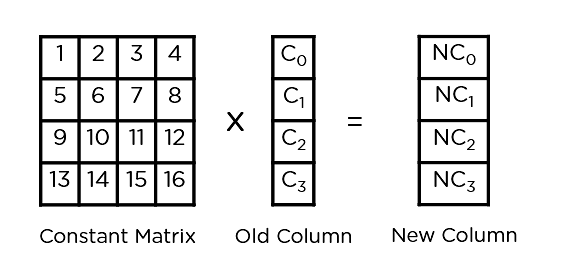Advanced Encryption Standard
Because of its key length options, AES encryption remains the best choice for securing communications. The time required to crack an encryption algorithm is directly related to the length of the key used, i.e., 128-bit, 192-bit, and 256-bit.
Advanced Encryption Standard (AES)
Morris J. Dworkin , Elaine B. Barker , James R. Nechvatal , James Foti , Lawrence E. Bassham , E. Roback , James F. Dray Jr.
Abstract
The Advanced Encryption Standard (AES) specifies a FIPS-approved cryptographic algorithm that can be used to protect electronic data. The AES algorithm is a symmetric block cipher that can encrypt (encipher) and decrypt (decipher) information. Encryption converts data to an unintelligible form called ciphertext; decrypting the ciphertext converts the data back into its original form, called plaintext. The AES algorithm is capable of using cryptographic keys of 128, 192, and 256 bits to encrypt and decrypt data in blocks of 128 bits.
Advanced Encryption Standard
The more popular and widely adopted symmetric encryption algorithm likely to be encountered nowadays is the Advanced Encryption Standard (AES). It is found at least six time faster than triple DES.
A replacement for DES was needed as its key size was too small. With increasing computing power, it was considered vulnerable against exhaustive key search attack. Triple DES was designed to overcome this drawback but it was found slow.
The features of AES are as follows −
- Symmetric key symmetric block cipher
- 128-bit data, 128/192/256-bit keys
- Stronger and faster than Triple-DES
- Provide full specification and design details
- Software implementable in C and Java
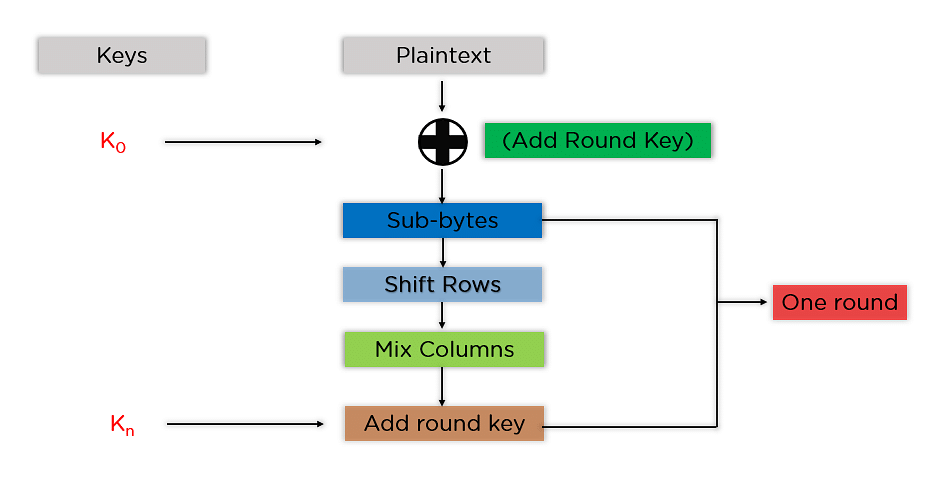
Operation of AES
AES is an iterative rather than Feistel cipher. It is based on ‘substitution–permutation network’. It comprises of a series of linked operations, some of which involve replacing inputs by specific outputs (substitutions) and others involve shuffling bits around (permutations).
