What are risk detections
Calculated in real-time or offline. This risk detection type indicates user activity that is unusual for the user or consistent with known attack patterns. This detection is based on Microsoft’s internal and external threat intelligence sources.
Фильтрация анонимных IP
Фильтр анонимных IP-адресов Adjust поддерживает целостность данных вашего приложения, защищая его от мошеннических операций по установке, данные о которых поступают из сетей VPN, выходных узлов Tor и центров обработки данных. Он направлен на противодействие мошенникам, использующим фермы устройств и ПО эмуляции для ложных установок и получения конверсий на рынках с высокой ценностью.
Этот фильтр производит перекрестную проверку всех установок и реатрибуций вашего приложения по базе данных анонимных IP-адресов MaxMind. Любой пользователь, связанный со службой анонимизации, такой как VPN, выходной узел Tor, или с известными центрами обработки данных, атрибуцируется к Untrusted Devices . Это помогает предотвратить большую часть мошеннических атрибуций, связанных с фермами устройств и эмуляторами, еще до того, как они попадут в набор данных, а также значительно понижает эффективность тактики, основанной на манипуляциях с ЦОД.
Решение для роста :
Fraud Prevention Suite — Решение для роста от Adjust. Для активации обратитесь по адресу [email protected].
Узнайте, как настроить фильтрацию анонимных IP-адресов для вашего приложения.
Данные о фильтрации анонимных IP-адресов в отчетах
Установки, отклоненные фильтром анонимных IP-адресов, назначаются Anonymous IP – дополнительной ссылке на уровне сети «Непроверенные устройства». Также можно использовать приведенные далее показатели KPI, чтобы просмотреть отклоненные установки и реатрибуции по источнику трафика.
| В отчетах | KPI (ключевой показатель эффективности) |
|---|---|
| Отклоненная установка: анонимный IP-адрес (RI AIP) | rejected_installs_anon_ip |
| Отклоненная реатрибуция: анонимный IP-адрес (RR AIP) | rejected_reattributions_anon_ip |
FAQ
Развернуть все
Что такое сети VPN, выходные узлы Tor и центры обработки данных?
Сети VPN
Сокращение VPN обозначает виртуальную частную сеть. Одна из функций сетей VPN — предоставление пользователю возможности подключаться к Интернету с IP-адреса, который отличается от собственного адреса пользователя. Сети VPN дают пользователям возможность обходить географические ограничения на доступ к веб-сайтам и сервисам, поскольку IP-адрес такой сети может быть расположен в любой точке мира. Издатели-мошенники используют сети VPN, чтобы имитировать ситуацию, когда установки поступают из более привлекательных стран.
Выходные узлы Tor
Tor — это служба, которая перенаправляет трафик через глобальную сеть серверов с целью анонимизации личностей пользователей. Каждый сервер называется узлом, причем сеть Tor шифрует трафик, передаваемый от одного узла к другому и далее. Зашифрованный трафик выходит в Интернет через выходной узел Tor. Трафик Tor маркируется IP-адресом выходного узла сети Tor, через который он покинул сеть.
Как и в случае VPN, сеть Tor обеспечивает повышенную анонимность при доступе к Интернету. Мошенники используют эту возможность в своих интересах, чтобы изобразить, как будто их ложные установки поступают из различных географических расположений.
Центры обработки данных
Центры обработки данных из списка MaxMind не связаны с поставщиками услуг Интернета (ISP). Это означает, что любые действия пользователей, поступающие из таких ЦОД, либо являются имитацией, либо перенаправляются из другого местоположения. Обычно ЦОД используются мошенниками, которые запускают большое количество эмуляторов в этих центрах, чтобы располагать достаточными вычислительными ресурсами для своей незаконной деятельности.
Что такое эмулятор устройства?
Эмулятор устройства — это операционная система смартфона, которая запущена и выполняется на сервере, а не на смартфоне. Такое эмулируемое программное обеспечение может запускать приложения и создавать просмотры объявлений и клики посредством автоматизированного процесса. Однако важнее всего то, что за этими вовлечениями и установками не стоит реальный пользователь. Эмуляторы устройств часто запускаются в целях рекламного мошенничества.
