Basic concepts of encryption in cryptography
For decades, attackers have attempted to decipher such keys via brute force, that is, by attempting over and over again. Cybercriminals are gradually gaining access to more powerful computational power, allowing them to obtain access to systems even when flaws exist.
What is Encryption? (Basic Concepts, Process, and Types)
Encryption is the procedure of converting data into a secret code that hides the real meaning of the data. Cryptography is the field of encrypting and decrypting information.
Encryption has long been a popular method of safeguarding sensitive data. Historically, military and governments have employed it. Encryption is used to safeguard data on computers and storage devices, as well as data in transit via networks, in modern times.
- Unencrypted data is referred to as plaintext in computing, whereas encrypted data is referred to as ciphertext.
- Encryption algorithms, often known as ciphers, are formulae that are used to encode and decode communications.
- A cipher must include a variable as part of its algorithm to be effective. The variable, known as a key, is what distinguishes a cipher’s output.
- When an unauthorized party intercepts an encrypted message, the intruder must figure out the cipher the sender used to encrypt the message and whose keys were used as variables. Encryption is a crucial security technique because of the time and complexity of guessing this information.
How Does Encryption Work?
Something as basic as “Hello, world!” might be considered original information or plain text. As an encrypted text, this may seem like something perplexing like 7*#0+gvU2x—something apparently unconnected to the plaintext
Encryption, on the other hand, is a logical process in which the person receiving the encrypted data – but not the key – can simply decode it and return it to plaintext.
For decades, attackers have attempted to decipher such keys via brute force, that is, by attempting over and over again. Cybercriminals are gradually gaining access to more powerful computational power, allowing them to obtain access to systems even when flaws exist.
When data is maintained, such as in a database, it must be encrypted “at rest,” and when it is accessed or sent between parties, it must be encrypted “in transit.”
Encryption Algorithm
A mathematical technique for converting plaintext (data) to ciphertext is known as an encryption algorithm. The key will be used by an algorithm to modify the data in a predictable manner. Even though the encrypted data appears to be random, the key may be used to convert it back to plaintext.
Blowfish, Advanced Encryption Standard (AES), Rivest Cipher 4 (RC4), RC5, RC6, Data Encryption Standard (DES), and Twofish are some of the most regularly used encryption algorithms. Encryption has progressed throughout time, from a system used primarily by governments for topsecret activities to a must-have for enterprises seeking to protect their data’s security and privacy.
Different Types of Encryption
There are several forms of encryption, each with its own set of advantages and applications.
Symmetric Encryption
Only one secret key is needed to encode and decipher information in this simple encryption method. While it is the oldest and the most well-known encryption method, it has the disadvantage of requiring both parties to have access to the key used to encrypt the data before they can decode it.
AES-128, AES-192, and AES-256 are symmetric encryption methods. Symmetric encryption is the recommended approach for transferring data in bulk as it is less difficult and also runs faster.
Asymmetric Encryption
Asymmetric encryption, often known as public-key cryptography, is a relatively recent method for encrypting and decrypting data that employs two separate but related keys. One key is private, while the other is public.
Encryption is done with the public key, while decryption is done with the private key (and vice versa). The public key does not require security because it is public and may be shared via the internet.
Asymmetric encryption is a far more powerful alternative for safeguarding the security of data delivered over the internet. Secure Socket Layer (SSL) or Transport Layer Security (TLS) certificates are used to protect websites. A request to a web server returns a copy of the digital certificate, from which a public key may be retrieved while the private key remains private.
Data Encryption Standard (DES)
DES is a deprecated symmetric key encryption technique. Because DES encrypts and decrypts messages using the same key, both the sender and the receiver must have access to the same private key. The more secure AES algorithm has supplanted DES.
In 1977, the United States government approved it as an official standard for the encryption of federal computer data. DES is widely regarded as the catalyst for the contemporary cryptography and encryption industries.
