear answer and know what to expect.
If you’re looking for a VPN that works in China, check out our recommended VPNs for China.
How is Private Tunnel’s customer service?
I was a little bit confused when I wasn’t able to find a proper privacy policy dedicated to Private Tunnel’s VPN server. So I decided to write an email to its support department to find out if it did publish a VPN service privacy policy on its website. Having seen 24/7 support listed in Private Tunnel’s marketing, I was expecting a prompt reply.
Well, it’s been four days and I’ve yet to receive a response. So I can’t say I’m very impressed. Still, the support section on its website answers most of the basic questions one might have. But 24 hour support? Nope.
While we’re on the subject of Private Tunnel’s website, I have to say that it looks like it was last updated in 1997. That and the fact that there’s apparently no support could make you wonder if anyone still works there.
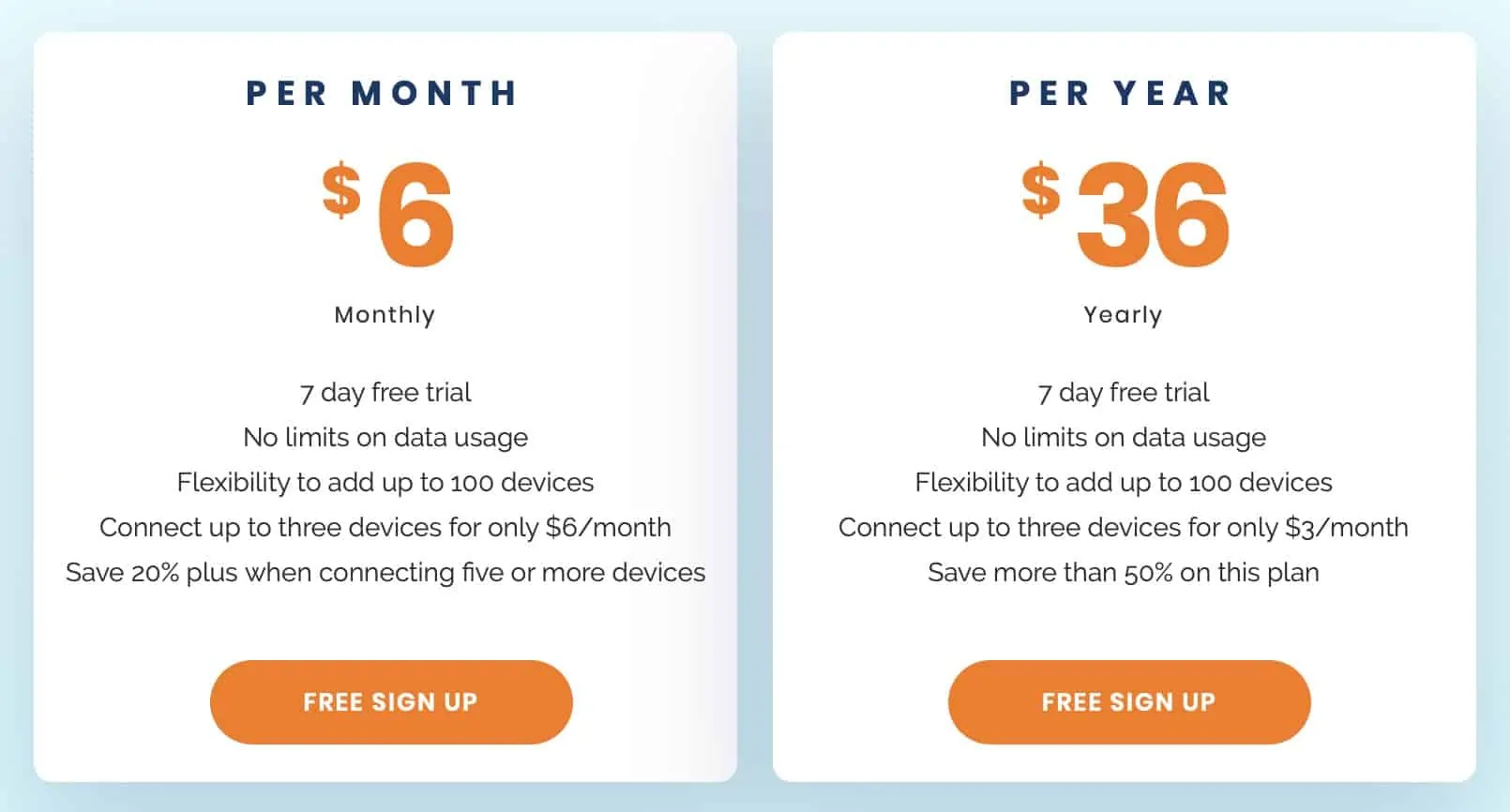
Private Tunnel Pricing
Private Tunnel’s prices are fair. While $6.00 per month (GBP £4.54) is a little bit high, their yearly plan for $36.00 (GBP £27.27) is a very good deal at $3.00 (GBP £2.27) a month.