Have a question? Get in touch
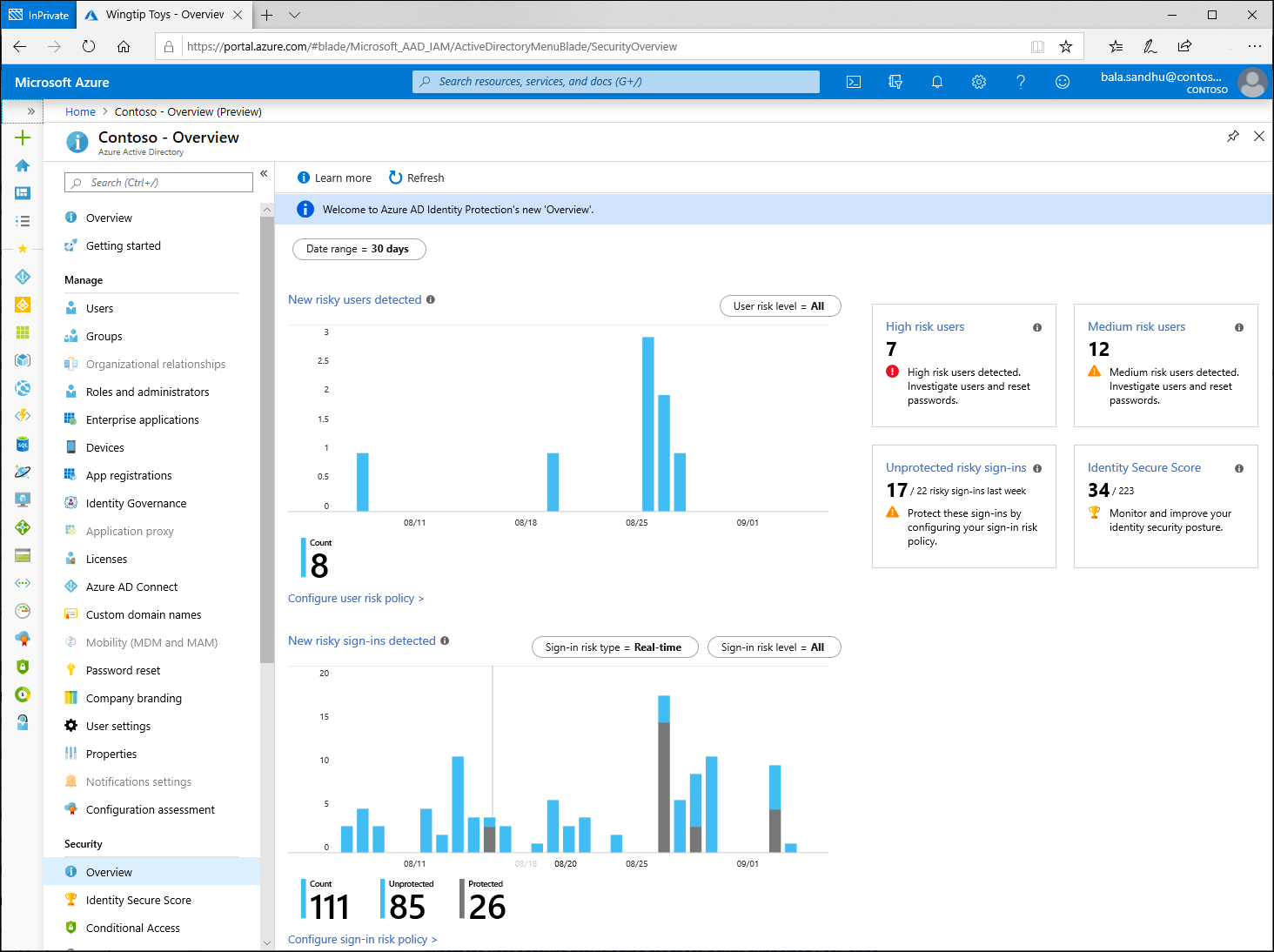
What are risk detections?