Triple Data Encryption Standard (3DES)
The Triple Data Encryption Standard (TDES) is a method of encrypting (3DES). It requires three distinct keys and three runs of the DES algorithm. 3DES was primarily considered as a temporary solution since the single DES algorithm was becoming to be seen as too weak to withstand brute force attacks, while the more powerful AES was still being tested.
Rivest-Shamir-Adleman (RSA)
RSA is a cryptosystem, a collection of cryptographic algorithms used for certain security services or purposes. It allows public-key encryption and is commonly used by browsers and virtual private networks to connect to websites (VPNs).
RSA is asymmetric, meaning it encrypts with two separate keys: one public and one private. If the public key is used for decryption, the private key is used for encryption, and vice versa.
Advanced Encryption Standard (AES)
Advanced Encryption Standard (AES) is a standard and the most secure type of encryption. AES uses “symmetric” key encryption. Advanced Encryption Standard is a symmetric encryption algorithm that encrypts fixed blocks of data (of 128 bits) at a time.
Why is it Important to Encrypt the Data?
Encryption is essential for many technologies, but it is especially critical for making HTTP requests and answers safe, as well as authenticating website origin servers. HTTPS is the protocol that is accountable for this (Hypertext Transfer Protocol Secure). A website delivered using HTTPS rather than HTTP has a URL that starts with https:// rather than http://, which is commonly indicated by a secure lock in the address bar.
Transport Layer Security (TLS) is the encryption mechanism used by HTTPS (TLS). Previously, the Secure Sockets Layer (SSL) encryption protocol was the industry standard, however, TLS has now supplanted SSL. A TLS certificate will be deployed on the origin server of a website that uses HTTPS. TLS and HTTPS are two terms that you should be familiar with.
The primary goal of Encryption is to safeguard the privacy of digital data kept on computers or communicated over the internet or any other computer network.
In addition to security, the necessity to comply with legislation is frequently a driving force for the adoption of encryption. To prevent unwanted third parties or threat actors from accessing sensitive data, a number of organizations and standard bodies either suggest or enforce encryption. The Credit Card Industry Data Security Standard (PCI DSS), for example, mandates that merchants encrypt their customers’ payment card data when it is held at rest and sent over public networks.
Key Management System
While encryption is intended to prevent unauthorized entities from understanding the data they have obtained, it can also prevent the data’s owner from accessing the data in specific circumstances. Because the keys to decrypt the encrypted text must be kept someplace in the environment, and attackers often know where to look, key management is one of the most difficult aspects of developing an enterprise encryption strategy.
There is a slew of recommended practices for managing encryption keys. It’s only that key management adds to the backup and restore process’s complexity. If a big disaster occurs, the procedure of obtaining the keys and transferring them to a new backup server may lengthen the time it takes to begin the recovery process.
It’s not enough to have a key management system in place. Administrators must devise a thorough security strategy to safeguard the key management system. This usually entails backing it up independently from everything else and keeping the backups in a method that allows you to quickly recover the keys in the case of a large-scale disaster.
How Do Attackers Crack the Encrypted Data?
Cybercriminals, hackers, and attackers employ various methods to crack the encrypted data and get access to sensitive data. Following are some of the popular methods to get unauthorized access to encrypted data −
Brute Force Attack
When an attacker doesn’t know the decryption key, they try millions or billions of guesses to figure it out. This is known as Brute Force Attack.
The most fundamental form of attack for any cipher is the Brute Force— attempting each key until the appropriate one is found. The number of viable keys is determined by the length of the key, indicating the attack’s viability. The strength of encryption is proportional to the key size, but as the key size grows, so does the resources required to conduct the computation.
With today’s computers, brute force assaults are substantially faster. Hence, encryption must be very strong and complicated. Most contemporary encryption systems, when combined with strong passwords, are immune to brute force assaults. Yet, as computers get more powerful, they may become vulnerable to such attacks in the future. Brute-force attacks can still be used against weak passwords.
Side-Channel Attack
Side-channel attacks, which attack the physical side effects of the cipher’s implementation rather than the cipher itself, are an alternative means of cracking encryptions. Such assaults can be made successful if there is a flaw in the system’s design or execution.
