Cryptography Demystified: Protecting Your Digital Privacy
If she had chosen to use a reputed website, which has encrypted transactions and employs cryptography, this iPhone enthusiast could have avoided this particular incident. This is why it’s never recommended to visit unknown websites or share any personal information on them.
What Is Cryptography? Definition & How It Works
Learn how Adaptive Multi-Factor Authentication combats data breaches, weak passwords, and phishing attacks.
Updated: 04/21/2022 – 12:27
Time to read: 9 minutes
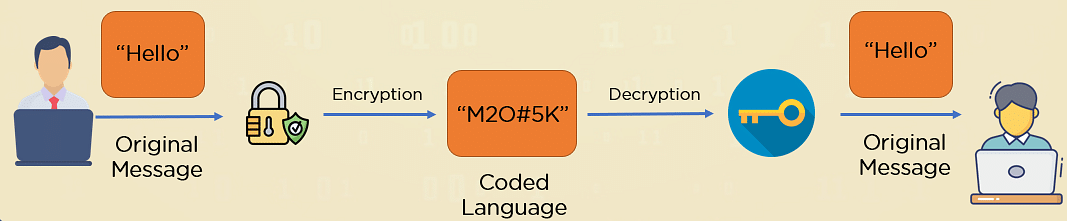
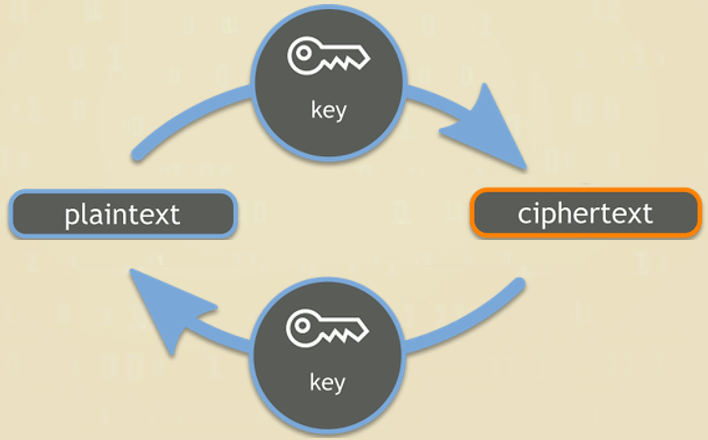
Modern cryptography is a method of sending and receiving messages that only the intended receiver and sender can read — to prevent third-party access. It often involves encryption of electronic data, which commonly creates ciphertext by scrambling regular text. Then, it uses a decryption key of some form to return it to readable format on the receiving end. Cryptography can involve either a symmetric key system, which is the simplest, or an asymmetric key system, which is typically more secure. Cryptography provides methods for secure communication and electronic data that malicious adversaries cannot read, interpret, or access.
What is cryptography?
Cryptography is used to keep messages and data secure from being accessible to anyone other than the sender and the intended recipient. It is the study of communications and a form of security for messaging. Ultimately, cryptography can keep data from being altered or stolen. It can also be used to authenticate users. Cryptography often uses encryption and an algorithm to keep electronic data and messages secure and only readable by the intended parties. Cryptography has been around for centuries. The term itself comes from the Greek word kryptos, which translates to hidden. Today, cryptography is based on computer science practices and mathematical theory.
Types of cryptography
There are two main types of cryptography used for digital data and secure messages today: symmetric cryptography and asymmetric cryptography. Hash functions, a third type, doesn’t involve use of a key.