Private Tunnel also offers a seven-day free trial. You do need to register a credit card to get the free trial, but as long as you cancel before the seven days are up, your card won’t be charged.
One thing to keep in mind, however, that at the prices listed above, Private Tunnel will only allow you to make up to three simultaneous connections. If you want more, you’ll need to pay more.
Here’s a breakdown of the costs if you raise the simultaneous connections limit:
- 3 devices / $6.00 per month / $36.00 per year (GBP £4.54/£27.27)
- 5 devices / $8.00 per month / $48.00 per year (GBP £6.06/£36.37)
- 10 devices / $13.00 per month / $78.00 per year (GBP £9.85/£59.10)
- 25 devices / $26.00 per month / $156.00 per year (GBP £19.70/£118.20)
You can go up to over 100 devices but I think I’ll stop here. Those types of plans are obviously for business accounts.
Do I recommend Private Tunnel?
No, I don’t. And for quite a few reasons.
First off, Private Tunnel provides essentially no features to its users beyond access to a small OpenVPN VPN server network and a vague malware blocker.
That means, no VPN protocols other than OpenVPN. No kill switch, no split tunneling, no streaming support, no torrenting support, no router support. That’s not exactly an award-winning performance, right?
Add to the mix its old-fashioned website, its unclear terms of service, and the lack of any concrete information on how its service actually works, and you really end up with something you can’t recommend in good faith.
Still, let’s look at the positives before moving on.
Private Tunnel’s speeds are good and stable. I didn’t experience any disconnects and my online gaming experience was very smooth. A malware blocker, however vaguely defined, is still welcome. It just feels as if Private Tunnel tried to launch a VPN service but gave up at one point. That’s what it feels like—and the fact that my support email never got an answer kind of reinforces that feeling.
Private Tunnel alternatives
NordVPN
NordVPN is a very well-known Panama-based VPN service. It provides a wealth of features for security, privacy, and convenience. Ad-blocking, DNS leak protection, robust encryption, and VPN kill switch have you covered on the security front. A strict no-logging policy, a thoughtful Privacy Policy, and anonymous payments have your back for privacy. Dedicated P2P servers, native apps for every major platform, and up to six simultaneous connections (or more with a VPN router) make NordVPN a very user-friendly service.
Surfshark
Surfshark is another provider worth looking at. I believe it to be the cheapest VPN service I’ve seen, with subscriptions starting at only $1.99/month (GBP £1.50). Surfshark only supports secure protocols and works with streaming services. It adheres to its strict no-logging policy and works in China. Surfshark also allows an unlimited number of simultaneous connections. Definitely worth checking out.
ExpressVPN
ExpressVPN is one of the larger players in the commercial VPN market and benefits from an excellent reputation. Its privacy and security practices are extremely good. All of the VPN servers run from volatile memory (RAM) and are booted from read-only disks. This setup essentially guarantees that no remnant data (logs) can exist on the system’s hard drives, which is great for user privacy. ExpressVPN is a little more expensive than most providers out there, but it’s fast, secure, it unblocks streaming sites, and it works in China.
Methodology used for testing
Below you’ll find the criteria used to assess the VPNs we review. It’s essential to be consistent across the board so that our reviews are reasonably objective and that we’re not comparing apples to oranges. For that reason, we want to expose our criteria.
- Speed – Speed is one of the most critical factors of any VPN. Aside from being frustrating, slow speeds can prevent you from streaming or even browsing the web. To make sure we address this issue, all of our recommended VPNs scored very high in our most recent speed tests.
- Apps & ease of use – More people than ever are using VPNs today. So app design and how easy it is to understand and use is critical. We look at the client apps’ UI, the features they provide, the supported operating systems, and their complexity.
- Streaming services – Accessing streaming sites over VPN is becoming rather tricky. But many VPN providers claim to work with streaming sites—with varying degrees of success. We test VPNs against a range of popular streaming services, including Netflix, Amazon Prime Video, BBC iPlayer, HBO Max, Disney+, Hulu, and more, before recommending a VPN provider for streaming.