Risk detections in Microsoft Entra ID Protection include any identified suspicious actions related to user accounts in the directory. Risk detections (both user and sign-in linked) contribute to the overall user risk score that is found in the Risky Users report.
Identity Protection provides organizations access to powerful resources to see and respond quickly to these suspicious actions.
Identity Protection generates risk detections only when the correct credentials are used. If incorrect credentials are used on a sign-in, it does not represent risk of credential compromise.
Risk types and detection
Risk can be detected at the User and Sign-in level and two types of detection or calculation Real-time and Offline. Some risks are considered premium available to Microsoft Entra ID P2 customers only, while others are available to Free and Microsoft Entra ID P1 customers.
A sign-in risk represents the probability that a given authentication request isn’t the authorized identity owner. Risky activity can be detected for a user that isn’t linked to a specific malicious sign-in but to the user itself.
Real-time detections may not show up in reporting for 5 to 10 minutes. Offline detections may not show up in reporting for 48 hours.
Our system may detect that the risk event that contributed to the risk user risk score was either:
- A false positive
- The user risk was remediated by policy by either:
- Completing multifactor authentication
- Secure password change.
Our system will dismiss the risk state and a risk detail of “AI confirmed sign-in safe” will show and no longer contribute to the user’s overall risk.
Sign-in risk detections
Risk detection Detection type Type Atypical travel Offline Premium Anomalous Token Offline Premium Token Issuer Anomaly Offline Premium Malware linked IP address Offline Premium This detection has been deprecated. Suspicious browser Offline Premium Unfamiliar sign-in properties Real-time Premium Malicious IP address Offline Premium Suspicious inbox manipulation rules Offline Premium Password spray Offline Premium Impossible travel Offline Premium New country Offline Premium Activity from anonymous IP address Offline Premium Suspicious inbox forwarding Offline Premium Mass Access to Sensitive Files Offline Premium Verified threat actor IP Real-time Premium Additional risk detected Real-time or Offline Nonpremium Anonymous IP address Real-time Nonpremium Admin confirmed user compromised Offline Nonpremium Microsoft Entra threat intelligence Real-time or Offline Nonpremium User risk detections
Risk detection Detection type Type Possible attempt to access Primary Refresh Token (PRT) Offline Premium Anomalous user activity Offline Premium User reported suspicious activity Offline Premium Additional risk detected Real-time or Offline Nonpremium Leaked credentials Offline Nonpremium Microsoft Entra threat intelligence Offline Nonpremium Premium detections
The following premium detections are visible only to Microsoft Entra ID P2 customers.
Premium sign-in risk detections
Atypical travel
Calculated offline. This risk detection type identifies two sign-ins originating from geographically distant locations, where at least one of the locations may also be atypical for the user, given past behavior. The algorithm takes into account multiple factors including the time between the two sign-ins and the time it would have taken for the user to travel from the first location to the second. This risk may indicate that a different user is using the same credentials.
The algorithm ignores obvious “false positives” contributing to the impossible travel conditions, such as VPNs and locations regularly used by other users in the organization. The system has an initial learning period of the earliest of 14 days or 10 logins, during which it learns a new user’s sign-in behavior.
Anomalous token
Calculated offline. This detection indicates that there are abnormal characteristics in the token such as an unusual token lifetime or a token that is played from an unfamiliar location. This detection covers Session Tokens and Refresh Tokens.
Anomalous token is tuned to incur more noise than other detections at the same risk level. This tradeoff is chosen to increase the likelihood of detecting replayed tokens that may otherwise go unnoticed. Because this is a high noise detection, there’s a higher than normal chance that some of the sessions flagged by this detection are false positives. We recommend investigating the sessions flagged by this detection in the context of other sign-ins from the user. If the location, application, IP address, User Agent, or other characteristics are unexpected for the user, the tenant admin should consider this risk as an indicator of potential token replay.
Token issuer anomaly
Calculated offline. This risk detection indicates the SAML token issuer for the associated SAML token is potentially compromised. The claims included in the token are unusual or match known attacker patterns.