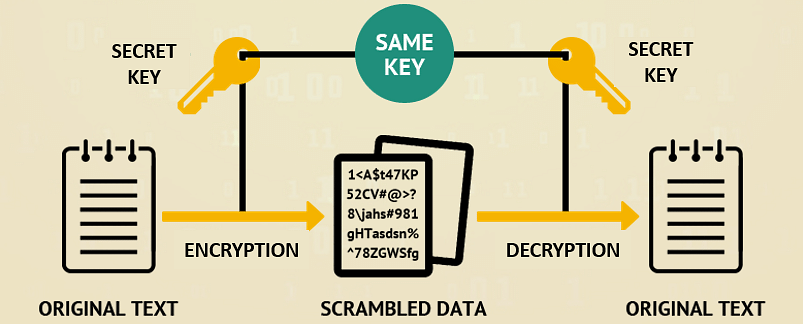
- Symmetric cryptography: This is one of the most commonly used and simplest forms of encrypting and decrypting electronic data. It is also called secret-key or private-key cryptography. With symmetric cryptography, both the sender and the recipient will have the same key. This key is used to encrypt messages and data on one end and then decrypt it on the other end. Before communications begin, both parties must have the same secret key. Symmetric cryptography is fast, easy to use, and best suited for transmitting large amounts of data or for bulk encryption. The issue with this form of cryptography is that if a third party gets the secret key, they too can read and decrypt the data or messages. There are two main forms of symmetric encryption algorithms: stream and block algorithms.
- Stream algorithm: This type encrypts the data while it is being streamed; therefore, it is not stored in the system’s memory. One of the most popular stream ciphers is the RC4 (Rivest Cipher 4), which encrypts messages one byte at a time.
- Block algorithms: This type encrypts specific lengths of bits in blocks of data using the secret key. The data is held within the system’s memory while blocks are completed. The Advanced Encryption Standard (AES) is the most commonly used symmetric algorithm. Blocks of 128-bit data are encrypted and decrypted using cryptographic keys of 128, 192, and 256 bits. The AES is FIPS (Federal Information Processing Standards) approved under guidance from NIST (National Institute of Standards and Technology).
What is cryptography used for?
The intention of cryptography is to keep data and messages secure and inaccessible to potential threats or bad actors. It is often working behind the scenes to encrypt and decrypt data you are sending through social media, applications, interactions on websites, and email. Symmetric cryptography can be used for these purposes:
- Card transactions and payment applications
- Random number generation
- Signature verification to ensure the sender is who they claim to be
Asymmetric cryptography can be used for the following purposes:
- Email messages
- SIM card authentication
- Web security
- Exchange of private keys
Key principles of cryptography
Cryptography strives for private communications and data security to protect digital information from being altered, accessed, or read by anyone other than those with legitimate access. These are key principles of cryptography:
- Confidentiality: The basis of cryptography relies on the information being kept private and confidential from third-party or malicious adversaries. Confidentiality agreements contain specific guidelines and rules that are meant to ensure that information is restricted, secure, and only accessible to certain people or within certain arenas.
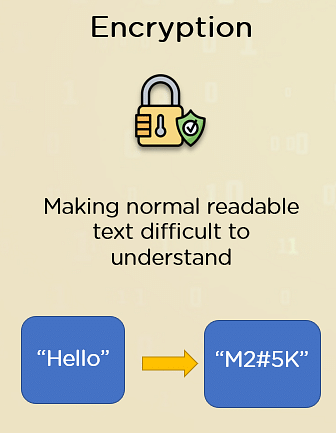
- Encryption: Encryption is what converts readable data into an unreadable form to protect the privacy as messages or data are sent between a sender and a receiver. This is typically done using an algorithm.
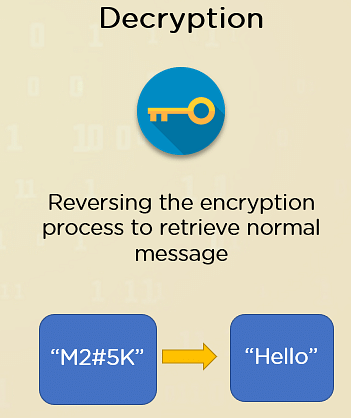
- Decryption: The reverse of encryption is decryption, and this is returning the data to its original and readable form. Typically, this is performed using a specific key, which can be the same for encryption and decryption or require two different keys.