Cryptanalysis
Attackers may also try cryptanalysis to break a targeted cypher. It is the act of looking for a flaw in the cypher that may be exploited with a lower level of complexity than a brute-force assault. When a cypher is already weak, the task of effectively attacking it becomes easy.
The DES algorithm, for example, has been suspected of being damaged by meddling from the National Security Agency (NSA). Many believe the NSA tried to undermine alternative cryptography standards and degrade encryption products after the revelations of former NSA analyst and contractor Edward Snowden.
Basic concepts of encryption in cryptography
To make your way in the IT industry, a fundamental understanding of cryptography concepts is vital. However, many still struggle when it comes to handling TLS certificates, certificate requests, and all sorts of keys. Before I start with those, let’s talk about the basic concepts of encryption in cryptography. In this article, I explain the basics of symmetric and public key cryptography to lay a strong foundation to build on. I focus on the key concepts and leave the math to the experts.
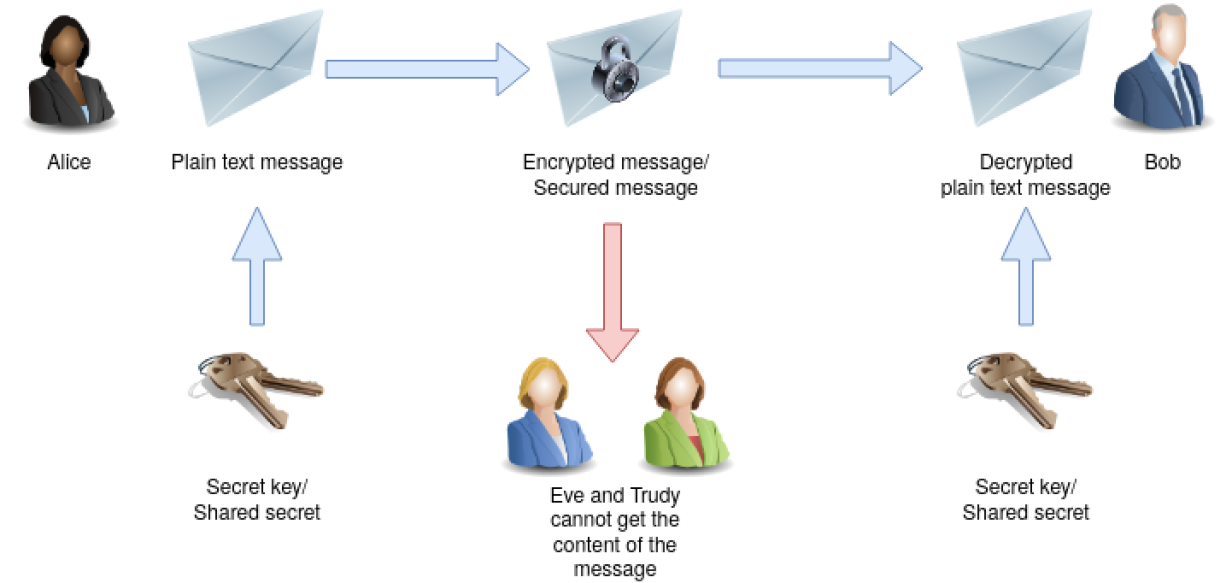
Our protagonists throughout this article are Alice, who wants to communicate with Bob over a public channel. We also have Eve and Trudy. The following techniques should make eavesdropping impossible. Messing up the content of a message shouldn’t go unnoticed.
Symmetric key cryptography
It’s called symmetric key cryptography because the same key is used to encrypt a message as to decrypt it. You could think of it as an actual key for a lock that secures your message so neither Eve nor Trudy would be able to read it or mess with it on its way to Bob.
Of course, Bob could use the same secret key/shared secret to send an encrypted message to Alice. Eve and Trudy don’t have a chance to get the plaintext from the intercepted message.