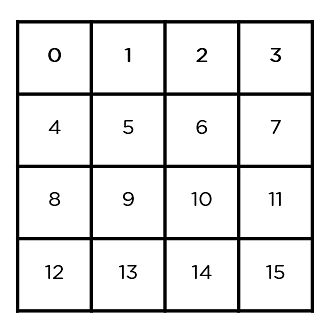
Interestingly, AES performs all its computations on bytes rather than bits. Hence, AES treats the 128 bits of a plaintext block as 16 bytes. These 16 bytes are arranged in four columns and four rows for processing as a matrix −
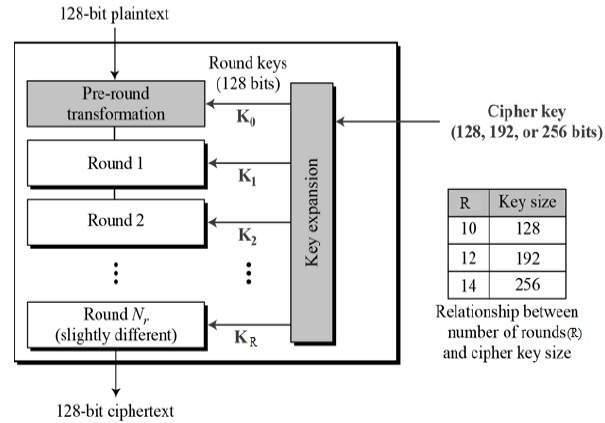
Unlike DES, the number of rounds in AES is variable and depends on the length of the key. AES uses 10 rounds for 128-bit keys, 12 rounds for 192-bit keys and 14 rounds for 256-bit keys. Each of these rounds uses a different 128-bit round key, which is calculated from the original AES key.
The schematic of AES structure is given in the following illustration −
Encryption Process
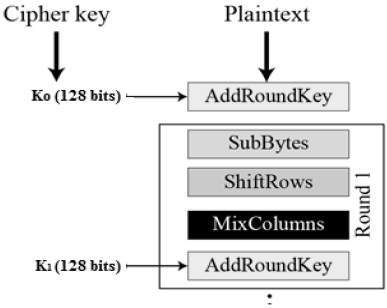
Here, we restrict to description of a typical round of AES encryption. Each round comprise of four sub-processes. The first round process is depicted below −
Byte Substitution (SubBytes)
The 16 input bytes are substituted by looking up a fixed table (S-box) given in design. The result is in a matrix of four rows and four columns.
Shiftrows
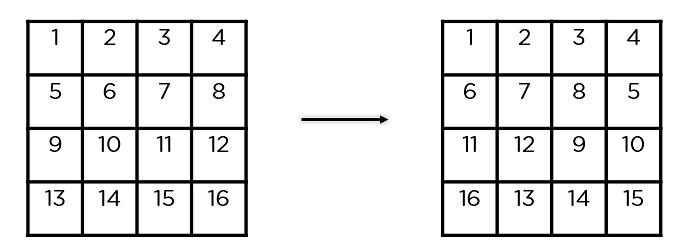
Each of the four rows of the matrix is shifted to the left. Any entries that ‘fall off’ are re-inserted on the right side of row. Shift is carried out as follows −
- First row is not shifted.
- Second row is shifted one (byte) position to the left.
- Third row is shifted two positions to the left.
- Fourth row is shifted three positions to the left.
- The result is a new matrix consisting of the same 16 bytes but shifted with respect to each other.
MixColumns
Each column of four bytes is now transformed using a special mathematical function. This function takes as input the four bytes of one column and outputs four completely new bytes, which replace the original column. The result is another new matrix consisting of 16 new bytes. It should be noted that this step is not performed in the last round.
Addroundkey
The 16 bytes of the matrix are now considered as 128 bits and are XORed to the 128 bits of the round key. If this is the last round then the output is the ciphertext. Otherwise, the resulting 128 bits are interpreted as 16 bytes and we begin another similar round.
Decryption Process
The process of decryption of an AES ciphertext is similar to the encryption process in the reverse order. Each round consists of the four processes conducted in the reverse order −
- Add round key
- Mix columns
- Shift rows
- Byte substitution
Since sub-processes in each round are in reverse manner, unlike for a Feistel Cipher, the encryption and decryption algorithms needs to be separately implemented, although they are very closely related.