- Data integrity: Data needs to stay consistent and accurate over its entire lifestyle, and data integrity can help to maintain this accuracy. Data cannot be altered anywhere in the communication path. It all needs to remain intact between the sender and the receiver.
- Authentication: This is to determine that the message or data received is sent from the actual originator of the message. The sender is often required to verify that they are indeed the originator of the message received by the recipient.
- Non-repudiation: This is the ability to ensure that the originator of a message or piece of data is unable to deny the authenticity of their signature. The use of digital signatures can prevent the originator or sender from denying their communication.
Best practices
Messages and data should always be encrypted to ensure privacy and security. The best practices for cryptography include using an entire cryptographic system, or cryptosystem, that regularly uses multiple forms of encryption to keep data and communications safe and secure. This system should have an easy-to-use interface along with strong cryptographic algorithms that conform to the industry’s best practices. For symmetric encryption, this means using AES with 128, 192, or 256-bit keys. For asymmetric encryption standards, it should include elliptical curve cryptography (ECC) and RSA. These are examples of files and data that should be encrypted and protected with cryptography:
- Email and messages
- Critical and sensitive files
- Company data
- Payment information
- Personal identification details
Cryptographic methods need to be effective, but also user-friendly to ensure that they are actually going to be used as intended. Using encryption functions can also help to prevent the loss or theft of data even if the hardware itself is stolen or compromised. A strong cryptosystem should be able to hold up to the security community and not rely on security through obscurity. Instead, the system should be known, and the only thing kept secret and private are the actual keys. The public key can be publicized, but the secret or private key should be protected. These are methods for keeping your keys secure:
- Do not store your encryption keys in clear text or along with the data that is encrypted.
- Store your keys in a file system protected with strong access control lists (ACLs) while adhering to the principle of least privilege — access only to those who need it.
- Use a second encryption key to encrypt your data encryption keys, generated using password-based encryption (PBE). A small number of administrators can use a password to generate a key to avoid storing the key in an unencrypted form within the system.
- Use a tamper-resistant hardware appliance called a hardware security model (HSM) that can securely store keys. When data is needed to be decrypted, code can make an application programming interface (API) call to the HSM.
Key takeaways
Cryptography is a necessary form of cybersecurity that uses encryption methods to keep digital data and communications secure and out of the hands of potential threats or bad actors. Data protection is highly important in this digital era where so much information is stored on computers, in the cloud, and on the internet. Data security is important to businesses, industries, companies, and individuals alike. Cryptography is a form of securing digital data and messages often using special keys that only the sender and recipient have access to. Cryptography uses mathematical systems and algorithms to encrypt and decrypt data. Symmetrical cryptography uses the same key for both encryption and decryption. It can quickly encrypt and decrypt data, and it is easy to use. It can also be compromised if a third party gains access to the key, however. It is important to keep your data encryption keys safe and secure. Sending your encryption key in a plain text form along with your encrypted message, for example, is similar to leaving your front door key in plain sight in front of your locked door. Keep your keys safe to keep your data safe. Asymmetrical cryptography is a step further than symmetrical cryptography, using different keys for encryption and decryption. The encryption key is “public,” and everyone has access to it. The decryption key is kept “private,” and only intended recipients can have access to this secret key. While this adds an extra layer of security, it can also take longer to encrypt and decrypt data, so it is regularly used for smaller bits of data. A strong cryptosystem often uses multiple forms of encryption and cryptographic methods to keep digital data private and secure from adversaries. Cryptography is a vital component of digital security.
References
Security Component Fundamentals for Assessment. (2020). Security Controls Evaluation, Testing, and Assessment Handbook (Second Edition).
Advanced Encryption Standard (AES). (2001). National Institute of Standards and Technology (NIST).
Elliptical Curve Cryptography ECC. (June 2020). National Institute of Standards and Technology (NIST).
