Types of Encryption: Symmetric or Asymmetric? RSA or AES
The block ciphers are schemes for encryption or decryption where a block of plaintext is treated as a single block and is used to obtain a block of ciphertext with the same size. Today, AES (Advanced Encryption Standard) is one of the most used algorithms for block encryption. It has been standardized by the NIST (National Institute of Standards and Technology) in 2001, in order to replace DES and 3DES which were used for encryption in that period. The size of an AES block is 128 bits, whereas the size of the encryption key can be 128, 192 or 256 bits. Please note this, there is three length in the key, but the size of the encryption block always is 128 bits. Block cipher algorithms should enable encryption of the plaintext with size which is different from the defined size of one block as well. We can use some algorithms for padding block when the plaintext is not enough a block, like PKCS5 or PKCS7, it also can defend against PA attack, if we use ECB or CBC mode. Or we can use the mode of AES which support a stream of plaintext, like CFB, OFB, CTR mode.
The difference in five modes in the AES encryption algorithm
Recently, I did some work with Sawada-san on the TDE. So I studied on the encryption algorithm. So far, I study five modes in the AES. In this document, I will introduce the difference in the five kinds of mode.
General
The block ciphers are schemes for encryption or decryption where a block of plaintext is treated as a single block and is used to obtain a block of ciphertext with the same size. Today, AES (Advanced Encryption Standard) is one of the most used algorithms for block encryption. It has been standardized by the NIST (National Institute of Standards and Technology) in 2001, in order to replace DES and 3DES which were used for encryption in that period. The size of an AES block is 128 bits, whereas the size of the encryption key can be 128, 192 or 256 bits. Please note this, there is three length in the key, but the size of the encryption block always is 128 bits. Block cipher algorithms should enable encryption of the plaintext with size which is different from the defined size of one block as well. We can use some algorithms for padding block when the plaintext is not enough a block, like PKCS5 or PKCS7, it also can defend against PA attack, if we use ECB or CBC mode. Or we can use the mode of AES which support a stream of plaintext, like CFB, OFB, CTR mode.
Now let’s introduce the five modes of AES.
- ECB mode: Electronic Code Book mode
- CBC mode: Cipher Block Chaining mode
- CFB mode: Cipher FeedBack mode
- OFB mode: Output FeedBack mode
- CTR mode: Counter mode
The attack mode:
- PA: Padding attack
- CPA: Chosen Plaintext Attack
- CCA: Chosen Ci
ECB Mode
The ECB (Electronic Code Book) mode is the simplest of all. Due to obvious weaknesses, it is generally not recommended. A block scheme of this mode is presented in Fig. 1.
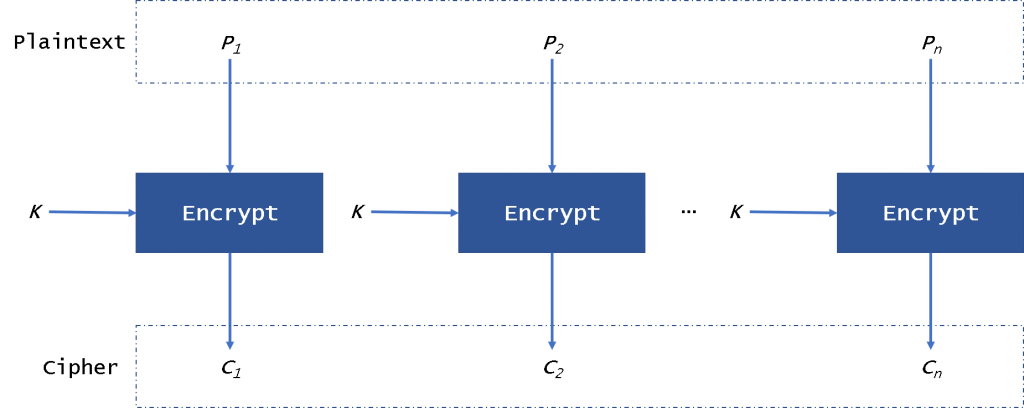
We can see it in Fig. 1, the plaintext is divided into blocks as the length of the block of AES, 128. So the ECB mode needs to pad data until it is same as the length of the block. Then every block will be encrypted with the same key and same algorithm. So if we encrypt the same plaintext, we will get the same ciphertext. So there is a high risk in this mode. And the plaintext and ciphertext blocks are a one-to-one correspondence. Because the encryption/ decryption is independent, so we can encrypt/decrypt the data in parallel. And if a block of plaintext or ciphertext is broken, it won’t affect other blocks.