AES Analysis
In present day cryptography, AES is widely adopted and supported in both hardware and software. Till date, no practical cryptanalytic attacks against AES has been discovered. Additionally, AES has built-in flexibility of key length, which allows a degree of ‘future-proofing’ against progress in the ability to perform exhaustive key searches.
However, just as for DES, the AES security is assured only if it is correctly implemented and good key management is employed.
Kickstart Your Career
Get certified by completing the course
What Is AES Encryption and How Does It Work?
Encryption has found a place in today’s digital world, by cultivating a culture of security and privacy. When the AES Encryption algorithm succeeded the Data Encryption Standard as the global standard for encryption algorithms in 2001, it fixed many shortcomings of its predecessor. It was seen as the future for encryption in daily life applications. So far, the Advanced Encryption Standard has achieved the targets placed during its inception. And it has a long way to grow.
Become an Expert in the Cyber Security Field
Post Graduate Program In Cyber Security Explore Program
Why Was the AES Encryption Algorithm necessary?
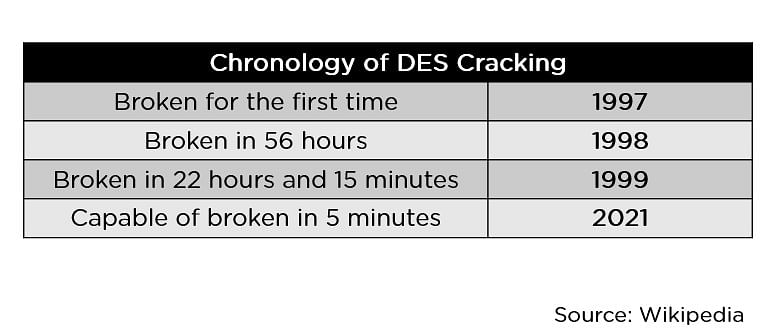
When the Data Encryption Standard algorithm, also known as the DES algorithm, was formed and standardized, it made sense for that generation of computers. Going by today’s computational standards, breaking into the DES algorithm became easier and faster with every year, as seen in the image below.
A more robust algorithm was the need of the hour, with longer key sizes and stronger ciphers to break into. They created the triple DES to fix this problem, but it never became mainstream because of its relatively slower pace. Thus, the Advanced Encryption Standard came into existence to overcome this drawback.
What is the Advanced Encryption Standard?
The AES Encryption algorithm (also known as the Rijndael algorithm) is a symmetric block cipher algorithm with a block/chunk size of 128 bits. It converts these individual blocks using keys of 128, 192, and 256 bits. Once it encrypts these blocks, it joins them together to form the ciphertext.
It is based on a substitution-permutation network, also known as an SP network. It consists of a series of linked operations, including replacing inputs with specific outputs (substitutions) and others involving bit shuffling (permutations).
In this tutorial, you will go through some of the standout features that AES offers as a globally standardized encryption algorithm.
What are the Features of AES?
- SP Network: It works on an SP network structure rather than a Feistel cipher structure, as seen in the case of the DES algorithm.
- Key Expansion: It takes a single key up during the first stage, which is later expanded to multiple keys used in individual rounds.
- Byte Data: The AES encryption algorithm does operations on byte data instead of bit data. So it treats the 128-bit block size as 16 bytes during the encryption procedure.
- Key Length: The number of rounds to be carried out depends on the length of the key being used to encrypt data. The 128-bit key size has ten rounds, the 192-bit key size has 12 rounds, and the 256-bit key size has 14 rounds.
Clear CompTIA, CEH, and CISSP Certifications!
Cyber Security Expert Master’s Program Explore Program
How Does AES Work?
To understand the way AES works, you first need to learn how it transmits information between multiple steps. Since a single block is 16 bytes, a 4×4 matrix holds the data in a single block, with each cell holding a single byte of information.