Cryptography Demystified: Protecting Your Digital Privacy
Today’s digital space has become flooded with doubts regarding the safety of personal information and privacy, in general. Some of these concerns have been taken care of, thanks to the adoption of cryptography and encryption. Here, you will learn about cryptography and the various aspects of it. The topics covered in this tutorial on ‘What is Cryptography’ are:
- What is the need for Cryptography?
- What is Cryptography?
- What are the Applications of Cryptography?
- What are the Different Categories in Cryptography?
- Historical Significance of Cryptography
- Demo on Cryptography
- How can Simplilearn help you?
What Is the Need for Cryptography?
Take a look at the following story to understand the need for Cryptography.
Take the example of Anne. Anne wants to look for a discount on the latest iPhone. After browsing the internet, she comes across a questionable website willing to offer a 50% discount on the first purchase.
However, a few moments after she provides her payment details, the website withdraws a huge chunk of money from her account. Anne then wonders how she had failed in realizing that the website was a scam. She then notices that the website is an HTTP webpage instead of HTTPS.
The payment information submitted was not encrypted and visible to anyone keeping an eye, including the website owner.
If she had chosen to use a reputed website, which has encrypted transactions and employs cryptography, this iPhone enthusiast could have avoided this particular incident. This is why it’s never recommended to visit unknown websites or share any personal information on them.
This is where Cryptography comes to play, and is so essential. Now you’ll go through exactly what cryptography is.
Become an Expert in the Cyber Security Field
Post Graduate Program In Cyber Security Explore Program
What is Cryptography?
Cryptography is the science of encrypting or decrypting information to prevent unauthorized access. In cryptography, you transform data and personal information to make sure only the correct recipient can decrypt the message. As an essential aspect of modern data security, using cryptography allows the secure storage and transmission of data between willing parties.
Here are a few terminologies which will help you understand what cryptography is, with better clarity.
There are two primary aspects of cryptography, they are:
1. Encryption
Encryption is the process of scrambling the information, to avoid third parties from comprehending the message even if it is intercepted. This scrambling is done using specific mathematical calculations and steps, often collectively known as ciphers. Along with the cipher, it uses an encryption key to encrypt the message.
2. Decryption
The second part of the cryptography process is decryption. Decryption is the process of reversing the work done by encryption. It converts the scrambled information into its original form so that the data is readable again. Usually, the encryption key which is used to scramble the data can decrypt the data, but that varies depending on the type of cryptography used. Irrespective of whether or not they are the same, a key is mandatory for both the encryption and decryption of data.
In the next section of this tutorial titled ‘what is cryptography’, you will go through an example as to how you can use keys to encrypt data.
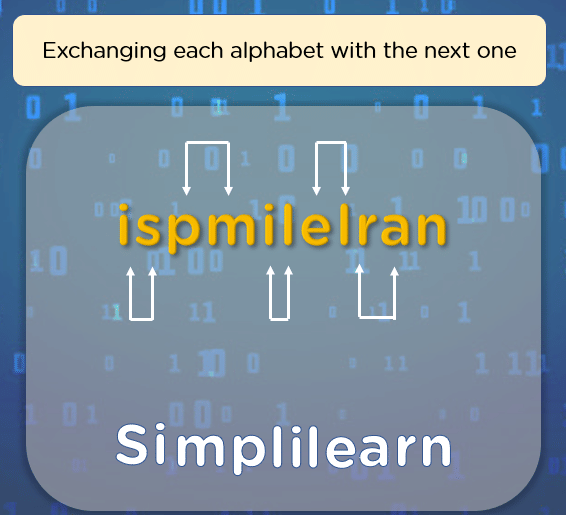
For example, jumble up the alphabets in the word ‘Simplilearn’ and someone without the necessary information cannot guess the original message just by looking at the ciphertext.
You can only understand the word if you know how to decrypt the coded word, thereby reversing the work done by encryption to get back the plaintext.
Taking the above example as reference, before the original message is encrypted, it is called cleartext or plaintext. After it encrypts the plaintext using the encryption key, the coded message is called the ciphertext. It can then pass the same ciphertext through the decryption key and return to the cleartext/plaintext format.