Automation advice
- Ansible Automation Platform beginner’s guide
- A system administrator’s guide to IT automation
- Ansible Automation Platform trial subscription
- Automate Red Hat Enterprise Linux with Ansible and Satellite
Symmetric key algorithms have the advantage of being pretty fast. On the downside, it’s difficult to distribute the shared secret to the communication partners. To send the key over a public (and unsecured) channel is not an option because Eve could intercept it and would be able to decrypt all future communications between Alice and Bob. The best way is for Alice and Bob to exchange the key personally face to face. Think of your teammate who is located in another country. You can guess how hard it could be to exchange the shared secret securely.
Now think of a situation where Alice and Bob are not the only participants in communication but Jason, Tyler, and Nate, too. You would have to meet them all in person for a secure key exchange.
The communication between Alice and Bob is secure as long as the shared secret stays private. If the secret key gets lost, or there is a chance that it is compromised, e.g., Eve got knowledge of it, you have to create a new key and distribute it to all communication partners again.
Think of the key to your office building, which you use for several doors in your office. When you lose it, all the locks have to be replaced, and you and your colleagues need new keys. It’s a mess. That’s the same mess when you have to renew a secret key in symmetric key cryptography.
Asymmetric cryptography
Asymmetric cryptography, or public key cryptography, solves the key distribution problem of symmetric key cryptography. It does so by using a pair of keys instead of a single one.
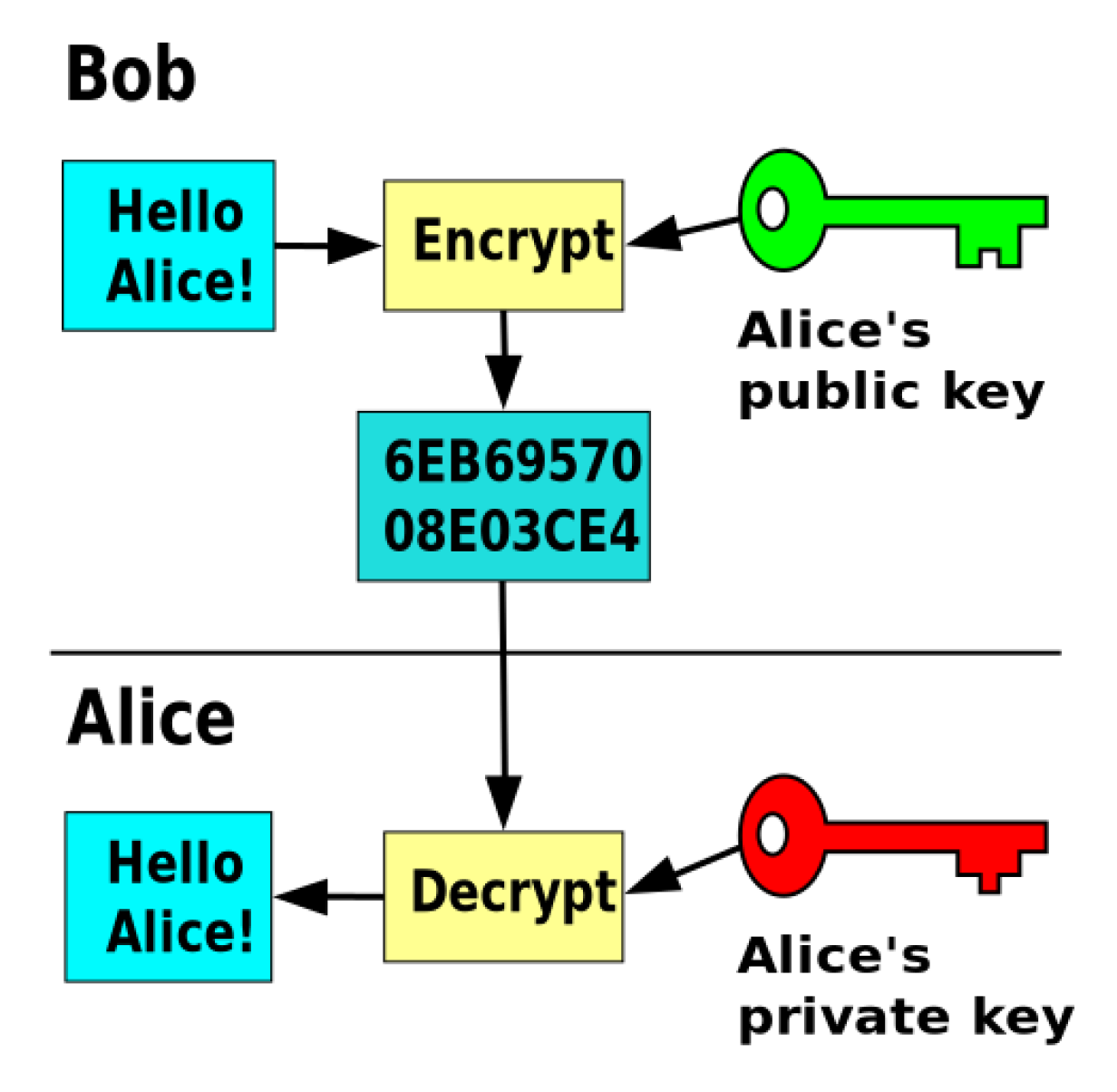