The matrix shown in the image above is known as a state array. Similarly, the key being used initially is expanded into (n+1) keys, with n being the number of rounds to be followed in the encryption process. So for a 128-bit key, the number of rounds is 16, with no. of keys to be generated being 10+1, which is a total of 11 keys.
Steps to be followed in AES
The mentioned steps are to be followed for every block sequentially. Upon successfully encrypting the individual blocks, it joins them together to form the final ciphertext. The steps are as follows:
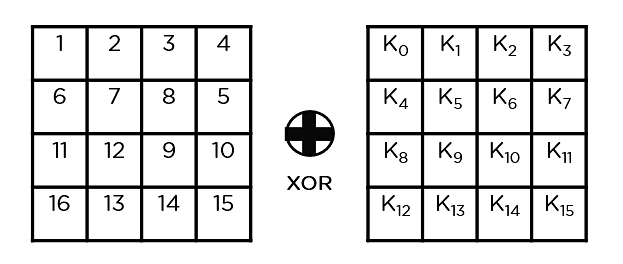
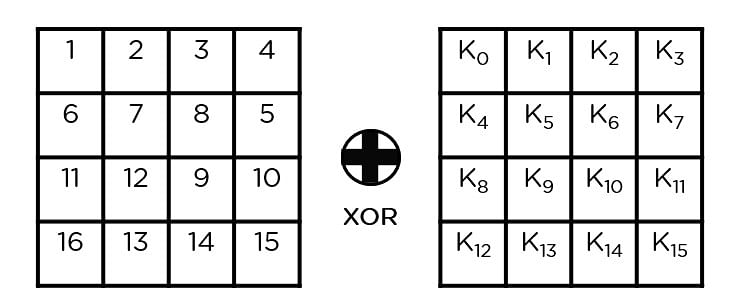
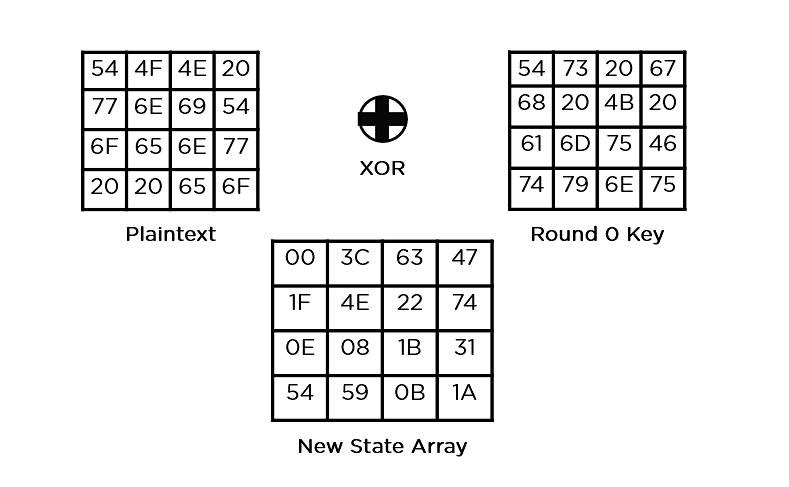
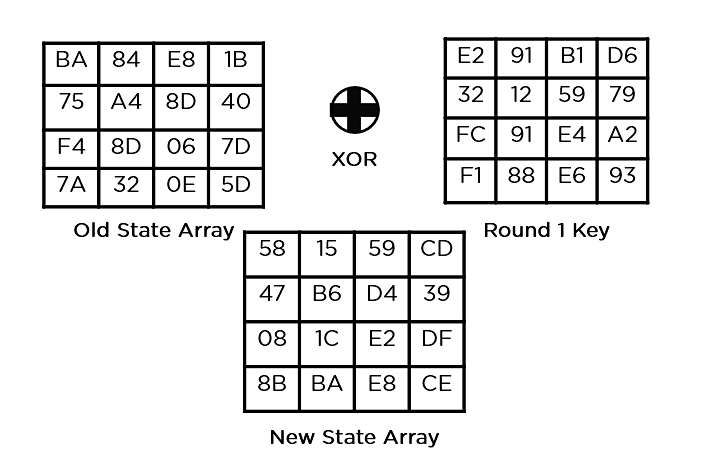
- Add Round Key: You pass the block data stored in the state array through an XOR function with the first key generated (K0). It passes the resultant state array on as input to the next step.