Because of the feature of ECB, the Mallory can make an attack even if they don’t get the plaintext. For example, if we encrypt the data about our bank account, like this: The ciphertext: C1: 21 33 4e 5a 35 44 90 4b(the account) C2: 67 78 45 22 aa cb d1 e5(the password) Then the Mallory can copy the data in C1 to C2. Then he can log in the system with the account as the password which is easier to get.
In the database encryption, we can use ECB to encrypt the tables, indexes, wal, temp files, and system catalogs. But with the issues of security, we don’t suggest to use this mode.
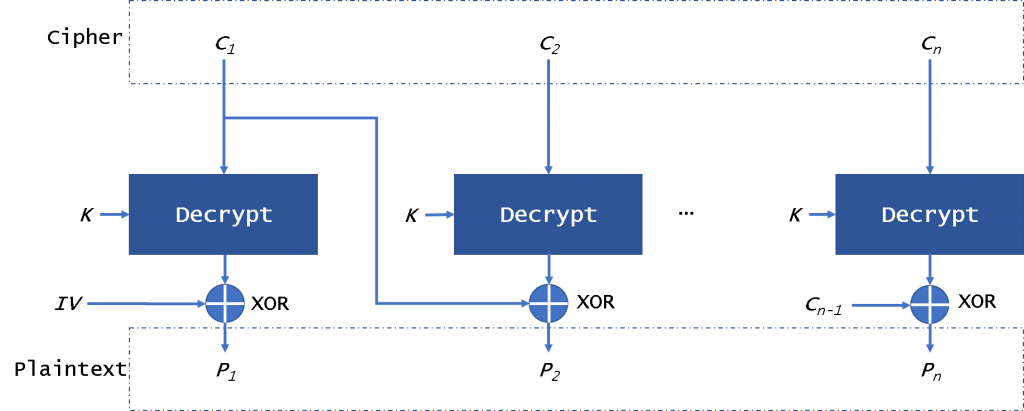
CBC mode
The CBC (Cipher Block Chaining) mode (Fig. 2) provides this by using an initialization vector – IV. The IV has the same size as the block that is encrypted. In general, the IV usually is a random number, not a nonce.
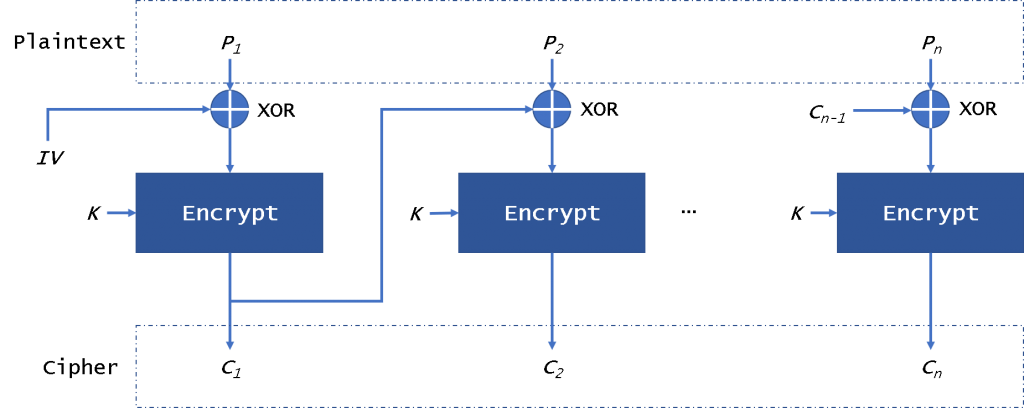
We can see it in figure 2, the plaintext is divided into blocks and needs to add padding data. First, we will use the plaintext block xor with the IV. Then CBC will encrypt the result to the ciphertext block. In the next block, we will use the encryption result to xor with plaintext block until the last block. In this mode, even if we encrypt the same plaintext block, we will get a different ciphertext block. We can decrypt the data in parallel, but it is not possible when encrypting data. If a plaintext or ciphertext block is broken, it will affect all following block.
A Mallory can change the IV to attack the system. Even if a bit is wrong in the IV, all data is broken. Mallory also can make a padding oracle attack. They can use a part of ciphertext to pad the ciphertext block. This will return some messages about the plaintext. It is safe from CPA, but it is easily sysceptible to CCA and PA.
To ensure security, we need to change the key when we encrypt 2^((n+1)/2)(n is the length of a block).