Malware linked IP address (deprecated)
Calculated offline. This risk detection type indicates sign-ins from IP addresses infected with malware that is known to actively communicate with a bot server. This detection matches the IP addresses of the user’s device against IP addresses that were in contact with a bot server while the bot server was active. This detection has been deprecated. Identity Protection no longer generates new “Malware linked IP address” detections. Customers who currently have “Malware linked IP address” detections in their tenant will still be able to view, remediate, or dismiss them until the 90-day detection retention time is reached.
Suspicious browser
Calculated offline. Suspicious browser detection indicates anomalous behavior based on suspicious sign-in activity across multiple tenants from different countries in the same browser.
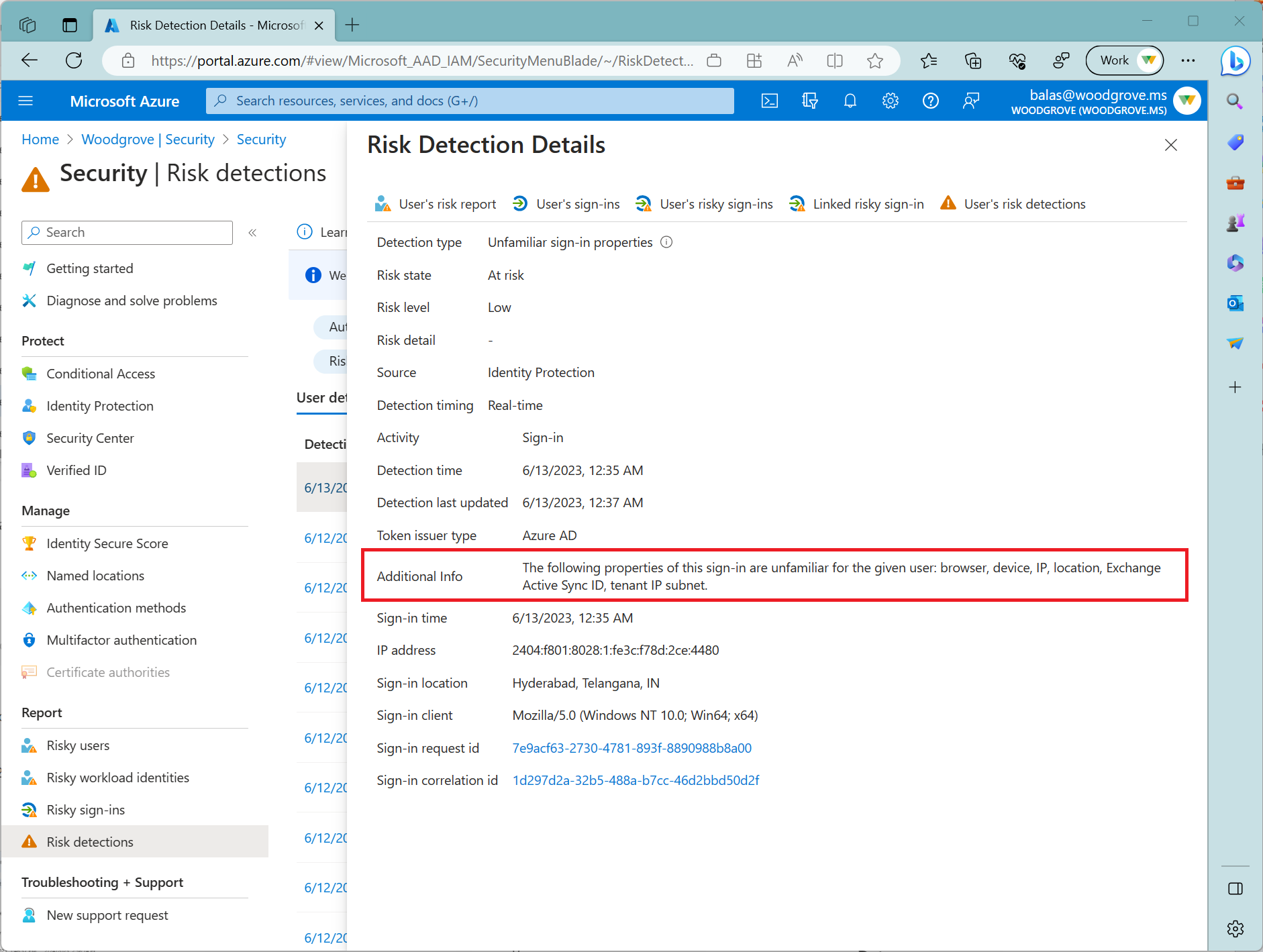
Unfamiliar sign-in properties
Calculated in real-time. This risk detection type considers past sign-in history to look for anomalous sign-ins. The system stores information about previous sign-ins, and triggers a risk detection when a sign-in occurs with properties that are unfamiliar to the user. These properties can include IP, ASN, location, device, browser, and tenant IP subnet. Newly created users are in “learning mode” period where the unfamiliar sign-in properties risk detection is turned off while our algorithms learn the user’s behavior. The learning mode duration is dynamic and depends on how much time it takes the algorithm to gather enough information about the user’s sign-in patterns. The minimum duration is five days. A user can go back into learning mode after a long period of inactivity.