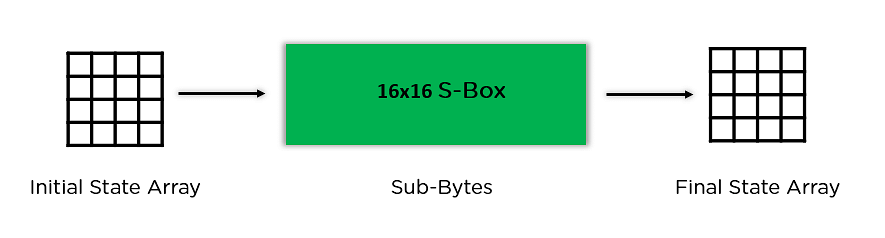
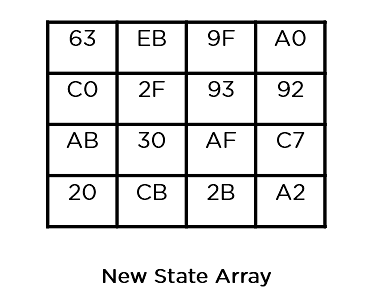
- Sub-Bytes: In this step, it converts each byte of the state array into hexadecimal, divided into two equal parts. These parts are the rows and columns, mapped with a substitution box (S-Box) to generate new values for the final state array.
Sneak Peek into Caltech’s Cyber Security Bootcamp
Free Webinar | Sept 21, Thursday | 9 PM IST Register Now!
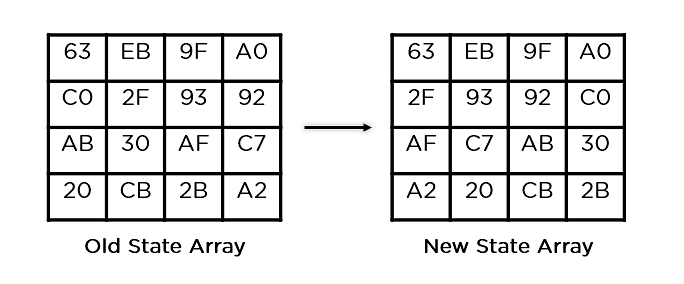
- Shift Rows: It swaps the row elements among each other. It skips the first row. It shifts the elements in the second row, one position to the left. It also shifts the elements from the third row two consecutive positions to the left, and it shifts the last row three positions to the left.
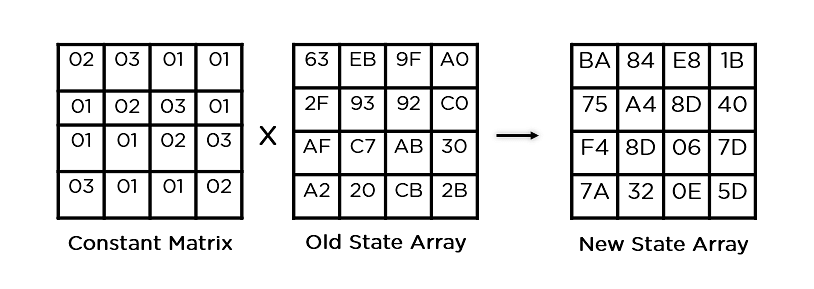
- Mix Columns: It multiplies a constant matrix with each column in the state array to get a new column for the subsequent state array. Once all the columns are multiplied with the same constant matrix, you get your state array for the next step. This particular step is not to be done in the last round.