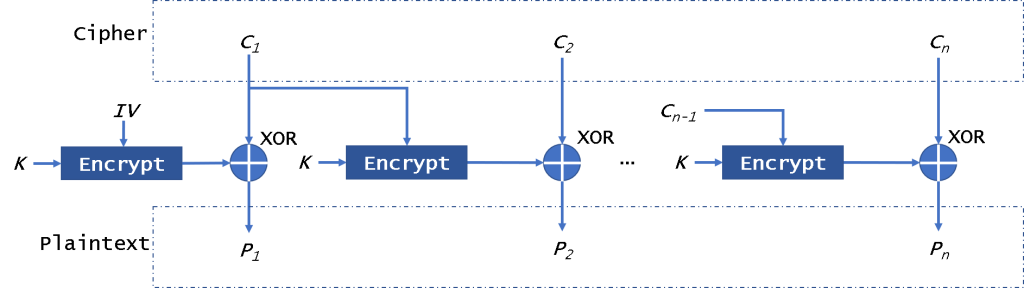
CFB mode
The CFB (Cipher FeedBack) mode of operation allows the block encryptor to be used as a stream cipher. It also needs an IV.
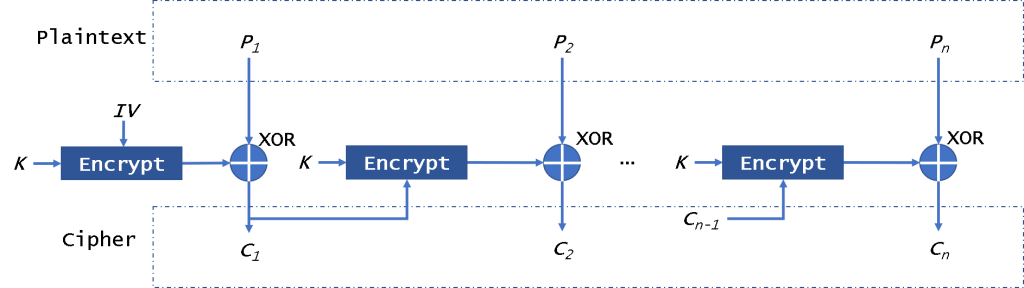
First, CFB will encrypt the IV, then it will xor with plaintext block to get ciphertext. Then we will encrypt the encryption result to xor the plaintext. Because this mode will not encrypt plaintext directly, it just uses the ciphertext to xor with the plaintext to get the ciphertext. So in this mode, it doesn’t need to pad data.
And it could decrypt data in parallel, not encryption. This mode is similar to the CBC, so if there is a broken block, it will affect all following block.
This mode can be attacked by replay attack. For example, if you use the other ciphertext to replace the new ciphertext, the user will get the wrong data. But he will not know the data is wrong. It is safe from CPA, but it is easily sysceptible to CCA.
To ensure security, the key in this mode need to be changed for every 2^((n+1)/2) encryption blocks.
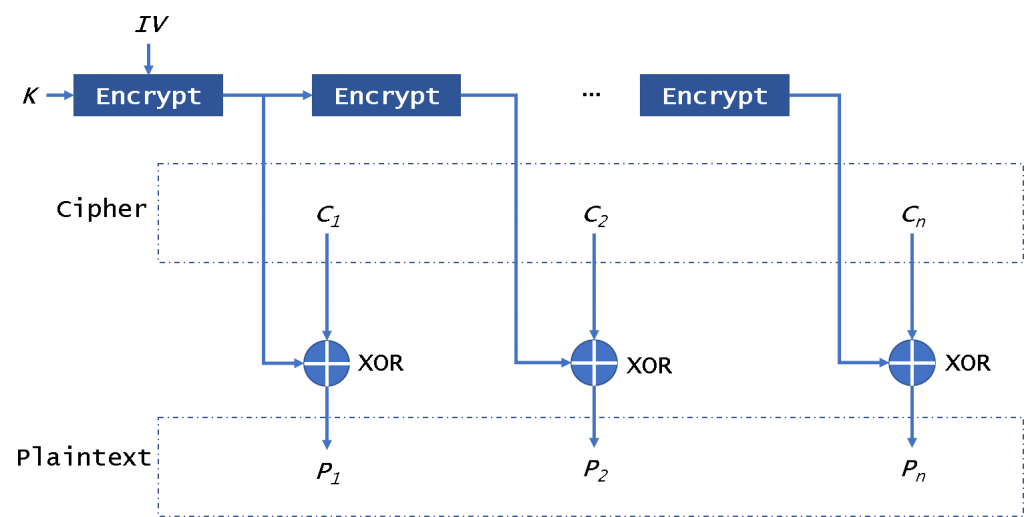
OFB mode
The OFB (Output FeedBack) mode of operation (Fig. 4) also enables a block encryptor to be used as a stream encryptor. It also doesn’t need padding data.