An asymmetric key algorithm is used to generate a pair of keys: A private key and a public key. As the name suggests, you should keep the private key safe and secure and share it with no one. Think of it as the key to your home. I bet you keep your eyes on this. The public key, on the other hand, is meant to be distributed publicly. You don’t have to keep it a secret and can share it with anybody. But why is that?
While the public key can encrypt a message, it is not able to decrypt it again. Only the corresponding private key can do that. If Eve and Trudy know Bob’s public key, they can use it to send an encrypted message to him. However, they cannot decrypt a message that Alice sends to Bob encrypted using the same public key. The message can only be decrypted using Bob’s corresponding private key.
When Alice and Bob want to use public key cryptography to communicate, they have to exchange their public keys and are good to go.
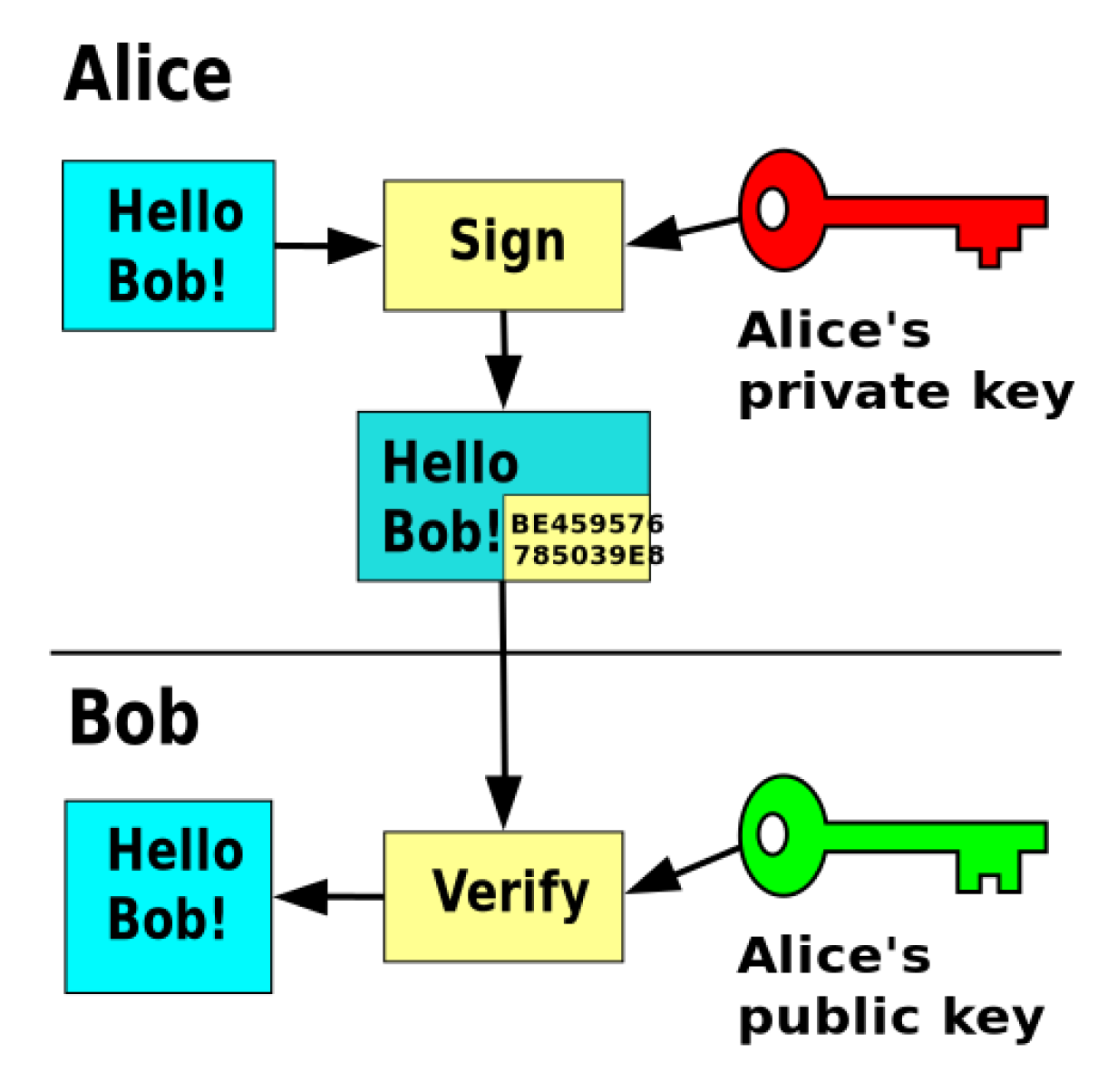
But what happens when Trudy uses Bob’s public key to send him a message in the name of Alice? How could Bob check if this message really came from Alice and wasn’t changed on the way to him? Well, Alice can use her private key to sign the message, and Bob can use Alice’s public key to check and verify the signature.
The security of public key cryptography depends on the privacy of the private key. If the private key gets compromised, you would have to generate a new pair of keys and revoke the old ones. However, it’s much easier to distribute the public key than a shared secret as you could simply send it via email.
Linux security
- What is security automation?
- Red Hat OpenShift Service on AWS security FAQ
- Enhance security with automation
- Implementing DevSecOps guide