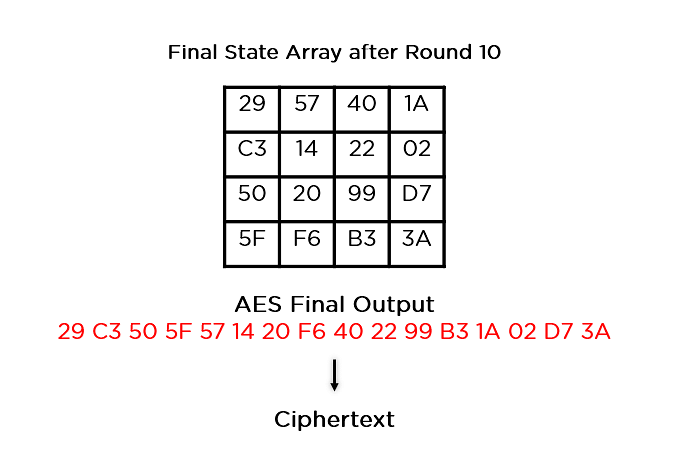
- Add Round Key: The respective key for the round is XOR’d with the state array is obtained in the previous step. If this is the last round, the resultant state array becomes the ciphertext for the specific block; else, it passes as the new state array input for the next round.
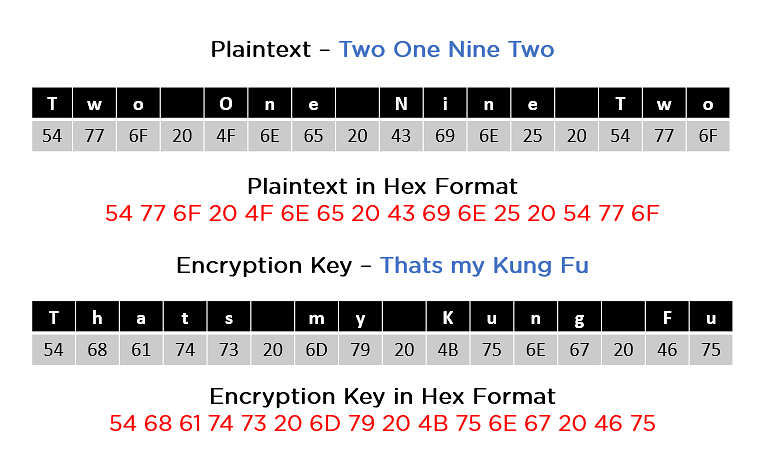
Now that you understand the basic steps needed to go through the encryption procedure, understand this example to follow along.
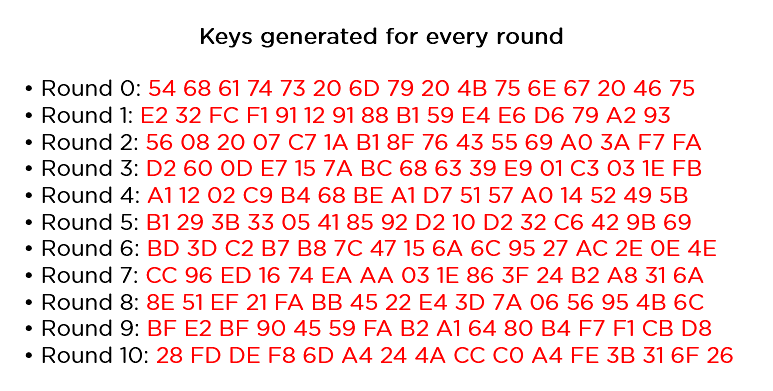
As you can see in the image above, the plaintext and encryption convert keys to hex format before the operations begin. Accordingly, you can generate the keys for the next ten rounds, as you can see below.
You need to follow the same steps explained above, sequentially extracting the state array and passing it off as input to the next round. The steps are as follows:
Clear CompTIA, CEH, and CISSP Certifications!
Cyber Security Expert Master’s Program Explore Program
- Add Round Key:
- Sub-Bytes: It passes the elements through a 16×16 S-Box to get a completely new state array.
This state array is now the final ciphertext for this particular round. This becomes the input for the next round. Depending on the key length, you repeat the above steps until you complete round 10, after which you receive the final ciphertext.
Now that you understand how AES works, go through some of the applications of this encryption algorithm.