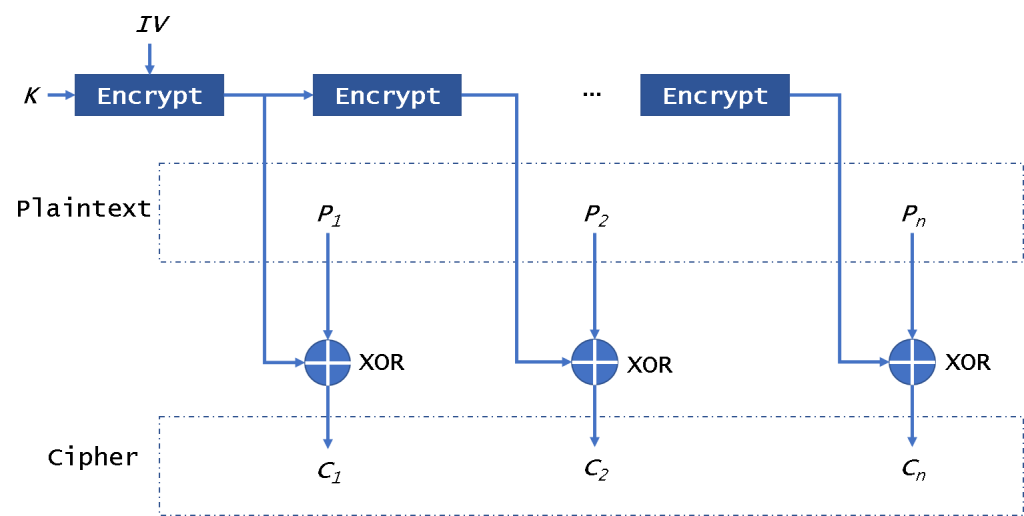
In this mode, it will encrypt the IV in the first time and encrypt the per-result. Then it will use the encryption results to xor the plaintext to get ciphertext. It is different from CFB, it always encrypts the IV. It can not encrypt/decrypt the IV in parallel. Please note that we won’t decrypt the IV encryption results to decrypt data. It will not be affected by the broken block. It is safe from CPA, but it is easily sysceptible to CCA and PA.
A Mallory can change some bits of ciphertext to damage the plaintext.
To ensure security, the key in this mode need to be changed for every 2^(n/2) encryption blocks.
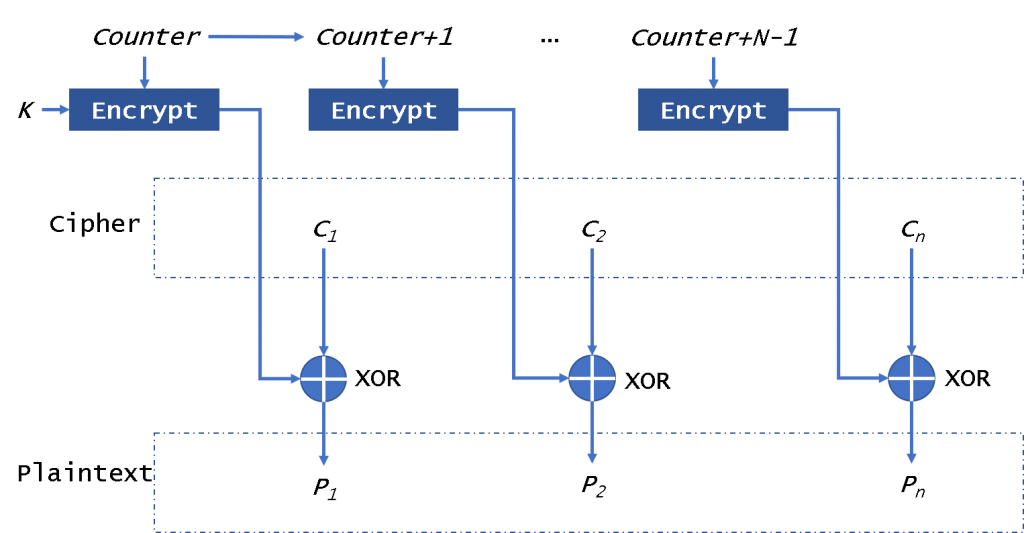
CTR mode
At the CTR (Counter) mode of operation, shown in Fig. 5, as an input block to the encryptor (Encrypt), i.e. as an IV, the value of a counter (Counter, Counter + 1,…, Counter + N – 1) is used. It also is a stream encryptor.