We also run this detection for basic authentication (or legacy protocols). Because these protocols don’t have modern properties such as client ID, there’s limited telemetry to reduce false positives. We recommend our customers to move to modern authentication.
Unfamiliar sign-in properties can be detected on both interactive and non-interactive sign-ins. When this detection is detected on non-interactive sign-ins, it deserves increased scrutiny due to the risk of token replay attacks.
Selecting an unfamiliar sign-in properties risk allows you to see Additional Info showing you more detail about why this risk triggered. The following screenshot shows an example of these details.
Malicious IP address
Calculated offline. This detection indicates sign-in from a malicious IP address. An IP address is considered malicious based on high failure rates because of invalid credentials received from the IP address or other IP reputation sources.
Suspicious inbox manipulation rules
Calculated offline. This detection is discovered using information provided by Microsoft Defender for Cloud Apps. This detection looks at your environment and triggers alerts when suspicious rules that delete or move messages or folders are set on a user’s inbox. This detection may indicate: a user’s account is compromised, messages are being intentionally hidden, and the mailbox is being used to distribute spam or malware in your organization.
Password spray
Calculated offline. A password spray attack is where multiple usernames are attacked using common passwords in a unified brute force manner to gain unauthorized access. This risk detection is triggered when a password spray attack has been successfully performed. For example, the attacker is successfully authenticated, in the detected instance.
Impossible travel
Calculated offline. This detection is discovered using information provided by Microsoft Defender for Cloud Apps. This detection identifies user activities (is a single or multiple sessions) originating from geographically distant locations within a time period shorter than the time it takes to travel from the first location to the second. This risk may indicate that a different user is using the same credentials.
New country
Calculated offline. This detection is discovered using information provided by Microsoft Defender for Cloud Apps. This detection considers past activity locations to determine new and infrequent locations. The anomaly detection engine stores information about previous locations used by users in the organization.
Activity from anonymous IP address
Calculated offline. This detection is discovered using information provided by Microsoft Defender for Cloud Apps. This detection identifies that users were active from an IP address that has been identified as an anonymous proxy IP address.
Suspicious inbox forwarding
Calculated offline. This detection is discovered using information provided by Microsoft Defender for Cloud Apps. This detection looks for suspicious email forwarding rules, for example, if a user created an inbox rule that forwards a copy of all emails to an external address.
Mass access to sensitive files
Calculated offline. This detection is discovered using information provided by Microsoft Defender for Cloud Apps. This detection looks at your environment and triggers alerts when users access multiple files from Microsoft SharePoint or Microsoft OneDrive. An alert is triggered only if the number of accessed files is uncommon for the user and the files might contain sensitive information
Verified threat actor IP
Calculated in real-time. This risk detection type indicates sign-in activity that is consistent with known IP addresses associated with nation state actors or cyber crime groups, based on Microsoft Threat Intelligence Center (MSTIC).