- Red Hat CVE checker
So the distribution problem is solved. You have a way to encrypt/decrypt messages, verify the sender, and confirm a message’s integrity. Any downsides? Yes, public key algorithms are pretty slow compared to symmetric key algorithms. That’s the reason why there are some forms of hybrid techniques that use public key cryptography to exchange a symmetric session key and continue the communication using the faster symmetric key algorithm.
Wrap up
The symmetric key algorithms work pretty fast, but the distribution of the shared secret could be difficult. The security of this technique requires that every participant keeps the shared secret private. Public key algorithms are slower, but it’s much easier to distribute and exchange public keys. Remember to keep your private key safe and secure all the time.
Beginner’s guide to the basics of data encryption
To understand what data encryption means, we first need to know what data is. Data refers to any piece of information that has been translated into a binary digital format that makes it easy to be moved or processed.
The increase in smartphone usage and fast internet connectivity has led to a surge in the creation of digital data. Examples of data include text, video information, web and log activity records and audio.
The proliferation of data in governments, organizations and agencies has placed increased emphasis on data quality and integrity. As a result, individuals and organizations are now faced with the heavy task of ensuring data quality and guaranteeing that the records in use are the most accurate.
Learn Applied Cryptography
Build your applied cryptography and cryptanalysis skills with 13 courses covering hashing, PKI, SSL/TLS, full disk encryption and more.