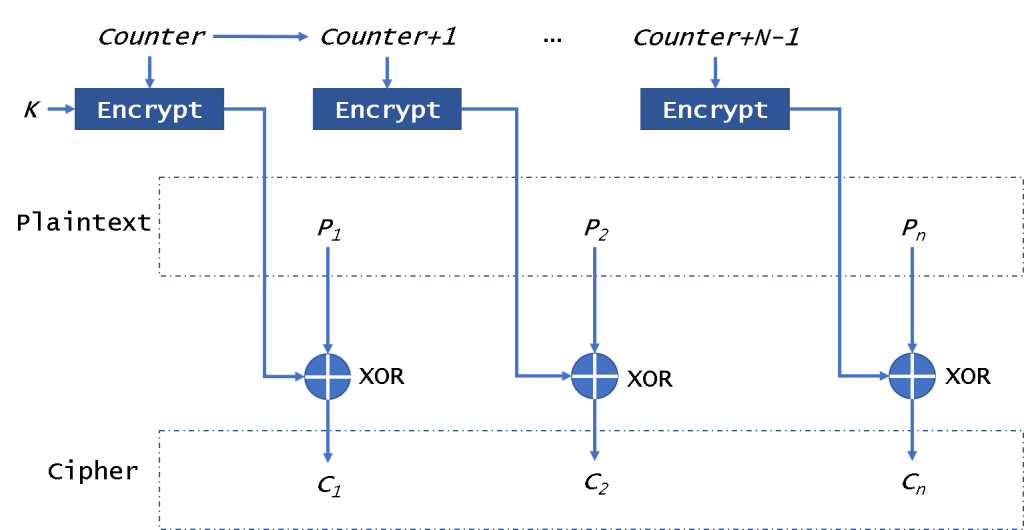
The counter has the same size as the used block. As shown in Fig. 5, the XOR operation with the block of plain text is performed on the output block from the encryptor. All encryption blocks use the same encryption key. As this mode, It will not be affected by the broken block. It is very like OFB. But CTR will use the counter to be encrypted every time instead of the IV. So if you could get counter directly, you can encrypt/decrypt data in parallel.
A Mallory can change some bits of ciphertext to break the plaintext. In the database encryption, we can use CBC to encrypt all the files.
To ensure security, the key in this mode need to be changed for every 2^(n/2) encryption blocks.
Summary
Which is the database needs?
| Object name | alignment | Parallel write | Parallel read | Encryption Mode |
|---|---|---|---|---|
| Indexes | yes | yes | yes | CTR |
| WAL | no | no | no | CFB, OFB, CTR |
| System catalogs | no | no | yes | CBC, CTR, CFB |
| Temporary files | yes | no | no | CBC, CTR, CFB, OFB |
| Tables | yes | no | yes | CBC, CTR, CFB |
In the end, I think the CTR mode is the best mode for PostgreSQL.
Shawn Wang is a developer of PostgreSQL Database Core. He has been working in HighGo Software for about eight years.
He did some work for Full Database encryption, Oracle Compatible function, Monitor tool for PostgreSQL, Just in time for PostgreSQL and so on.
Now he has joined the HighGo community team and hopes to make more contributions to the community in the future.
Types of Encryption: Symmetric or Asymmetric? RSA or AES?
If you’re looking to encrypt data to protect it, you might find there are different encryption methods and encryption algorithms to pick from. From RSA to AES, your pick should be informed by context.
June 15, 2021
Symmetric vs asymmetric is a comparison that’s often used in the world of cryptography and computer security. Symmetric encryption involves using a single key to encrypt and decrypt data, while asymmetric encryption uses two keys – one public and one private – to encrypt and decrypt data. Each type of encryption has its own strengths and weaknesses, and the choice between the two depends on the specific needs of the user.
In popular culture, the concept of symmetric vs asymmetric encryption is often explored in movies and TV shows that involve hacking and espionage. For example, in the TV show “Mr. Robot,” the protagonist Elliot uses asymmetric encryption to protect his data from hackers and other adversaries.
What is Data Encryption?
Data Encryption is a process that can be as easy as flipping on a switch if you know what you’re looking to achieve. Let’s recap the basics of this data security asset. To encrypt data is to take a piece of information, and translate it into another piece of unrecognizable information. This end product is called a ciphertext.
To get a ciphertext, you run the information that is to be encrypted through an encryption algorithm. This algorithm takes the original information and, based on randomized rules, transforms the information into a new, undecipherable piece of data. Think of it as a ‘translation’.
What the encryption algorithm does is create a new language, and hide sensitive data by transforming it into this secret code, which you can only decrypt and turn back to plaintext if you know the rules, or what’s called a key. The key represents the mathematical steps the algorithm took to convert your text from “Hello World” into “XJtg920kl#aJFJ”%*¨*FK”. Without it, you can’t decrypt the data, and thus it is protected from unauthorized access.