Premium user risk detections
Possible attempt to access Primary Refresh Token (PRT)
Calculated offline. This risk detection type is discovered using information provided by Microsoft Defender for Endpoint (MDE). A Primary Refresh Token (PRT) is a key artifact of Microsoft Entra authentication on Windows 10, Windows Server 2016, and later versions, iOS, and Android devices. A PRT is a JSON Web Token (JWT) that’s specially issued to Microsoft first-party token brokers to enable single sign-on (SSO) across the applications used on those devices. Attackers can attempt to access this resource to move laterally into an organization or perform credential theft. This detection moves users to high risk and only fires in organizations that have deployed MDE. This detection is low-volume and is seen infrequently in most organizations. When this detection appears it’s high risk, and users should be remediated.
Anomalous user activity
Calculated offline. This risk detection baselines normal administrative user behavior in Microsoft Entra ID, and spots anomalous patterns of behavior like suspicious changes to the directory. The detection is triggered against the administrator making the change or the object that was changed.
User reported suspicious activity
Calculated offline. This risk detection is reported when a user denies a multifactor authentication (MFA) prompt and reports it as suspicious activity. An MFA prompt not initiated by a user may mean their credentials are compromised.
Nonpremium detections
Customers without Microsoft Entra ID P2 licenses receive detections titled “additional risk detected” without the detailed information regarding the detection that customers with P2 licenses do.
Nonpremium sign-in risk detections
Additional risk detected (sign-in)
Calculated in real-time or offline. This detection indicates that one of the premium detections was detected. Since the premium detections are visible only to Microsoft Entra ID P2 customers, they’re titled “additional risk detected” for customers without Microsoft Entra ID P2 licenses.
Anonymous IP address
Calculated in real-time. This risk detection type indicates sign-ins from an anonymous IP address (for example, Tor browser or anonymous VPN). These IP addresses are typically used by actors who want to hide their sign-in information (IP address, location, device, and so on) for potentially malicious intent.
Admin confirmed user compromised
Calculated offline. This detection indicates an admin has selected ‘Confirm user compromised’ in the Risky users UI or using riskyUsers API. To see which admin has confirmed this user compromised, check the user’s risk history (via UI or API).
Microsoft Entra threat intelligence (sign-in)
Calculated in real-time or offline. This risk detection type indicates user activity that is unusual for the user or consistent with known attack patterns. This detection is based on Microsoft’s internal and external threat intelligence sources.
Nonpremium user risk detections
Additional risk detected (user)
Calculated in real-time or offline. This detection indicates that one of the premium detections was detected. Since the premium detections are visible only to Microsoft Entra ID P2 customers, they’re titled “additional risk detected” for customers without Microsoft Entra ID P2 licenses.
Leaked credentials
Calculated offline. This risk detection type indicates that the user’s valid credentials have been leaked. When cybercriminals compromise valid passwords of legitimate users, they often share these gathered credentials. This sharing is typically done by posting publicly on the dark web, paste sites, or by trading and selling the credentials on the black market. When the Microsoft leaked credentials service acquires user credentials from the dark web, paste sites, or other sources, they’re checked against Microsoft Entra users’ current valid credentials to find valid matches. For more information about leaked credentials, see Common questions.
Microsoft Entra threat intelligence (user)
Calculated offline. This risk detection type indicates user activity that is unusual for the user or consistent with known attack patterns. This detection is based on Microsoft’s internal and external threat intelligence sources.
Common questions
Risk levels
Identity Protection categorizes risk into three tiers: low, medium, and high. When configuring Identity protection policies, you can also configure it to trigger upon No risk level. No Risk means there’s no active indication that the user’s identity has been compromised.
Microsoft doesn’t provide specific details about how risk is calculated. Each level of risk brings higher confidence that the user or sign-in is compromised. For example, something like one instance of unfamiliar sign-in properties for a user might not be as threatening as leaked credentials for another user.
Password hash synchronization
Risk detections like leaked credentials require the presence of password hashes for detection to occur. For more information about password hash synchronization, see the article, Implement password hash synchronization with Microsoft Entra Connect Sync.
Why are there risk detections generated for disabled user accounts?