Now that you understand the ‘what is cryptography’ bit and its essential functions, look at its importance and worldwide applications.
What Are the Applications of Cryptography?
Cryptography finds use in many areas, ranging from safety in payment portals, to secure messaging platforms like WhatsApp. A few of those applications are as follows –
1. SSL/TLS Encryption:
Browsing the internet is secure today primarily because cryptography has allowed you to encrypt your data flow. Starting from browser identification to server authentication, encryption and cryptography, in general, have simplified online browsing.
2. Digital Signatures:
With digital contracts gaining prominence, the world was in the need of a secure channel to pass critical documents through. Cryptography helps provide a layer of authentication so you can be certain regarding the origin, confidentiality, and integrity of your documents.
3. Safe Online Banking:
Online banking services and payment applications would be an afterthought, if not for encryption of data. Cryptography has enabled authentication systems to verify the identity of certain individuals before allowing them to hold transactions and help reduce credit card fraud in the process.
4. Secure Chatting Services:
Messaging applications like WhatsApp, Telegram, and Signal have now adopted an end-to-end encryption protocol, which guarantees that no one other than the sender and receiver can read the messages. This is a huge step up from SMS days, where security was always a toss-up. Thanks to cryptography, there are a plethora of communication platforms to make use of.
5. Encrypted Emails:
With a vast amount of private information passing through your inbox, having a secure method of communication is an absolute necessity. Thanks to encryption algorithms like PGP (Pretty Good Privacy), your emails are now encrypted at all times.
6. Crypto-Currency:
With blockchain technology, cryptocurrency has seen an astronomical increase in interest rates and is still one of today’s most sought-after trade markets. A completely decentralized, secure, and tamper-proof system has found its way into today’s digital sphere, thanks to cryptography.
With so many different avenues where cryptography has found its place, its implementation is distinct. In the next section on ‘what is cryptography’, you will understand how to go ahead with it.
What Are the Different Categories in Cryptography?
Cryptography can be broadly classified into three different types –
- Symmetric Key Cryptography
- Asymmetric Key Cryptography
- Hashing
1. Symmetric Key Cryptography
Symmetric key cryptography is the category where the same key is used for both the encryption and decryption of information.
This type of encryption is used when data rests on servers and identifies personnel for payment applications and services. The potential drawback with symmetric encryption is that both the sender and receiver need to have the key, and it should be secret at all times.
For example, as seen from the image below, if Alice wants to send a message to Bob, she can apply a substitution or shift cipher to encrypt the message, but Bob must be aware of the same key so that he can decrypt it when necessary.
Symmetric key algorithms use one of the two types of Ciphers –
- Stream Ciphers – The plaintext is converted to ciphertext bit-by-bit, one at a time.
- Block Ciphers – The plaintext is broken down into blocks/chunks of data encrypted individually and later chained together.
The most widely used Symmetric Key Algorithms are AES (Advanced Encryption Standard), DES (Data Encryption Standard), 3DES (Triple DES), Twofish, etc.
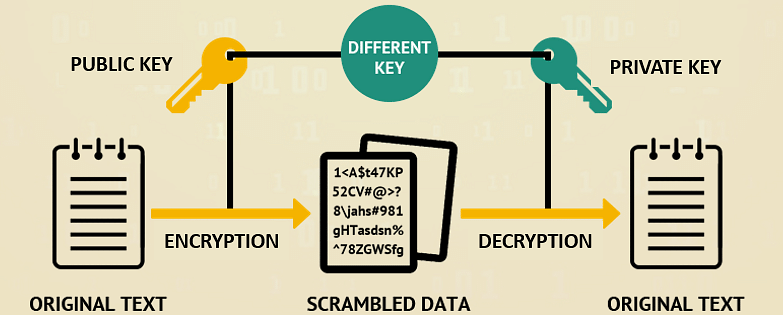
2. Asymmetric Key Cryptography
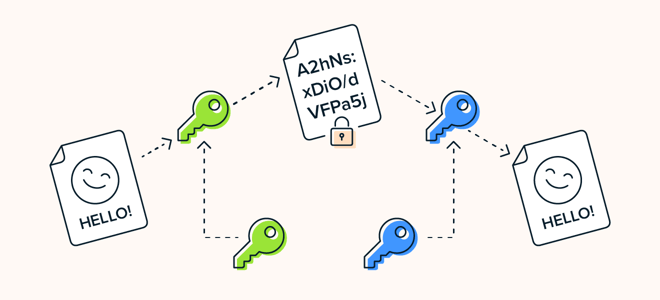
In asymmetric key cryptography, there are two keys at play. A public key and a private key. The public key is used to encrypt the data pre-transit, and the private key is used to decrypt the data post-transit.