Types of Encryption Systems
There are many different types of encryption algorithms and methods to pick from, so how do you know which one is the safest pick for your cybersecurity needs? Let’s begin with the most common types of encryption systems: symmetric vs asymmetric encryption.
Symmetric Encryption
In this type of encryption, there is only one key, and all parties involved use the same key to encrypt and decrypt information. By using a single key, the process is straightforward, as per the following example: you encrypt an email with a unique key, send that email to your friend Tom, and he will use the same symmetric key to unlock/decrypt the email.
What is a Symmetric Key?
A symmetric key is one that may be used to encrypt and decode data. This implies that in order to decrypt information, the same key that was used to encrypt it must be utilized. In practice, the keys represent a shared secret shared by two or more people that may be utilized to maintain a confidential information link.
Exploring symmetric encryption examples in everyday technologies
Symmetric encryption is a widely used method for securing data across various applications, providing confidentiality and integrity. By utilizing a single key for both encryption and decryption, symmetric encryption examples showcase the technique’s speed and efficiency in protecting sensitive information. From securing online communications to encrypting sensitive files, symmetric encryption remains a vital component of modern cybersecurity.
Three practical symmetric encryption examples:
- Secure messaging apps (e.g., WhatsApp, Signal): These messaging platforms use symmetric encryption, such as the Signal Protocol, to ensure that messages are encrypted end-to-end, allowing only the intended recipients to read the content.
- File encryption software (e.g., VeraCrypt, AxCrypt): Symmetric encryption algorithms like AES are employed by file encryption software to protect sensitive data stored on devices, ensuring data remains secure even if the device is lost or stolen.
- BitLocker: When you activate BitLocker on a Windows computer to encrypt all hard drives. By unlocking the PC with his/her passcode, the user will decrypt data without the risk of exposing its secret encryption key.
Asymmetric Encryption
Asymmetric encryption, on the other hand, was created to solve the inherent issue of symmetric encryption: the need of sharing a single encryption key that is used both for encrypting and decrypting data.
What is an Asymmetric Key?
Asymmetric keys are the cornerstone of Public Key Infrastructure (PKI), an encryption technique that requires two keys, one to lock or encrypt the plaintext and another to unlock or decrypt the cyphertext. Neither key performs both functions.
This newer and safer type of encryption method utilizes two keys for its encryption process, the public key, used for encryption, and the private key used for decryption. These keys are related, connected, and work in the following way:
A public key is available for anyone who needs to encrypt a piece of information. This key doesn’t work for the decryption process. A user needs to have a secondary key, the private key, to decrypt this information. This way, the private key is only held by the actor who decrypts the information, without sacrificing security as you scale security.
Exploring Asymmetric Encryption Examples in Everyday Technologies
Asymmetric encryption plays a critical role in modern-day cybersecurity, providing confidentiality, integrity, and authentication in various applications. By using public and private key pairs, asymmetric encryption examples are found across a range of industries and technologies, demonstrating its importance in securing digital information. This versatile encryption method has become an essential tool for safeguarding sensitive data and ensuring secure communications.
Three practical asymmetric encryption examples:
- Secure email communications (e.g., PGP, S/MIME): Asymmetric encryption is utilized in secure email communication protocols such as Pretty Good Privacy (PGP) and Secure/Multipurpose Internet Mail Extensions (S/MIME). These protocols leverage public and private keys to encrypt email content, ensuring only the intended recipient with the correct private key can decrypt and read the message. This method provides confidentiality and maintains message integrity.
- Digital signatures for document authenticity and integrity (e.g., Adobe Sign, DocuSign): Asymmetric encryption is also used in digital signature services like Adobe Sign and DocuSign. When a user signs a document digitally, their private key is used to create a unique signature. The recipient can then verify the authenticity and integrity of the document using the sender’s public key. This process ensures the document hasn’t been tampered with and confirms the identity of the signer.
- Secure key exchange and establishment in SSL/TLS protocol for secure websites: Asymmetric encryption plays a vital role in the Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols, which are used to secure data transmission between a user’s browser and a website. During the initial handshake process, asymmetric encryption is used for the secure exchange of a symmetric encryption key, which is then used to encrypt and decrypt data for the remainder of the session. This approach combines the security advantages of asymmetric encryption with the speed of symmetric encryption for efficient and secure communication.
Symmetric vs Asymmetric Encryption
Asymmetric and symmetric encryption are two primary techniques used to secure data. Symmetric encryption uses the same key for both encryption and decryption, while asymmetric encryption uses a pair of keys: a public key for encryption and a private key for decryption. ELI5: Imagine symmetric encryption as a single key that locks and unlocks a treasure chest, while asymmetric encryption uses two keys—a key to lock (public) and a different key to unlock (private).