Disabled user accounts can be re-enabled. If the credentials of a disabled account are compromised, and the account gets re-enabled, bad actors might use those credentials to gain access. Identity Protection generates risk detections for suspicious activities against disabled user accounts to alert customers about potential account compromise. If an account is no longer in use and wont be re-enabled, customers should consider deleting it to prevent compromise. No risk detections are generated for deleted accounts.
Where does Microsoft find leaked credentials?
Microsoft finds leaked credentials in various places, including:
- Public paste sites such as pastebin.com and paste.ca where bad actors typically post such material. This location is most bad actors’ first stop on their hunt to find stolen credentials.
- Law enforcement agencies.
- Other groups at Microsoft doing dark web research.
Why am I not seeing any leaked credentials?
Leaked credentials are processed anytime Microsoft finds a new, publicly available batch. Because of the sensitive nature, the leaked credentials are deleted shortly after processing. Only new leaked credentials found after you enable password hash synchronization (PHS) are processed against your tenant. Verifying against previously found credential pairs isn’t done.
I haven’t seen any leaked credential risk events for quite some time
If you haven’t seen any leaked credential risk events, it is because of the following reasons:
- You don’t have PHS enabled for your tenant.
- Microsoft has not found any leaked credential pairs that match your users.
How often does Microsoft process new credentials?
Credentials are processed immediately after they have been found, normally in multiple batches per day.
Locations
Location in risk detections is determined using IP address lookup.
Next steps
- Policies available to mitigate risks
- Investigate risk
- Remediate and unblock users
- Security overview
How people hide their IPs and why it can be useful to detect them?
Almost anywhere you go today on the Internet, you leave some sort of a trail behind. Whether it’s your online activities, location, or something else, unless you are very good at covering your tracks, it will be possible to find enough information about you.
One such trail is your Internet Protocol or IP address. Every computer, router, or another device on the network has an IP address assigned to them as an identifying number. The IP address itself is connected to the location, which is how we typically know if someone is using a laptop in the US or France for example.
But IP location can go even deeper than the country-level. Today, IP geolocation services are capable of very accurately pinpoint your location to the Zip code and according to the Transparency Report, the global IP geolocation market will reach $4.5 billion in value by 2027.
Depending on how you look at it, this can be a good or a bad thing. We are going to show you the various ways people use to hide their real IPs, why they do it, as well as why you need to detect them. Finally we will show you how IPInfo can help with that.
Why Do People Hide Their IP?
There are many reasons why people are hiding their IP addresses.
For instance, someone hiding their IP might be doing it to hide their identity from hackers trying to track their actions and reveal as little information about themselves as possible.
Or, they want to protect themselves from censoring governments who are spying on what they say and do online.
They might also want to prevent their Internet Service Providers (ISP) or search engines from keeping a log of their Internet browsing activities.
Some hide their IP to bypass geographically blocked content and websites or restrictions put up in their workplace or school.
Others want to be able to access video streaming services like Netflix or Hulu and watch the latest episodes of their favorite TV shows wherever they are.
People living in authoritarian countries like Iran, China, Russia, etc. hide their IPs to avoid state censorship and access blocked sites and content in their countries (hear the other side, so to speak).
On the other hand, that doesn’t mean that people in democratic countries like the US or UK are exempt from being spied upon by their governments. Anonymizing IP can also be useful for anyone living under the government with powerful electronic eavesdropping capabilities.
For instance, people in many western countries are under constant monitoring under 14EY. This is a coalition of countries, including United States, United Kingdom, Canada, Australia, New Zealand, Germany, France, Holland, Belgium, Italy, Spain, Denmark, Sweden and Norway that not only monitor their own citizens, but also trade information about the other members’ citizens back and forth with the rest of the “eyes”.
Whatever the reason, people will try to mask their IP address. If you have a website where it’s important for you to know exactly how they are doing that.
How Do People Hide Their IPs?
There are several ways to hide your real IP address. Here, we will focus on the three most widely used.
1. Using a VPN Software
An estimated worldwide VPN market value in 2019 was $23.6bn and it will be $27.1bn in 2020, according to Go-Globe’s The State of VPN Usage — Statistics and Trends. According to their figures, the worldwide VPN market grows by about 4 billion dollars every year.