- Torrenting – P2P file-sharing has been around for a long time, and it’s still going strong. But not all VPN providers allow torrenting over their network, while others go as far as providing dedicated P2P servers. We look at each VPN’s policy around torrenting and run tests on those that do to see how well they handle file-sharing.
- Security & privacy – This is pretty much a VPN’s raison d’être. What is the provider’s privacy policy like? What is its logging policy? What encryption protocols does the VPN support? Does it use robust ciphers? Does it support Perfect Forward Secrecy (PFS)? Is it vulnerable to IP or DNS leaks? These are all crucial questions, and we provide answers to all of them when assessing VPNs’ privacy and security practices.
The above represents a high-level view of our methodology. If you’d like more details, have a look at our full VPN testing methodology. This data-driven approach helps us better understand the services to recommend the right VPN to the right users.
Serve traffic through a private tunnel
Learn how to serve traffic from your local network over a private tunnel.
Introduction
At the end of this tutorial, you’ll have a a secure TLS public endpoint using your own DNS and domain, which you can use to access your internal services or webpages.
I’ll show you how to:
- automate a tunnel server on a public cloud provider with inlets pre-loaded onto it,
- how to connect a client from your home or private network
- how to tunnel one or more services
- and what else you can do
In a previous article, I explained some of the differences between SaaS and self-hosted tunnels.
Create your tunnel server
With a private tunnel like inlets, you need to create a tunnel server. It has a public IP address that you can use to accept traffic and proxy it into your private network.
Pictured: Inlets Conceptual architecture
The simplest way to do this is to use the inletsctl tool, which supports around a dozen clouds. The alternative is to set up a VPS or install inlets-pro onto a server you already have set up, and then add a systemd unit file so that it restarts if the tunnel or server should crash for any reason.
To see a list of supported clouds run:
inletsctl create --help For instructions on how to create an API key or service account for each, feel free to browse the docs.
inletsctl create \ --region lon1 \ --provider digitalocean \ --access-token-file ~/digital-ocean-api-key.txt \ --letsencrypt-domain blog.example.com \ --letsencrypt-email [email protected] A VM will be created in your account using the cheapest plan available, for DigitalOcean this costs 5 USD / mo at time of writing.
You can also run your tunnel server in the free tier of GCP, Oracle Cloud or on Fly.io at no additional cost.
Once the tunnel server has been created, you will receive:
- The IP address
- An endpoint for the inlets client to connect to
- A token for the inlets client to use when connecting
Take a note of these.
Now create a DNS “A” record for the IP address of the tunnel server on your domain control panel.
Personally, I’m a fan of Google Domains and the .dev domains, but DigitalOcean can also manage domains through their CLI:
export IP="" export SUBDOMAIN="blog.example.com" doctl compute domain create $SUBDOMAIN \ --ip-address $IP How does the TLS encryption work?
The inlets server process will attempt to get a TLS certificate from Let’s Encrypt using a HTTP01 Acme challenge.
What if I have multiple sites?
You can pass a number of sub-domains, for instance:
--letsencrypt-domain blog.example.com \ --letsencrypt-domain grafana.example.com \ --letsencrypt-email [email protected] Connect your tunnel client
The tunnel client can be run as and when required, or you can generate a systemd unit file so that you can have it running in the background. You can run the tunnel on the same machine as the service that you’re proxying, or you can run it on another computer. It’s entirely up to you.
So you could have a Raspberry Pi which just runs Raspberry Pi OS Lite and an inlets client, and nothing else. In this way you’re creating a kind of router appliance.
Let’s imagine you’ve run a Node.js express service on your computer:
$ git clone https://github.com/alexellis/alexellis.io \ --depth=1 $ cd alexellis.io/ $ npm install $ npm start alexellis.io started on port: http://0.0.0.0:3000 inlets also has its own built-in file-server with password protection and the ability to disable browsing for sharing private links. You can expose the built-in file-server when you want to share files directly, without having to upload them first: The simple way to share files directly from your computer
You can download the inlets client using the inletsctl tool:
$ sudo inletsctl download Now you can start the tunnel client and start serving a test version of my personal homepage alexellis.io :
$ export URL="" $ export TOKEN="" $ inlets-pro http client \ --url $URL \ --token $TOKEN \ --upstream blog.example.com=http://127.0.0.1:3000 What if my services are running on different computers?