If Alice wants to communicate with Bob using Asymmetric encryption, she encrypts the message using Bob’s public key. After receiving the message, Bob uses his private key to decrypt the data. This way, nobody can intercept the message in between transmissions, and they don’t need a secure key exchange for this to work.
RSA encryption is the most widely used asymmetric encryption standard today. Named after its founders (Rivest, Shamir, and Adleman), it uses block ciphers that separate the data into blocks and obscure the information.
On many occasions, it is advised to use a combination of symmetric and asymmetric to achieve better speed and security. In the image below, you see the process of using both symmetric and asymmetric encryption to transfer information and secret keys privately.
Follow the procedure as explained below:
Step 1: Encrypt the original message using symmetric key cryptography.
Step 2: Encrypt the key used in step one using the receiver’s public key i.e. using asymmetric key cryptography.
Step 3: Send both the encrypted message and encrypted symmetric key to the receiver.
Step 4: The receiver uses his private key to decrypt the symmetric key used to encrypt the original message.
Step 5: The decrypted key is used to convert the encrypted message back to plaintext.
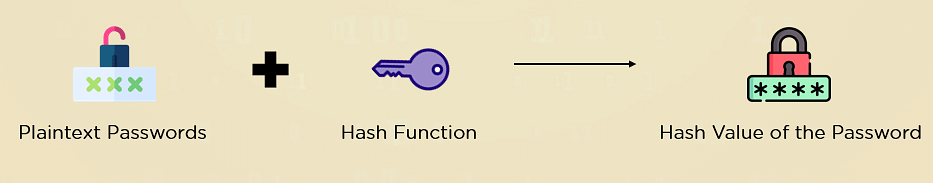
3. Hashing
Hashing is the branch of cryptography that scrambles data beyond recognition. However, unlike symmetric and asymmetric key cryptography, hashing isn’t designed to be reversible. It gives an output of a fixed size, known as the hash value of the original data.
You can use hash functions to scramble the data. They are not reversible and the output size of a hash function is always the same, irrespective of the size of the plaintext.
It is to be noted that cryptography isn’t entirely limited to the 21st century. There have been several occasions in history where cryptography has helped create secure channels of communication. This tutorial on ‘what is cryptography’ will take you through two such examples in the next section.
Historical Significance of Cryptography
The two most famous examples of cryptography in ancient times are –
1. Caesar Cipher:
Julius Caesar used a substitution shift to move alphabets a certain number of spaces beyond their place in the alphabet table. A spy cannot decipher the original message at first glance.
For example, if he wanted to pass confidential information to his armies and decides to use a substitution shift of +2, A becomes A+2=C, B becomes B+2=D, and so on. This cipher has been appropriately named Caesar cipher, which is one of the most widely used algorithms.
2. Enigma Machine:
The Nazi German armies used to have a machine called the Enigma during the era of the world wars. It was used to protect confidential political, military, and administrative information. It consisted of 3 or more rotors that scramble the original message typed, depending on the machine state at the time.
The decryption process is similar, but it needs both machines to stay in the same state before passing the ciphertext to give out the plaintext message.
Now you will go through how modern-day cryptography has helped in keeping the data secure on the internet with a demonstration of what is cryptography.