Clear CompTIA, CEH, and CISSP Certifications!
Cyber Security Expert Master’s Program Explore Program
What Are the Applications of AES?
The applications of the AES Encryption algorithm are as follows:
- Wireless Security: Wireless networks are secured using the Advanced Encryption Standard to authenticate routers and clients. WiFi networks have firmware software and complete security systems based on this algorithm and are now in everyday use.
- Encrypted Browsing: AES plays a huge role in securing website server authentication from both client and server end. With both symmetric and asymmetric encryption being used, this algorithm helps in SSL/TLS encryption protocols to always browse with the utmost security and privacy.
Now that you learned about the applications of AES encryption, take a look at its upgrades over its predecessor, the DES encryption algorithm.
Differences Between AES & DES
DES Algorithm
AES Algorithm
Key Length – 56 bits
Key Length – 128, 192, 256 bits
Block Size – 64 bits
Block size – 128 bits
Fixed no. of rounds
No. of rounds dependent on key length
Slower and less secure
Faster and more secure
FAQs
1. Is AES encryption secure?
AES encryption is secure; however, its security varies according to its variants. For example, using brute-force methods, the 256-bit is virtually impenetrable, while the 52-bit DES key can be cracked in less than a day.
2.Is AES the best encryption method?
Because of its key length options, AES encryption remains the best choice for securing communications. The time required to crack an encryption algorithm is directly related to the length of the key used, i.e., 128-bit, 192-bit, and 256-bit.
3. What is AES encryption used for?
AES is implemented in hardware and software worldwide to encrypt sensitive data. It is a symmetric block cipher essential for government computer security, electronic data protection, and cybersecurity.
4. Which is better: RSA or AES?
RSA is considerably slower and more computationally intensive than AES. RSA has to deal with large numbers and calculations, which makes it slower. AES is considered secure against analysis with quantum computers and is generally used by various organizations.
5. Is AES free to use?
AES is available for free, and anyone can use it. Though several countries apply export restrictions, it is an open standard that is free to use for any private, public, non-commercial, or commercial use.
6. What is AES?
Advanced Encryption Standard is a symmetric block cipher chosen by the US government. It converts the individual blocks using different keys. It is one of the best encryption protocols available, letting anyone enjoy their daily online activities without disruption.
How Can Simplilearn Help You?
With this, you have seen the impact AES Encryption has on the global stage, with many systems needing a secure channel of authentication as DES collapsed. With many bases to cover in cybersecurity, cryptography is one of the most crucial aspects, even though several other topics are essential to excel as a cybersecurity expert.
Simplilearn offers a “Cybersecurity Expert” course designed to equip you with all the skills necessary to start or promote your career in cybersecurity. It doesn’t have any academic pre-requirements, and the introductory module will prepare beginners for the course ahead. Training for highly sought-after certifications like CompTIA Security+, CEH, CISM, and CISSP is at the forefront of this course, preparing you for the best jobs being offered in the industry.
Transform your cybersecurity career and become an industry-ready professional by enrolling in our Advanced Executive Program in Cybersecurity today.
Conclusion
This tutorial explores the need for AES Encryption, its origin and process of encryption, all the way up to its applications, and a direct comparison with the DES algorithm. Hope this tutorial has been of value to you.
If you are looking to learn further on encryptions, cryptography and other fundamental concepts and skills in cybersecurity, Simplilearn’s Advanced Executive Program In Cyber Security program should be a great fit for you. This program covers all the fundamental and advanced aspects of cybersecurity and provides you the right job-ready training you need to become a world-class cybersecurity expert today. Explore the program today.
Do you have any questions for us regarding this AES encryption tutorial? Please don’t hesitate to mention them in the comment section of this tutorial, and we’d be happy to have our experts answer them for you.
About the Author
Baivab Kumar Jena
Baivab Kumar Jena is a computer science engineering graduate, he is well versed in multiple coding languages such as C/C++, Java, and Python.
Recommended Programs
Advanced Executive Program in Cybersecurity