A VPN, or Virtual Private Network, acts as a middleman between your computer and the destination server.
It serves two purposes. One is to encrypt your connection to the Internet. The other is to hide your real IP address.
To hide your IP address with a VPN all you need is to download a VPN of your choosing (such as NordVPN or ExpressVPN), log in to it and turn it on. Once on, the VPN should hide your IP and your location.
What happens here and the way that VPN hides your IP is that your traffic takes a slight detour through the VPN server. That way, your traffic reaches the websites you want to visit (like Netflix for example), not through your real IP, but the VPN’s IP.
2. With a Proxy Server
Another way to hide your IP address is to use a proxy server. In essence, what the proxy does is forward the client’s or network’s requests and receives and delivers server responses.
People often confuse proxy with VPN servers, believing them to do the same thing. This is not the case.
Proxy servers don’t encrypt the traffic, meaning that they won’t be able to hide your IP address from someone who intercepts traffic on the way from the device to the proxy server.
That’s why proxies tend to be less reliable than VPN servers when it comes to online privacy.
There are three types of proxy servers, with varying degrees of protection:
- Transparent, which doesn’t hide your IP or the fact that you are using a proxy server.
- Anonymous, which hides the IP, but not that you use a proxy.
- Elite, which hides both your IP address and your use of a proxy server.
3. Using Tor
Tor, or The Onion Router, is an open-source and free network of server nodes run by volunteers that hides your identity behind layers of proxy (like an onion, hence the name).
When using the Tor browser, it first connects to a random publicly listed entry node. Next, the traffic goes through a randomly chosen middle node. Finally, the traffic goes through the third and final node.
As each node in the path will only know the IP of the nodes immediately before and after it, it’s almost impossible to figure out the original (your) IP address, even if someone could intercept the traffic from the final node to the destination server.
This makes Tor excellent at hiding your real IP address, but all this bouncing from node to node has its price. The tradeoff comes in speed as with Tor, the traffic takes longer to complete the journey.
How to Detect if Your Visitors are Using a VPN, Proxy, or Tor?
Although there are plenty of legitimate reasons why someone would want to hide their IP address, there are many of those that aren’t so legitimate.
Sites like Netflix, for example, block VPNs (they have a list of known VPN IP addresses) to protect copyright holders and make sure they receive money for people watching their movies or TV shows.
Another reason why you might want to detect if someone is hiding their IP some other way is to combat spam. Let’s say someone is posting spam on your website. If you try to block their IP, they can come back with another one since they are behind a proxy. In that case, your best course of action might be to block a range of IPs for that proxy.
Click fraud is another ever-present threat that online business owners have to deal with. It is estimated that fake PPC clicks cost companies $60 million per year and click fraud traffic is growing at an alarming rate (50% per year).
Finally, you also want to know where your visitors are coming from to fight off hackers.
Let’s say your website caters to the US-based audience and perhaps some UK and Europe. But then, looking at the analytics, you notice that your second-largest audience source is China and your content in no way caters to that particular audience. Knowing that China has the largest population of hackers in the world, this can be worrying.
All that said, how do you detect the use of a VPN, proxy server, or Tor?
There are several ways to do that, but they are either overly complicated or they can only detect one of them. For example, we already mentioned how Netflix has a list of known VPN IPs they block if someone tries to connect through.
IPInfo provides a much simpler solution with its Privacy Detection API. This API detects different methods that your visitors might be using to hide their real IPs, including VPN, proxy, Tor, or hosting.
The Privacy Detection API performs full Internet-wide scans to detect up to 10 million active VPNs. This is then combined with data on Tor exit nodes, HTTP and SOCKS proxies and IPInfo’s own IP type detection to find the IP ranges belonging to their user’s hosting providers.
IPinfo is a comprehensive IP address data and API provider with flexible pricing plans to meet your business needs. We handle billions of API requests per month, serving data like IP geolocation, ASN, mobile carrier, privacy detection, and hosted domains. Sign up for a free account or contact our data experts to learn more.
The link has been copied!