Clear CompTIA, CEH, and CISSP Certifications!
Cyber Security Expert Master’s Program Explore Program
Demo on Cryptography
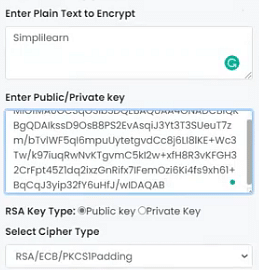
For this demo on what is cryptography, there is a web-based tool (https://www.devglan.com/online-tools/rsa-encryption-decryption) that will help you understand the process of RSA encryption. As you already probably know, the RSA encryption algorithm falls under the umbrella of asymmetric key cryptography, which implies that you have two keys at play here, the public key and the private key.
You have the choice of key size in RSA, which allows you to prioritize either speed or added complexity, depending on the requirements. Here, choose the key size as 1028 bits and generate the key pair for this example.
Now, try and encrypt the word Simplilearn in this example. You have to select if the key which is being used for encryption is private or public. Since that affects the process of scrambling the information. Since you are using the public key, select the same. You also have the option of using modified ciphers, but stick to plain RSA for the time being.
With the above parameter set, encrypt the data.
You have to generate your ciphertext that is to be sent to the recipient of the message.
The receiver must already possess the private key generated from the same pair. No other private key can be used to decrypt the message. You must paste the private key here and select the same.
The cipher must also match the one used during the encryption process.
Once you click decrypt, you can see the original plaintext.
This sums up the entire process of RSA encryption and decryption.
You can also use the private key for decryption and the public key for decryption, but the appropriate checkbox must be enabled for it to work flawlessly, as shown in the image below.
While this dealt with mostly theoretical concepts, have a look at a real-time example.
Here, you are going to use the software called Wireshark, which helps in analyzing network traffic from your system, so you can see what kind of data enters and leaves the machine.
Consider the website Wikipedia. Pretty standard HTTPS website where the S stands for secured. Analyze the traffic passing through the network when you use the website.
You can see that there are a lot of applications running, and you see a lot of requests, so you apply a filter that only shows results for the requests generated and requested by Wikipedia. Once done, analyze some of the data packets.
As you can see, there is a bunch of gibberish data here that reveals nothing you searched or read. Similarly, other secured websites function this way and it’s very difficult if at all possible, to snoop on user data.
To put this in perspective, consider an HTTP website (http://www.demo.amitjakhu.com/login-form/) that has a login form.
You need to apply similar filters in Wireshark and enter some random credentials to test the manner of data transfer. Have a look at the data packets being sent to the website in this case.
As you can see from the image above, the credentials you entered are visible to anyone monitoring your network traffic. In this case, the password was deliberately wrong, but on scam websites that ask for payment details, this can be very damaging to anyone who is either misinformed regarding HTTP websites or just missed it in general.
That brings an end to the tutorial titled ‘what is cryptography’.
How Can Simplilearn Help You?
The importance of symmetric key cryptography in today’s internet sphere and its value in safeguarding our privacy and security is clear. With many bases to cover in the world of cybersecurity, cryptography is crucial, even though there are multiple more topics essential to excel in, as a cybersecurity expert.
Simplilearn offers a “Cybersecurity Expert” course designed to equip you with all the skills necessary to start or promote your career in cybersecurity. It doesn’t have any academic pre-requirements, and the introductory module will prepare beginners for the course ahead. Training for highly sought-after certifications like CompTIA Security+, CEH, CISM, and CISSP are at the forefront of this course, preparing you for the best jobs being offered in the industry.
Looking forward to a career in Cyber Security? Then check out the Certified Ethical Hacking Course and get skilled. Enroll now!
Conclusion
Through this tutorial, you have received an understanding of why cryptography is essential, what is cryptography, its categories, and applications, all the way to its real-life implementation with a demonstration. Though not perfect, cryptography has managed to provide a secure environment for our daily information to travel through and prevent cybercrime as much as possible. To learn more on this topic, you can watch the video on what is cryptography, here: https://www.youtube.com/watch?v=rjWx39mB4Sc
Hope this tutorial on ‘What is Cryptography’ has been helpful to you. If you have any questions, please feel free to ask in the comments section, and we will be happy to answer them.