Data breaches have become rampant these days, which is why data integrity and quality are in question. According to Statista, the number of data breaches in the U.S. has grown from 157 in 2005 to over 1,000 each of the past five years.
Is there something that can be done to control the situation?
What is data encryption?
Data encryption is one solution to mitigating the menace of data breaches that are ravaging the internet streets. Data encryption refers to the procedure or process of scrambling plaintext data into a complex undecipherable format known as ciphertext. Data encryption renders data unreadable to unauthorized parties who do not have the decryption keys.
Robust data encryption tools, combined with competent key management, can go a long way toward safeguarding data from modification, data disclosures and theft. Data encryption is thus one of the most significant elements of a cybersecurity strategy.
How does data encryption work?
Data encryption algorithms in use today go beyond simply concealing data from unauthorized parties. Data encryption ensures that the data’s origin can be authenticated and maintains its integrity throughout its transmission stage.
Encryption works by scrambling data and information into a sequence of a random and unrecognizable characters. The scrambled information is then transmitted to the receiver, who holds the decryption key to turn the ciphertext into plain text. You can see the figure below to understand more about how encryption works.
Source: ClickSSL
For example, the phrase “Nice Meeting You” can be encrypted to a ciphertext that appears like 4596 9012 11884. For the receiver to get back the “ Nice Meeting You” text, they need a decryption key.
Data encryption techniques
There are several data encryption techniques. However, three approaches appear to be more popular. These are symmetric encryption, asymmetric encryption and hashing. We will have a look at them to see how they work.
Symmetric encryption
Symmetric encryption is the most straightforward data encryption that involves a single secret key for encryption and decryption of data. The private key could be in the form of a number, letter or a string of random numbers and letters.
The secret key combines with the data in plain text to transform the contents of the information in a particular manner. Both the sender and recipient of the information must know the secret key. One of the major drawbacks of symmetric encryption is that the parties must exchange the private keys before the data can be decrypted.
Asymmetric encryption (public key)
Popularly referred to as public-key cryptography, asymmetric encryption is a relatively novel technique compared to symmetric encryption. This data encryption method uses two keys (private key and public keys) to convert plain text data into ciphertext.
In public keys, two keys are used. The public key will encrypt data, while the private key will decrypt data. It is referred to as a public key because anyone can use the key to encrypt data. No hacker can read, interpret or decipher the original information once encrypted using a public key.
The private key will be used to decrypt the data. Usually, details about the private key will be shared between the party sending the information and the party receiving the information.
Hashing
The last data encryption approach is hashing . Hashing is an encryption technique that generates a fixed-length unique signature for an information set. Data encrypted with hashing cannot be reversed back into plain text. As such, hashing is used primarily for data verification.
Many cybersecurity professionals still do not regard hashing as an encryption technique. However, the bottom line is that hashing is a perfect way of proving that the data was not tampered with in its transmission.
How to encrypt your data
Now that you know the benefits of data encryption and how data encryption works, you might be wondering what steps you should take to ensure that your data is encrypted. Data encryption comes at little or absolutely no cost. Most android phones run on full device encryption.
If you run a website, you must ensure that the website runs on the HTTPS protocol. HTTPS websites have a Secure Socket Layer. SSL certificates are one of the most crucial encryption tools that will protect your data from unauthorized access. To encrypt the in-transit data and communications between website servers and website visitors, all you need to do is purchase an SSL certificate. Usually, SSL certificates are acquired from trusted certificate providers like ClickSSL.
To encrypt a file on your computer, right-click on the file you wish to encrypt and select properties . You should then navigate to the advanced tab and select the check box designated Encrypt contents to secure data. Finally, click OK and then Apply.
The future of data encryption
Data encryption and the cybersecurity landscape are constantly transitioning to keep up with cybersecurity threats. Without data encryption, institutional data is susceptible to brute force attacks, data breaches and identity thefts.
To combat such cybersecurity threats, companies and organizations have now resolved to develop enterprise-wide encryption tactics. Over 50% of organizations have implemented at least one data encryption technique, according to the Entrust 2021 Global Encryption Trends Study.