Choosing between asymmetric vs symmetric encryption can be a difficult choice, so here are some key differences:
- Speed: Symmetric encryption is generally faster than asymmetric encryption, as it requires less computational power, making it suitable for encrypting large amounts of data.
- Key distribution: In symmetric encryption, secure key distribution is crucial, as the same key is used for both encryption and decryption. Asymmetric encryption simplifies key distribution, as only the public key needs to be shared, while the private key remains confidential.
- Key usage: Symmetric encryption uses a single shared key for both encryption and decryption, while asymmetric encryption employs a pair of keys: a public key for encryption and a private key for decryption.
- Use cases: Symmetric encryption is ideal for bulk data encryption and secure communication within closed systems, whereas asymmetric encryption is often used for secure key exchanges, digital signatures, and authentication in open systems.
- Security: Asymmetric encryption is considered more secure due to the use of two separate keys, making it harder for attackers to compromise the system. However, symmetric encryption can still provide strong security when implemented correctly with strong key management practices.
Selecting the right encryption method for your needs
Choosing between symmetric and asymmetric encryption depends on the specific security requirements and use cases. Understanding when to use symmetric vs asymmetric encryption is crucial for maintaining secure communications and protecting sensitive data. Factors such as key management, computational efficiency, and desired functionality should be considered when deciding which encryption method best suits a particular scenario.
Three practical examples of when to use symmetric vs asymmetric encryption:
- File encryption: Symmetric encryption is preferred for encrypting files due to its speed and computational efficiency, making it ideal for handling large volumes of data.
- Secure key exchange: Asymmetric encryption is commonly used for secure key exchange in protocols like SSL/TLS, ensuring that symmetric keys can be safely shared between parties without being intercepted.
- Digital signatures: Asymmetric encryption is suitable for creating digital signatures, allowing users to authenticate documents and verify their integrity using public and private key pairs.
Common symmetric encryption algorithms
Common Symmetric Encryption Algorithms are widely used in securing data and communications. Examples of these algorithms include Advanced Encryption Standard (AES), Data Encryption Standard (DES), Triple Data Encryption Standard (3DES), and Blowfish.
AES Encryption or Advanced Encryption System
AES is one of the most common symmetric encryption algorithms used today, developed as a replacement to the outdated DES (Data Encryption Standard), cracked by security researchers back in 2005. This new algorithm sought to solve its predecessor’s main weakness, a short encryption key length vulnerable to brute force.
AES encrypts information in a single block (block cipher), and does so one block at a time in what is called ’rounds’. Data is initially converted into blocks, and then these are encrypted with the key in different rounds depending on key size: 14 rounds for 256-bits, 12 rounds for 192-bits, and 10 rounds for 128-bits. The process involves a series of data manipulation and mixing steps that are done each round: substitution, transposition, mixing, column mix, and sub-bytes.
Blowfish and TwoFish
Blowfish was another symmetric successor to DES, designed as a block cipher like AES but with a key length that goes from 32 bits to 448 bits. It was designed as a public tool, not licensed and free. This initial version was upgraded to TwoFish, an advanced version of the latter, which utilizes a block size of 128-bits, extendable up to 256-bits.
The main difference with other encryption algorithms is that it utilizes 16 rounds of encryption, independently of the key or data size.
The main reason why TwoFish is not considered the top symmetric algorithm is that AES gained recognition and was quickly adopted as a standard by manufacturers, meaning it had the upper technical edge.
3DES or Triple Data Encryption Standard
Finally, the direct successor to DES is 3DES or Triple Des. This symmetric algorithm is an advanced form of the deprecated DES algorithm that uses a 56-bit key to encrypt blocks of data. Its concept is simple: it applies DES three times to each block of information, tripling the 56-bit key into a 168-bit one.
Due to applying the same process thrice, 3DES is slower than its more modern counterparts. Furthermore, by using small blocks of data, the risk of decryption by brute force is higher.
Common Asymmetric Encryption Algorithms
Common asymmetric encryption algorithms are essential in secure communication and data transmission. Examples of these algorithms include RSA, Diffie-Hellman, and Elliptic Curve Cryptography (ECC).
RSA or Rivest–Shamir–Adleman
Considered a staple of asymmetric encryption. Designed by the engineers that gave it its name in 1977, RSA uses the factorization of the product of two prime numbers to deliver encryption of 1024-bits and up to 2048-bit key length. According to research conducted in 2010, you would need 1500 years of computational power to crack its smaller 768-bit version!
However, this means that it is a slower encryption algorithm. Since it requires two different keys of incredible length, the encryption, and decryption process is slow, but the level of security it provides for sensitive information is incomparable.