About the Author
Simplilearn
Simplilearn is one of the world’s leading providers of online training for Digital Marketing, Cloud Computing, Project Management, Data Science, IT, Software Development, and many other emerging technologies.
What Is Cryptography and How Does It Work?
For thousands of years, cryptography has been used to hide and protect secret messages. In today’s digital world, cryptography helps secure communications and data as it travels through the internet. Learn what cryptography is and how it keeps information safe online. Then, install a VPN to get automatic encryption and ironclad privacy whenever you log on.
Copy article link
Link Copied
Written by Deepan Ghimiray
Published on September 30, 2022What is cryptography?
Cryptography is the use of mathematical concepts and rules to secure information and communications. Derived from the Greek word kryptos, which means hidden, the definition of cryptography refers to converting intelligible text into unintelligible text, and vice versa. Cryptographic techniques allow only a message’s sender and intended recipient to read the decoded contents.
Types of cryptography
There are three cryptography types, which are distinguished by the types of cryptographic algorithms they use to scramble data. Most types of cryptography use algorithms called keys that scramble and unscramble, or code and decode, data.
Here are the different types of cryptography:
- Secret Key Cryptography: A secret key is used to both encrypt and decrypt the data. The sender includes the secret key in the coded message sent to the intended recipient. If the message is intercepted, the included key can decode its contents.
- Public Key Cryptography: The sender uses a public key to encrypt the message, and the receiver uses a private key to decrypt it. If the message is intercepted, the contents can’t be deciphered without the private key.
- Hash Functions: Hash functions don’t rely on keys. Instead, they scramble data of varying size into values of uniform length. With hash functions, both a one-word message and a 1000-page novel create a fixed-sized output of encoded text (called a hash value), making it nearly impossible to determine the original content. Commonly using the MD5 hashing algorithm, hashing is often used for authentication purposes.
How does cryptography work?
Cryptography works by taking plaintext (or cleartext) and scrambling it into ciphertext, so that the encoded output can be understood only by the intended recipient. As ciphertext, the information should be unreadable to all except the intended recipient.
In cybersecurity, encryption is most often used to scramble plaintext into ciphertext — while decryption reverses the process. The best encryption software uses complicated cryptographic algorithms that are incredibly difficult to crack.
In asymmetric encryption, a public key is used to encrypt a message and a private key is used to decrypt it.
The exact technique used to scramble plaintext into ciphertext defines how cryptography works. Symmetric encryption, asymmetric encryption, blockchain, and digital signatures are some prominent encryption techniques. Hashing, another cryptographic process, is not technically encryption, since it doesn’t use keys.
Use of cryptography
Cryptography is used to keep communications and information private. Protecting data with cryptography helps minimize threats like ransomware attacks, because if hackers intercept information, they won’t be able to understand it without a decryption key.
Here are some common uses of cryptography:
- Financial transactions and online banking: Online banking and ecommerce websites use advanced encryption techniques to keep financial information safe.
- SSL-secured websites: A website with an SSL certificate creates a secure, encrypted connection to protect information passing from your browser to the website’s server.
- VPNs: A VPN is a security tool that redirects web traffic through a private server and encrypts the connection.
Though you can enable Wi-Fi encryption on your router settings, you need a VPN if privacy and security are truly important to you. VPN encryption methods vary, depending on which VPN protocol is used — for example the WireGuard VPN protocol is one of the most recent, while the OpenVPN protocol is perhaps the most common.
Shop, stream, and browse the web with bank-grade encryption
Encrypted internet connections keep our personal data secure while we surf the web. Avast SecureLine VPN features bank-grade encryption to protect all your online communications and keep your activity private. Get automatic encryption at the click of a button today with Avast.