Learn Applied Cryptography
Build your applied cryptography and cryptanalysis skills with 13 courses covering hashing, PKI, SSL/TLS, full disk encryption and more.
One of the notable emerging trends in data encryption is the bring your own key (BYOK) data encryption model. The data owner is required to use their encryption key without necessarily acquiring it from a third-party key management vendor. In addition, homomorphic encryption and quantum crypto-agile solutions are also gaining pace. Soon, we will see increased dependence on these encryption solutions.
Data encryption has proved to be one of the essential elements of data security. It can be used to reduce the risk of threats such as data breaches, man-in-the-middle attacks and many others. Data encryption should be part and parcel of your organization’s cybersecurity mix. Sensitive data should remain encrypted at all times.
Sources
- U.S. data breaches and exposed records 2005-2020 , Statista
- 2021 Global Encryption Trends Study, Entrust
Posted: August 20, 2021
Riya Sander
Riya Sander is a digital strategist, having 5+ years of experience in the field of internet marketing. She is a social media geek, a complete foodie and enjoys trying varied cuisines. A perfect day for her consists of reading her favorite author with a hot cuppa coffee.
Learn applied cryptography and cryptanalysis
What you’ll learn:
- Cryptography fundamentals
- Public key infrastructure
- Blockchain technology
- SSL and TLS
- And more
- Beginner’s guide to the basics of data encryption
- How does hashing work: Examples and video walkthrough
- How does encryption work? Examples and video walkthrough
- Planning for post-quantum cryptography: Impact, challenges and next steps
- Structures of cryptography
- Role of digital signatures in asymmetric cryptography
- What is homomorphic encryption?
- Encryption and etcd: The key to securing Kubernetes
- Quantum cyberattacks: Preparing your organization for the unknown
- An Introduction to asymmetric vs symmetric cryptography
- Breaking misused stream ciphers
- Entropy calculations
- Blockchain and asymmetric cryptography
- Security of the PKI ecosystem
- Elliptic curve cryptography
- Methods for attacking full disk encryption
- Introduction to Public Key Infrastructure (PKI)
- Introduction to the TLS/SSL cryptography protocol
- Introduction to Diffie-Hellman Key Exchange
- Introduction to the Rivest-Shamir-Adleman (RSA) encryption algorithm
- Introduction to full disk encryption
- 8 reasons you may not want to use VPNs
- Rivest Cipher 4 (RC4)
- Understanding stream ciphers in cryptography
- Cryptography Errors
- Understanding block ciphers in cryptography
- How to mitigate Credential Management Vulnerabilities
- How To Exploit Credential Management Vulnerabilities
- Poor Credential Management
- How Is Cryptography Used In Applications?
- Decrypting Downloaded Files
- Introduction to hash functions
- Introduction to Asymmetric Cryptography
- The Advanced Encryption Standard (AES)
- Fundamentals of symmetric and asymmetric cryptography
- Case Studies in Poor Password Management
- The ultimate guide to encryption key management
- Principles of cryptography
- Encryption vs Encoding
- Introduction to Cryptanalysis
- Secure Credential Management
- Introduction to Blockchain
- Blockchain Technology
- Virtual Private Networks (VPNs)
- Public Key Infrastructure: Architecture & Security
- Hash Functions
- Asymmetric Cryptography
- Fundamentals of Cryptography
- Symmetric Cryptography
- Introduction to cryptography
- Best tools to perform steganography [updated 2020]
Related Bootcamps
- (ISC)² CISSP® Training Boot Camp
- Ethical Hacking Dual Certification Boot Camp (CEH and PenTest+)
- OWASP Top 10 Training Boot Camp
- CompTIA Security+ Training Boot Camp
- Reverse Engineering Malware Training Boot Camp
Get certified and advance your career
- Exam Pass Guarantee
- Live instruction
- CompTIA, ISACA, (ISC)², Cisco, Microsoft and more!