ECC or Elliptic Curve Cryptography
This method was originally pitched in 1985 by Neal Koblitz and Victor S. Miller, only to be implemented years later in 2004. ECC uses a fairly difficult mathematical operation based on elliptic curves on a finite field, in what is called the Elliptic-curve Diffie–Hellman.
With ECC you have a curve, defined by a math function, a starting point (A), and an ending point (Z) in the curve. The key is that to get to Z, you have done a series of “hops”, or multiplications that resulted in Z. This amount of hops is the private key.
Even if you have the starting and ending point (public key), and the curve, it is nearly impossible to crack the private key. This is because ECC is what is called a “trapdoor”, or a mathematical operation that is easy and quick to complete, but extremely difficult to reverse.
ECC, or ECDH, a mathematical formula is of such strength that it can match a 1024-bit key system with security with a 164-bit key. In its highest setting, 512-bits, ECC can achieve a comparable level of security of a 15360-bit RSA key!
To paint a picture, RSA 2048-bit keys are the banking standard, yet 521-bit ECC delivers the equivalent of a 15360-bit RSA key.
Considering the aforementioned facts, ECC is considered the future of encryption. It’s asymmetric, yet it is able to provide a security level of 256 bits at a maximum key length of 521 bits, which ensures fast encryption speeds with a high complexity of decryption to ensure sensitive data stays safe.
ECC is also extremely attractive for mobile, where processing power is low and data transfers are high.
AES vs. RSA: Understanding the Key Differences
When comparing AES vs. RSA encryption methods, it is essential to understand their unique strengths and applications. While AES is a symmetric algorithm designed for rapid data encryption and decryption, RSA is an asymmetric method used primarily for secure key exchange and digital signatures. In certain scenarios, one may outperform the other, making the choice between AES and RSA crucial for optimal security and efficiency.
- Securing file storage: AES is preferable due to its faster encryption and decryption speeds, making it suitable for encrypting large amounts of data.
- Secure communications: RSA is typically used for key exchange in SSL/TLS protocols, ensuring a secure channel for data transmission between clients and servers.
- Digital signatures: RSA’s asymmetric properties make it an ideal choice for creating and verifying digital signatures, ensuring data integrity and authentication.
- Streaming services: AES is commonly used for protecting streaming content due to its performance and ability to handle real-time encryption and decryption.
- Email encryption: RSA is often used for encrypting emails, as it allows for secure key exchange, ensuring only the intended recipient can decrypt the message.
Which Data Encryption Algorithm is Best?
Well, as you can see in the comparison above, it depends. For some people, best could mean most popular, but for others it might be the cheapest one. So, instead of saying which one is the most used or has the lowest price of adoption, lest do a quick recap of all the algorithms and their best qualities:
AES (Symmetric)
AES is one of the most frequently used algorithms. It is fast, with a variable key length option that gives it extra security. It is ideal when handling large amounts of encrypted data.
TwoFish (Symmetric – previously BlowFish)
The main attraction of TwoFish is its flexibility in performance, giving you total control of the encryption speed.
3DES (Symmetric)
Despite its slower speeds and generally outdated status when compared to AES, it is still widely utilized in financial services to encrypt ATM PINs and UNIX passwords.
RSA (Asymmetric)
Since its speed isn’t convenient for processing large amounts of data, RSA encryption is mostly used in digital signatures, email encryption, SSL/TLS certificates, and browsers.
ECC (Asymmetric)
The low-cost, low-impact, high-security combination makes it the ideal standard for protecting sensitive mobiles and apps. It may likely be the algorithm of the future.
Takeaways
Encryption, a vital aspect of modern cybersecurity, can appear daunting due to its multifaceted nature. The omnipresence of data necessitates its protection across various states and scenarios, including data at rest and data in transit. One must carefully assess the access requirements, transmission methods, and the nature of interactions involving sensitive information to ensure that appropriate encryption measures are implemented, thus safeguarding confidentiality and integrity of the data.
You could be encrypting your enterprise’s communications, web browser information, e-commerce transactions, your company’s database, hard drives, or customer and user data. Taking the first step might seem difficult, but it is necessary to document all data interactions and make a plan. This way, you’ll understand what types of encryption you’ll need.
Fortunately, there are many straightforward encryption tools that are already at your disposal, ready to be activated quickly as you figure out the extent of your data security protocols. FileVault on macOS comes integrated and ready to encrypt your Mac computers with AES. Prey can help with Microsoft computers, using BitLocker and AES to provide disk encryption to your devices. It’s ideal if you have a remote workforce. The data is encrypted remotely, so you don’t have to worry about the hassle, but can keep your company safe.