If they are all within the same network, then you can run the client in one place and have it point at the various internal IP addresses.
$ inlets-pro http client \ --url $URL \ --token $TOKEN \ --upstream blog.example.com=http://127.0.0.1:3000 \ --upstream grafana.example.com=http://192.168.0.100:3000 If they are on different networks, you can simply run multiple clients, just change the –upstream flag on each client.
How can I run the client in the background?
For Linux hosts, you can generate a systemd unit file for inlets by using the –generate systemd flag to the client or server command.
Then simply copy the resulting file to the correct location on your system and install it:
$ export URL="" $ export TOKEN="" $ inlets-pro http client \ --url $URL \ --token $TOKEN \ --upstream blog.example.com=http://127.0.0.1:3000 \ --license-file=$HOME/.inlets/LICENSE \ --generate=systemd > inlets.service $ sudo cp inlets.service /etc/systemd/system/ $ sudo systemctl enable inlets You can then check the logs or service status:
$ sudo journalctl -u inlets $ sudo systemctl status inlets Access your website over the tunnel
You can now access your local website being served at http://127.0.0.1:3000 over the tunnel by visiting the domain you created:
Checking the status of the tunnel server
You can check the status of your tunnel server with the inlets-pro status command:
$ export URL="" $ export TOKEN="" $ inlets-pro status \ --url $URL \ --token $TOKEN Server info: Hostname: creative-pine6 Started: 1 day Mode: http Version: 0.8.9-rc1 Connected clients: Client ID Remote Address Connected Upstreams 4e35edf5c6a646b79cc580984eac4ea9 192.168.0.19:34988 5 minutes example.com=http://localhost:8000, prometheus.example.com=http://localhost:9090 A Grafana dashboard can be set up to monitor your tunnel server itself, plus any services that you expose get metrics collected automatically.
Your IP goes where you go
You can close the lid on your laptop, and open it again in Starbucks or your favourite local independent coffee shop. As soon as you reconnect the client, your local server will be available over the tunnel at the same IP address and domain: https://blog.example.com/
I used this technique to test a live demo for the KubeCon conference. I then took a flight from London to San Diego and was able to receive traffic to my Raspberry Pi whilst tethering on a local SIM card.
Tethering my Raspberry Pi with K3s in San Diego
Wrapping up
In a very short period of time we created a private tunnel server on a public cloud of our choice, then we created a DNS record for it, and connected a client and accessed our local website.
When would you need this?
- If you’re self-hosting websites, you already have some equipment at home, so it can work out cheaper.
- If you’re running a Kubernetes cluster or K3s on a Raspberry Pi, it can be much cheaper over the course of a year.
- But it’s also incredibly convenient for sharing files and for testing APIs or OAuth flows during development.
Ben Potter at Coder is writing up a tutorial on how to access a private VSCode server from anywhere using a private tunnel. If you would like to learn more, follow @inletsdev for when it gets published.
“I prefer to play around with different projects without having to worry about my costs skyrocketing. I had a few Raspberry Pis and wondered if I could use them as a cluster. After a bit of searching #k3s and inlets gave me my answer”
Andrew’s K3s cluster, with inlets
You may also like
- Tunnel a service or ingress from Kubernetes
- Share a file without uploading it through inlets tunnels
- Connecting my boat to the Internet with inlets
Subscribe for updates and new content from OpenFaaS Ltd.
By providing your email, you agree to receive marketing emails.
How to use private tunnel
Об этой странице
Мы зарегистрировали подозрительный трафик, исходящий из вашей сети. С помощью этой страницы мы сможем определить, что запросы отправляете именно вы, а не робот. Почему это могло произойти?
Эта страница отображается в тех случаях, когда автоматическими системами Google регистрируются исходящие из вашей сети запросы, которые нарушают Условия использования. Страница перестанет отображаться после того, как эти запросы прекратятся. До этого момента для использования служб Google необходимо проходить проверку по слову.
Источником запросов может служить вредоносное ПО, подключаемые модули браузера или скрипт, настроенный на автоматических рассылку запросов. Если вы используете общий доступ в Интернет, проблема может быть с компьютером с таким же IP-адресом, как у вас. Обратитесь к своему системному администратору. Подробнее.
Проверка по слову может также появляться, если вы вводите сложные запросы, обычно распространяемые автоматизированными системами, или же вводите запросы очень часто.